
Any meaningful endeavor is always accompanied by risk, and running a business is no exception. 40 years ago, the only industries that actively managed risk were banking and manufacturing. But in the last two decades, the nature, speed, and sophistication of both internal and external threats have increased dramatically.
Much of this can be credited to ever-emerging new technologies. While technological innovation is undoubtedly required to keeping pace, it presents a common dilemma. With every step forward, we have the potential to leave behind a wake of exploitable loopholes. Put otherwise, new technology offers early adopters a competitive advantage, but also rise to emerging strategic, reputational, and financial risks that – more often than not – require rapid response.
Consequently, businesses across all sectors are adopting risk management strategies in one form or another. In order to prepare you for the inherent uncertainty faced by today’s corporations, we present a complete guide to Enterprise Risk Management. Keep on reading to find out what Enterprise Risk Management is and how to start implementing the associated best practices in your company.
1. What is Enterprise Risk Management?
First, let’s define enterprise risk. Enterprise risk is the contrast between the outcome of a corporation’s business strategy and its goals. As such, this term addresses all internal and external factors that can negatively impact a business’ ability to meet its objectives.
Now, enter “enterprise risk management” – a set of methods aimed at preventing such types of suboptimal performance from occurring and, by extension, securing new business opportunities. As such, identifying critical risks in your company, prioritizing them, and developing a set of procedures to quickly mitigate incidents that result from such risks, all lie at the core of modern enterprise risk management.
Consequently, the ultimate goal is to enable businesses to leverage these inherent uncertainties and risks to their advantage. This aim is realized by way of modern technologies, such as AI and cloud computing, which help corporations to not only analyze substantial streams of information in real-time, but to also find hidden connections between unrelated events. For example, these analytical powers can be used to both assess the quality of strategic decisions and predict their long-term repercussions.
Today, these risk management practices largely account for why large enterprises value data above all other assets. It allows the big players to avoid substandard results and capitalize on risks that often intimidate less prepared competitors.
2. The History of Risk Management
Academic studies on corporate risk emerged in the 1950s, in the wake of booming business growth post World War 2. This is right around the time when enterprise risk management methods began taking root, and large companies began enforcing self-insurance policies to guard themselves from losses due to threats. Take liquid financial reserves as an example. These reserves were established from that era to aid in smoothly recovering from erratic and volatile markets.
As time went on, universal risk management strategies further evolved to encompass internal threats, and were often based on precedents set by or within other companies/industries. This risk management revolution was ultimately induced in the 1970s by the increased instability of the financial world, alongside its resultant inflation and price fluctuations. This industry transformation was also marked by the increased use of forward and futures contracts, which helped guard businesses from the inherent risks associated with this new financial reality.
With respect to business strategies, new initiatives became riskier due to the imperative of “do or die” executive decisions in increasingly crowded markets. History reveals that such tactics are only effective when their execution is carefully planned. Thus, this shift in corporate strategy paved the way for the rapid development of strategic risk management policies and procedures. Not to mention, the sheer number of organizations that faced catastrophic failure, on its own, served as testimony to the intrinsic value of risk management.
As the early 2000s began, the role of governments thus expanded to establishing strict enterprise risk management legislation, which enforced companies to strategically prevent and/or mitigate threats. On of the most landmark pieces of legislation was the Sarbanes-Oxley Act. These new laws created the need for new risk-management framework, such as COSO and ISO 31000, which were aimed at addressing the unique needs of large businesses.
The rest is history, leaving us with the modern enterprise risk management as we see it now. Today, this practice has been reworked, fine-tuned, and carefully calibrated for applications of a much larger corporate scale.
3. Goals of Enterprise Risk Management
- Risk Identification and Evaluation
Risk management involves identifying both external and internal risks that are critical to a business, and prioritizing them based on their potential impact on performance. As such, risk identification and evaluation provide insight as to where these risks originate from, thereby enabling a more proactive, top-to-bottom mitigation approach/strategy.
- Threat Prevention and Remediation
Critical risks often negatively impact a business’ operational efficiency and financial prosperity. In order to prevent these undesirable outcomes, organizations need to thoroughly plan and carefully execute their threat prevention and remediation procedures. By developing and closely adhering to these policies and practices, corporations will be able to effectively address risks/threats in a faster, more efficient manner.
- Efficient Use of Resources
Risk management illuminates how businesses can most efficiently leverage their resources. In doing so, they stand to achieve greater operational efficiency, productivity, and a considerable increase in revenue. For example, eliminating any redundant processes and potential for communication breakdowns not only improves the tools and overall framework used, it also illuminates how organizations can best allocate resources for managing and reporting risk.
- Improving the Quality of Internal Communication
Speaking of communication breakdowns, enterprise risk management requires full cooperation between each level of a given organization – from the field workers all the way up to the executives. ERM thus gives rise to a more transparent environment with fully-integrated communication. These enhancements foster a cohesive workplace that builds trust between employees. In gist, improving internal communications mitigates risk associated with integrity-compromising internal conflict.
- Continuous Improvement
A company’s “risk landscape” is highly dynamic, so it’s important to constantly be on the lookout for ways to improve your risk management approaches. No effective risk management strategy is static. It must constantly adapt to the ebbs and flows of market demands and financial imperatives in order to continuously improve. To achieve this goal, businesses must regularly conduct internal audits. Such rigorous auditing reveals any dormant or developing issues that can be addressed via risk management policies.
- Inspire Confidence in Stakeholders
Stakeholders take a personal/financial interest in your company and, by extension, embrace its risk. Accordingly, your risk management policies should inspire confidence within your stakeholders (e.g., employees, clients, senior management, and executives). Organizations that can prove their vigilance and preparedness for detrimental incidents bolster trust, thereby preventing operational bottlenecks due to delayed stakeholder decisions.
4. Enterprise Risk Taxonomy
Given all the ways in which enterprise risk manifests itself, it’s worth providing a comprehensive taxonomy that classifies them. These classifications will inform you of the distinct nature of each risk type, thereby enabling the development of targeted strategies to address them.
- Industry-specific risk is – predictably – unique to a company’s particular sector. For example, the biggest risk in healthcare involves worsening a patient’s condition or, at worst, death due to negligence, carelessness, and/or inexperience.
- Compliance risk can be defined as the degree to which companies adhere to governmental regulations, such as the GDPR, SOX, HIPAA, etc., as well as the risks associated with non-compliance and legal ramifications.
- Hazard risk is often dormant and pose potential threats to the life and health of workers or the workplace environment. For example, geopolitical tensions in certain regions could evolve into full-on, armed conflicts. Moreover, natural disasters like wildfires, earthquakes, hurricanes, and meteor showers are examples of hazard risks.
- Operational risk entails possible disruptions to everyday business activities. They are caused by a number of factors, ranging from a breach in a company’s critical IT structure to hiring underqualified workers for important positions.
- Financial risk is a vast category that comprises both controllable and uncontrollable risks that are linked to liquidity, credit, alongside imprecise financial models, market fluctuations, and equity.
- Strategic risk usually results from poorly-planned initiatives, falling behind on the technology and innovation curve, and/or “bold” marketing strategies. In gist, these risks often entail repercussions from poorly-deliberated executive decisions.
- Reputational risk is somewhat tied to strategic risk. It is often a consequence of one or more operational incidents or strategic failures. This type of risk falls into its own category because it’s the most damaging type across all business sectors.
That said, not all risks are equally prevalent in all businesses. Moreover, the risk management landscape fluctuates and evolves as new threats emerge monthly or more. For example, a 2013 Deloitte survey involving 300 executives reveals that more than 80% of multinational corporations explicitly manage strategic risk.
However, today, the majority of enterprise risk management is centered on preventing reputational risk, which has been on the rise ever since the advent of the internet and social media. Operational risks related to IT security, insider threats, and storage of sensitive data are also enjoying the spotlight, not least because they, of all other threats, have the greatest impact on a corporation’s reputation.
5. What Are the Limitations of Traditional Approaches to Risk Management?
Traditional approaches to enterprise risk management often involve assigning subject matter experts to each business division to manage its respective risks. This is also referred to as the “siloed” approach, wherein each business division acts as a standalone unit with its own taxonomy of critical risks. In effect, this approach allows for minimal cooperation between departments.
The following list further outlines key limitations of this traditional approach:
- There are risks that can affect multiple units at the same time. If a senior manager in one of the units/silos notices a critical risk, he/she might not realize that it could be critical to other silos too. This might result in a situation where one of the silos falls prey to a “new” risk that was already assessed by another unit, yet not shared with other divisions due to lack of insight and poor communication.
- Certain risks might be located outside of a particular silo, thus making them undetectable to the subject matter expert(s) in question. Regardless of their awareness, these risks still exist and therefore still pose significant threats to a company’s operations and strategy.
- Leaders of silos might not be aware of how a given response to a seemingly unit-specific risk can affect other facets of the company. In such cases, an appropriate risk response in one unit could trigger a critical risk increase in another.
- Traditional risk management practices are focused internally. However, more often than not, the most serious disruptions are caused externally. From competitors upgrading their products to new financial regulations – there’s ample justification for why enterprise risk management should not be self-contained.
- When leaders of individual silos are not involved in corporate strategy decisions, decision-makers tend to lack critical knowledge of new or potential risks. But when the risk management process is conducted in a centralized manner, executives can harness that knowledge for strategic planning.
These 5 reasons highlight why simply implementing risk management is not enough on its own to be considered an all-encompassing remedy. Complacency is even more insidious than some of the most common and critical risks. That’s why it’s important to implement and execute risk management procedures with careful deliberation across all company departments.
6. IT and Cybersecurity risks
Once a sub-category within the Operational group, IT-related risks slowly transformed themselves into the most feared enterprise threats. This is because all major businesses today possess large volumes of highly sensitive data, which necessitates high-security protections. There are ample ways in which such private data can be exposed, such as cyber-attacks, malicious insider activity (e.g., theft, sabotage), trojans, keyloggers, and other types of social engineering hacks that can effortlessly undermine the integrity of the most stringent security protocols.
IT security risks are different from all other types of enterprise risk. For example, they not only require organizations to go beyond the mere implementation of risk mitigation strategies. But they also require active and rigorous monitoring, alongside reacting to threats with lightning speed.
Solutions for such weighty tasks can fortunately be automated within one of the Information Security frameworks, or the steadily evolving category of IT Security Governance platforms (to which Greenlight belongs). Such software solutions enable organizations to track all digital employee activities for analysis. Through these analyses, such specialized software can recognize and flag potentially harmful behavior. When the software detects malicious behavior on the part of “bad actors”, it can then automatically revoke their access to all sensitive information until an official review is conducted.
In addition to Greenlight, we’ve provided a detailed list of similar software under the heading, “Enterprise Risk Management Solutions”.
7. Insider Threats: The Most Dangerous Enterprise Risk
Operational risks that arise internally are called “insider threats”. They’re most insidious because the company must provide these “bad actors” with sensitive data, in good faith, so they can fulfill their roles. Thusly, these risks involve malicious activity that’s carried out by a current or former employee, contractor, or business partner. According to recent research conducted by Verizon, in certain industries like healthcare, internal actors are responsible for as much as 44% of all data breaches.
A prime example of an insider threat would be a recently disgruntled employee whose access to confidential information was not restricted in a timely manner. These might be employees who were recently demoted, reviewed negatively, passed over for a promotion, or subject to a paycut, Many times, this malicious individual could abuse his/her access to the company’s network to retrieve and share highly-sensitive, confidential, or competitive data with third parties, either for financial compensation and/or vengeful purposes.
In other circumstances, insider threats could lead to the theft of employee credentials and other such crippling disruptions to business operations.
It’s a good time to note that not every insider threat will be inspired by malicious intent. It’s worth mentioning that the majority of these kinds of incidents occur for relatively innocuous reasons, such as negligence and human error. That’s why it’s important to take preventive measures against insider threats. For example, insider threats in the IT security realm are largely preventable with the enforcement of zero trust and least privilege policies.
Let’s have a closer look at what each of these terms mean:
Zero Trust is a software and network architecture model that was originally developed in 2010 by John Kindervag of Forrester Research. This model, in its simplest form, illuminates one key principle – corporate security should never automatically validate anyone, regardless of whether they’re internal or external to your company. As such, this Zero Trust policy effectively blocks out all potential threat sources until they’re authenticated.
Least Privilege is a software and network architecture policy that restricts access to only the minimum information that’s required for users to effectively execute their roles. This ensures that any user or computer program within a company must have secured strict permissions to access critical data for their operations. Therefore, any excessive permissions and data access is revoked in order to minimize insider risk.
Both these Zero Trust and Least Privilege policies lie at the core of Pathlock’s Control platform – one of the most innovative software solutions for facilitating the prevention of insider threats. For example, Pathlock’s platform automatically analyzes all user permissions, across an entire corporate ecosystem, to pinpoint dangerous instances of excessive data access.
8. Compliance in Enterprise Risk Management
Compliance with legal regulations comprises a significant portion of modern risk management practices. As such, if you’re unable to keep pace with ever-changing governmental regulations, not only do you pose serious threats to your business, but you expose it to debilitating legal consequences. It’s not uncommon for compliance risks to result in multimillion-dollar fines or, at worst, a complete halt to business operations.
Here are some examples of the most common regulations that organizations must comply with:
Sarbanes-Oxley Act: A US federal law enacted in 2002 that outlines the responsibilities of public corporations in order to hold them accountable to shareholders. It aims to improve the accuracy of their financial reporting. This act was largely motivated by a number of serious incidents involving large companies that tried to mislead external auditors by altering their financial statements or providing them with false financial data. To that effect, the Sarbanes-Oxley Act mandates companies to implement internal controls that precisely track their financial condition. Furthermore, this act requires companies to consistently conduct assessments that evaluate the effectiveness of these controls.
HIPAA: Enacted in 1996, this legal act regulates how personally-identifiable information is maintained within healthcare organizations, thereby safeguarding it from possible theft. It was specifically designed to protect patient information from disclosure to unauthorized parties. The most important application of HIPAA is its requirement to implement internal controls within electronic information systems. If you’re unable to meet HIPAA’s requirements, your organization might face a complete shutdown until further reviewed by authorities.
SOC 2: A security focused audit, developed in 2014, by the American Institute of Certified Public Accountants (AICPA). It was created due to the increasing popularity of cloud-based data storage methods in enterprises. Consequently, SOC 2 helps ensure that companies not only store important client data in the cloud, but do so securely. SOC 2 further requires strict information security protocols to be in place; these protocols address an organization’s integrity, availability, and confidentiality procedures.
SOC 2 is a well-regarded standard that’s adhered to by many of the most trusted companies in the IT sector, alongside IT service providers.
PCI DSS: The Payment Card Industry Data Security Standard is a highly-specific set of security protocols, which ensures that all companies that store and process credit card information do so in a secure environment. It was first released in 2006 to effectively reduce any financial and reputational risks associated with credit-card transactions. In addition, the PCI DSS helps prevent information on a company’s owner(s) from being subject to theft. Non-compliance with this regulation could result in compromised confidential data, which can severely damage your company’s reputation (again – one of the direst enterprise risks).
GDPR: The General Data Protection Regulation is a relatively new act that came into effect in 2018. It enforces a set of standards on how companies can store and process the personal data of EU citizens. The GDPR requires companies that store such personal data to implement risk assessments, data protection policies, and maintain internal documentation on their processes. Failure to meet these GDPR requirements can amount to fines as high as 10-million euros. If only for these reasons, EU companies give are highly inclined to give the GDPR due consideration.
CCPA: The California Consumer Privacy Act (CCPA) legally protects the personal data of any Californian whose information lies with a technology business. This regulation lists a number of mandates that enterprises must meet to remain compliant, such as letting clients know which information is being stored, as well as upholding clients’ rights to request that all their data be permanently deleted.
ISO 27001: Developed by the International Organization for Standardization, this is one of the most commonly used standards for information security in the world. It paves the way for companies to continuously protect all of their data in a cost-effective fashion. Unlike the other legal acts listed here, this ISO 27001 standard is merely an information security framework that can be adopted by companies to evidence the degree of meticulousness with which they deal with client data. The 3 main goals of this ISO 27001 framework entails protecting all data confidentiality, integrity, and availability.
All of these regulations necessitate the enactment of different security and enterprise risk management policies. Otherwise, it’d be practically impossible to comply with them. As a result, compliance with the ISO 27001 might prove to be a difficult task to tackle without external assistance. However, with software like Pathlock, companies can rest assured that they’re compliant with all of these standards. Especially since Pathlock is capable of embracing the tedious task of data governance and security, all while ensuring compliance.
9. What Risks Are Specific to Certain Industries?
While enterprise risk is to be expected for organizations across all economic sectors, some of these risks are specific to certain industries. The list below highlights what some of these industry-specific risks look like.
- Healthcare: Workers in this industry are highly-subjected to workplace violence. Incidents of this nature occur at least 4 times more frequently than in other industries (e.g., manufacturing). Also, the healthcare industry becomes quite vulnerable in cases of global pandemics (e.g., COVID-19). Healthcare risk is, thusly, defined as the speed with which such diseases are transmitted into the modern world, especially with helpful factors like overpopulation and excess international travel.
- Manufacturing: The inherent complexity of manufacturing supply chains makes the industry vulnerable to risks/threats from social and geopolitical pressures, alongside lacking quality assurance measures. Another related risk involves talent shortages. Each position within a manufacturing workforce usually necessitates specific training/qualifications. Without adequate supply of qualified personnel, these businesses risk staff shortages or hiring ill-equipped personnel out of desperation. In such cases, unqualified personnel and the lack of qualified workers pose internal threats.
- Information Technology: The speed and regularity with which the IT industry innovates the tech sphere is unparalleled. Though new technologies are often appealing to consumers, from a business perspective, they can be disruptive to operations. Organizations in this industry must quickly adapt in order to retain their client base and remain competitive.
Moreover, the volatility of human resources poses other threats within the IT industry. For example, a well-managed team of talented programmers can develop products with features and functionalities that eclipse those of their competitors. However, this creates a different type of competition, wherein rival companies try to steal employees away with higher-level positions, compensation, and/or conduct corporate sabotage.
- Finance: Credit risk remains atop the list of significant threats to the finance industry/banks. It occurs when borrowers can’t repay their debt, which leads to dire consequences not only for the banks, but the economy at large. Anyone who lived through the 2007-2008 financial crisis that rippled through the world due the growth of the US housing bubble has witnessed, first-hand, the repercussions of credit risk.
- Communications: New technological standards within the communications industry, such as 5G networks, constantly force companies in related industries to update and revamp all of their software and equipment, which is nothing short of costly. When companies are unable to ride the wave of such innovations, they risk getting left behind.
These are just some of the industry-specific risks that businesses regularly face. It’s also important to reiterate here, that the corporate risk landscape is constantly evolving. As such, while some risks like financial liquidity are impossible to eliminate, other risks will gradually become extinct and inadvertently be replaced by new challenges. This natural evolution of risk demonstrates, yet again, why risk management is a critical matter for businesses.
10. Benefits and Drawbacks of Enterprise Risk Management
Here are the main advantages of implementing rigorous risk management practices:
- Better strategizing: Enterprise risk management enables businesses to foresee and proactively adopt strategies to prevent and/or minimize risk. That way, they can seize only those opportunities which have an ideal risk-return- ratio.
- Corporate resilience: Enterprise risk management fosters a high degree of corporate “self-awareness”. This makes it much easier to accurately predict the majority of potential incidents, as well as quickly and effectively respond/adapt to them before they become manifest.
- Clearer top-to-bottom vision: Field workers collect risk-related data, the foundation upon which risk management ground processes are built. Such massive amounts of internal data can help bring to light the majority of dormant or “incognito” risks/threats.
- Reduced stress: Embarking on a novel project or undertaking causes undue stress as companies try to counterbalance the fear of uncertainty with the imperative to succeed. As such, risk management practices are invaluable during the project planning process. Without stress and fear from uncertain risks, your team(s) can simply focus on what they do best – their role-specific tasks.
- Maximum operational efficiency: Risk management practices highlight how organizations can best maximize their operational processes, thereby maximizing revenue while accounting for interest, taxes, depreciation, and amortization (EBITDA). With an effective ERM approach, businesses can achieve ultimate operational efficiency while fostering an environment that discourages overworking, unreasonable expectations, and burnout.
- Complete compliance: Continuous risk management, as related to compliance, ensures that your company always adheres to even the most obscure and stringent legislation. The financial risk of non-compliance can be remarkably crippling for even the largest, most well-established organizations.
The drawbacks of enterprise risk management are much less numerous and show themselves mostly in situations when there’s simply too many resources allocated for the sole task of managing risks. In such cases, unnecessary concern may be artificially induced and critical business opportunities missed as a result. So, as with many other good business practices, moderation is advised.
11. How to assess and prioritize risk?
The first step in implementing enterprise risk management involves assessing existing risks. To do so, businesses need to develop a proprietary risk register or log as a means of risk identification. Such risk registers include extensive descriptions for each risk, as well as information about their origins, suggested solutions, and any current countermeasures.
Moreover, this register should further contain insights from all of the business’ departments and agencies to ensure objectivity. Subsequently, the business should organize these risks into categories to accumulate data based on each division. This requires a thoughtful approach. For example, being ultra-specific and creating too many risk categories can result in redundancy. Whereas overly broad categorizations can blur the borders, thus making it harder to glean meaningful insights.
Only after you’ve completed this comprehensive list, can you begin the prioritization process. This involves rating each risk in terms of its potential severity or impact on business operations.
Once cross-divisional consensus is reached on your proprietary risk log, it can be distributed to each department, after which they can begin developing a standardized risk-reporting format. That way, each department can stay informed. It also provides easy access for auditing purposes or executive reviews. In this way, the risk register serves as a central database.
12. Types of Risk Management Solutions
Enterprise risk management solutions can be divided into two broad categories:
- Frameworks (also referred to as methodologies)
- Risk management software
ERM frameworks provide recommendations and guidelines on how to manage corporate risk. Whereas software solutions provide digital tools to automate associated tasks. For example, digital risk registers are most commonly used among field workers, which enable field workers to access risk-related data via forms and surveys.
Let’s take a closer look at some of the industry’s top risk management frameworks and software solutions.
A. Frameworks and methodologies
ISO 31000
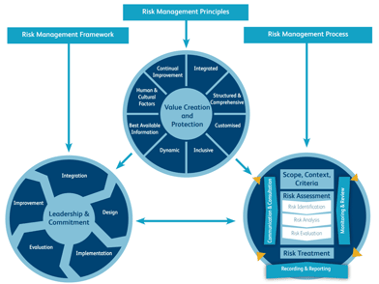
Developed in 2009 by the International Organization for Standardization, the ISO 31000 is the most popular Risk Management Framework in the world. It was revised in 2018 with more concision.
The eight main tenets of the ISO 31000 framework involve being:
- Proportionate. Customize the framework in line with your unique company needs.
- Aligned. Ensure all risk management processes within your organization are executed in sync with business activities across all departments. Moreover, stakeholders/executives should be actively involved to remain aligned.
- Comprehensive: Risk management is only fruitful when it’s comprehensive and well-structured.
- Embedded: Ensure that your risk management program is inseparable from all business activities.
- Dynamic: Managing risk is an active, rather than passive process. As such, it requires rapid response and adaptation to the ever-changing threat landscape.
- Demanding: Only the best and most current data should be taken into consideration for effective risk management.
- Human: Factor in any human demographics, such as age, culture, and experience/educational background, that could affect the integrity of business operations.
- Evolving: Your risk management practices should continuously improve and be refined as you learn about and encounter new threats. These experiences inadvertently equip you to better identify future risks.
The ISO 31000 framework is invaluable for businesses, as it provides a tried-and-true method of effectively implementing risk management across all business activities. To learn about this framework in more detail, visit the ISO website.
COSO
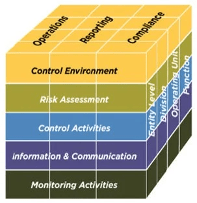
The COSO framework was formed by a joint initiative of several associations, including the American Accounting Organization (AAA), in 1992. It’s been updated several times since then, the latest version of which was released in 2013. The main purpose of COSO is to help organizations establish internal controls over their operations – with an emphasis on achieving business goals, clear reporting, and SOX compliance.
COSO includes five integrated components:
- Control environment – Outlines specific processes and standards that need to be implemented as the basis for internal controls.
- Risk assessment – The ground rules that determine how various risks are assessed and prioritized.
- Control activities – Preventive policies and procedures that help mitigate risk.
- Information and communication – While “information” describes the flow of useful data for internal controls, “communication” outlines the methods through which senior management shares such information, which should be instantaneous and easy to access.
- Monitoring activities – Continuous or periodic verification that all internal control components are functioning optimally.
COSO suggests 5 phases for adopting its framework:
- Planning;
- Documentation development;
- Implementation;
- Testing; and
- Optimization.
Note that these guidelines are flexible. Thusly, you’re encouraged to customize it to suit your particular business’ needs. To learn more about the COSO Risk Management Framework, visit their website.
Risk Management Framework / NIST 800-37
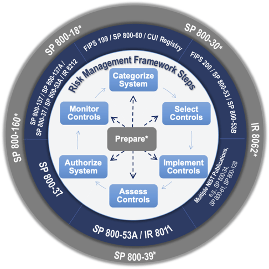
Developed by the National Institute of Standards and Technology (US) in 2016, the “Risk Management Framework” (RMF) is specially designed to help businesses establish key information security practices. It follows the Federal Information Security Management Act (FISMA).
The RMF outlines seven steps for implementing information security practices and safeguarding against risk. Each step includes a number of key tasks with defined lists of roles, responsibilities, and required outcomes in order to smoothly progress through the RMF implementation process. The steps are as follows:
- Prepare: First, you’ll need to establish how you’ll implement the RMF across various business activities, particularly when it comes to how you’ll communicate between IT security managers and executives (both at the operational and mission/business levels).
- Categorize: Analyze and prioritize risks based on the nature and criticality of the information or processes it affects. To do so, you’ll need to predict the outcomes of various worst-case scenarios, such as the degree of damage posed by exposing sensitive data to the general public.
- Select: Establish and select baseline security controls based on how you categorized the risks/threats in the previous step.
- Implement: Deploy and thoroughly document any developed security controls.
- Assess: Evaluate how well your business implemented the RMF system by ensuring that it functions, at the very least, in line with standard security requirements.
- Authorize: Someone from senior management either approves or denies the baseline security controls based on performance or higher-level business considerations.
- Monitor: Continuously monitor implemented security controls for any changes, threats, or suspicious activities that can compromise the security of sensitive company data.
It’s worth noting that, because RMF was designed in a tech-neutral manner, it can be adopted by virtually any industry. In addition, this same institute also provides a Cybersecurity Framework that addresses a variety of modern and highly focused cybersecurity issues. For more information on RMF and FISMA, visit the NIST website.
B. Software
In addition to the aforementioned risk management methodologies, in this section, we present a list of the best enterprise risk management platforms on the market. If you’re interested in viewing a more comprehensive list, we’ve provided a thorough guide on the best ERM software solutions [1] for enterprise risk management.
1. Pathlock Control
Pathlock Control is capable of monitoring all employee activity within your digital landscape. It immediately sends alerts to your security team via integration to popular SIEM’s (LogRhythm, Splunk, QRadar) whenever suspicious behavior is discovered. Whenever a security risk poses too high of a threat, it swiftly and automatically executes prevention measures based on flexible rulesets. For example, if an unauthorized user tries to access a system without appropriate permissions, it forbids entry and notifies relevant security personnel. This is just one of many ways in which Pathlock can effectively shut down threats at the source.
In order to protect against compliance risks associated with legal acts and data security policies, such as the SOX and GDPR, Pathlock provides tools for Segregation of Duties (SOD) analysis, all while ensuring continuous protection of your critical data. Moreover, this software generates detailed reports that help companies to not only automate the access review process, but also pass security audits with ease.
Best features:
- Can detect existing and potential SOD conflicts, effectively reducing operational risks
- Supports integration with the leading business apps, such as SAP, Oracle, NetSuite, Workday, Salesforce, and others to monitor user activity across these tools
- Identifies and prevents potentially malicious behavior before it evolves into an incident
- Generates detailed reports on all facets of your company’s information security data
- Smooth and stress-free audits due to automated reports that are trusted by auditors
- Automates routine tasks for your security team, freeing their hands for what matters most
- Can be deployed as either SaaS or an on-premise solution, to suit your needs
Pricing:
You can request a custom quote from this page.
LogicManager
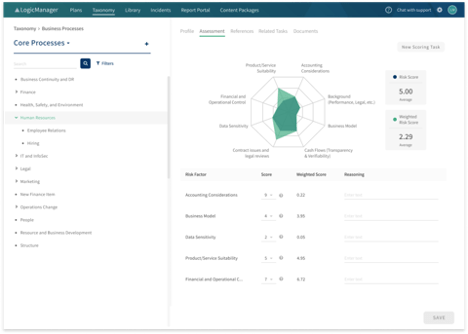
LogicManager is a complex Governance, Risk, and Compliance (GRC) solution for managing a wide assortment of enterprise risks. It helps businesses automate the risk identification, assessment, and prioritization process. In addition, LogicManager provides tools to continuously monitor risks as well as oversee their prevention. For example, it allows senior managers to effortlessly allocate specialized, everyday tasks to employees, and to report risk evaluation data to the platform.
This software also caters to companies who are new to enterprise risk management, by providing a collection of industry-specific templates. They’re built right into the platform so as to minimize the learning curve and expedite the prevention, identification, and mitigation of critical risks.
Moreover, LogicManager is also equipped with compliance management tools, ensuring that your business operations align with key policies, such as the GDPR and SOX. In this way, you can avoid the costly legal ramifications of non-compliance without having to resort to the tedium of manual verification.
Best features:
- SaaS risk management solution that also acts as an IT governance and regulatory compliance solution
- Helps companies build their risk management processes from the ground up, using reporting, assessment, and monitoring tools
- Streamlines both internal and external risk auditing and analyses with simple yet thorough graphic reports
Pricing:
You can request a custom quote from the vendor.
Intelex
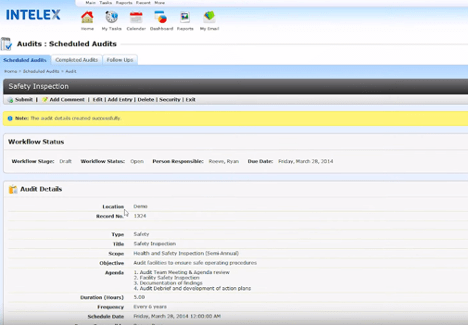
Moreover, Intelex generates exhaustive risk data reports that can satisfy even the most discerning audit board. Not only does this bring dormant threats to the surface, but this automated reporting process takes a load off with regards to passing internal and external audits. Compatible with both desktop and mobile devices, this software minimizes disruptions to everyday workflows by enabling remote access to all its main features.
Best features:
- Complex ERM platform based on the most popular framework in the world – the ISO 31000
- Provides customizable forms and surveys to help businesses establish risk-related data collection procedures
- Equipped with illustrative dashboards that display and update all risk-related data in real-time
- Provides access to a worldwide community of risk-management specialists for support, general knowledge, and to stay informed of new risks/threats
- Grants access to powerful risk analysis tools that can help companies recognize the true nature, scope, and potential damage posed by critical threats
Pricing:
You can request a custom quote from the vendor.
CURA
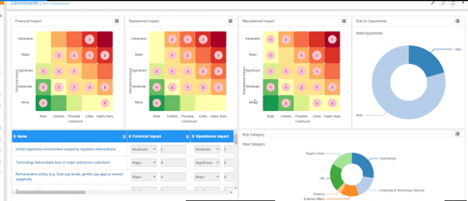
CURA is a renowned GRC enterprise solution that bears striking similarities to the abovementioned software. It provides a readymade risk management infrastructure that equips companies will the required tools for managing internal and external operational risks. As such, CURA is the “cure” that minimizes the rate of risk-related incidents while providing invaluable insight into your company’s vulnerabilities. This enhanced awareness empowers organizations to seize major opportunities, as well as to better recognize how they’re positioned, competitively.
As with most other enterprise risk management tools, employees must enter all risk-evaluation data into the platform. This is done via customizable forms and surveys, which contain selected criteria that guide risk prioritization decisions. In addition, CURA supports most key regulations, and accordingly, makes for a handy compliance tool.
Best features:
- Provides a secure, online ERM platform that enables a role-based, user experience
- Contains an API for integration with other apps, thus allowing for ultimate convenience and flexibility
- Equipped with an informative and visually-appealing dashboard that helps managers identify key risk data, and efficiently enforce mitigation policies
- Provides several ways to send notifications to other users in the system
- Sends automatic reminders prompting employees to conduct risk-evaluation assessments, as well as urgent alerts for board members, thus ensuring no threat goes unnoticed
- Supports top risk management frameworks, thereby allowing you to make informed decisions about your unique organizational needs and obtain optimal results
Pricing:
You can request a custom quote from the vendor.
Integrum QHSE
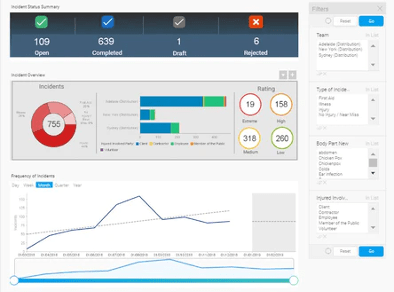
Integrum QHSE is an integrated Quality, Health, Safety and Environment (QHSE) platform that allows for
seamless implementation of enterprise risk management policies. Despite the fact that it was specially designed for large companies, it also proves valuable for smaller organizations. Integrum establishes which risk management activities are most core to business operations, by granting access to risk evaluation surveys, and providing managers with flexible risk assessments.
Because its main focus is enterprise risk management, Integrum can also be used as a project management tool and Business Intelligence reports generator. For added value, it further boasts some impressive HR functionalities. In addition, Integrum markets itself as an ERM solution that provides unrivaled reporting and insight into any given set of risk evaluation data. In effect, this software makes it much more easy for stakeholders and executives to accurately project into the future, and decide on the best business strategy accordingly.
For ultimate ease and convenience, Integrum also features a number mobile applications that will make employees’ everyday risk management roles much more manageable. Not to mention, Integrum can be deployed in several different ways, which is sure to be appreciated by your IT team.
Best features:
- Combines all required components of effective risk management into one comprehensive SaaS platform
- Equipped with LMS capabilities to not only deliver eLearning/corporate training, but also track employee progress
- Empowers risk owners to specify which policies and mitigation measures that will need to be executed in case of a risk/threat escalation
- Helps ensure compliance with major regulations like the SOX, ISO 27001, etc.
- Provides 24/7 access to your organization’s full history of operational incidents, as well as documented risks and incidents, for easy and relatively “hands-off” internal and external audits
- Features enhanced risk analysis tools that permit you to precisely predict the potential occurrence of incidents, and take proactive/preventive measures
- Provides options for several deployment methods, including on-premise, custom cloud and, of course, SaaS
Pricing:
You can request a custom quote from the vendor.
13. Enterprise Risk Management Maturity Model
The Risk Maturity Model (RMM) is a self-assessment benchmark for companies that would like insight into how well they manage risk. It outlines the activities and indicators for several levels of risk management, from Ad Hoc to Mature.
There are seven key attributes to the risk maturity model, each of which addresses various aspects of planning and maintaining an enterprise risk management program:
- Adopting ERM-Based Processes measures the effectiveness of your company’s risk culture and evaluates the degree of involvement that your executive board members have.
- ERM Process Management measures how organizational ERM policies are implemented in the company and how much they coincide with industry best practices.
- Risk Appetite Management measures the degree of a company’s risk accountability, therefore defining its risk tolerance and risk profile. Risk Appetite Management also verifies how, and how well, your organization is closing the gaps between actual and potential risks.
- Root Cause Analysis Discipline identifies a business’ ability to analyze risk and identify their respective root causes. As such, this discipline is distinguished from symptom-based identification.
- Uncovering Risks highlights how well your business is performing with regards to accumulating risk data. Consequently, it evaluates the quality of your risk assessments and data collection methods.
- Performance Management measures an organization’s ability to smoothly and swiftly execute planning, communication, and develop strategies while leveraging risk-oriented approaches.
- Business Resiliency and Sustainability determines if your business is (properly) using a risk-driven approach for the purposes of operational planning, and by extension, market sustainability.
It’s important to note that there are two versions of the RMM. The first version is for executives and stakeholders who are overseeing the risk management evaluation process. Whereas, the second version caters to employees who are not only tasked with executing everyday business activities, but also ensuring smooth business operations.
Regardless of which version you’re using, both serve as invaluable sources of insight into how well your business is managing risk. It also enhances your businesses’ self-awareness by providing analyses on risk mitigation from unique perspectives and vantage points.
14. How to Choose the Best Risk Management Solution for your Company
Not all risk management solutions are made equal. Accordingly, before you invest in a particular product, we’ve provided some general guidelines for choosing the ideal solution.
- Allocate a substantial period of time to market research to clear up any uncertainties before making a final decision. Because risk management processes will need to be integrated at all levels of normal business operations, you’ll need a product that is ultra-malleable or most closely coincides with current processes.
If, after the implementation phase, you suddenly realize that the chosen solution is unfeasible, then changing the “risk management horse” mid-stream can cause a lot of internal friction and negatively impact the company’s overall performance. Remember: Proper Prior Planning Prevents Piss Poor Performance (the principle of 7 Ps).
- Learn common risk terminology. It’s much easier to identify and evaluate all available enterprise risk management solutions when all employees adhere to the same, standardized terminology as the product vendors.
- Try to identify the most critical risks. Before making any decisions, it’s worth analyzing and identifying which company-specific risks are most critical. This information provides a frame of reference for what features to prioritize in your ideal ERM solution, and serves as a baseline for decision makers to assess the efficacy of each proposed solution.
For example, if your company works with massive amounts of highly confidential data, the biggest risk it faces is exposure or disclosure of said information to unauthorized parties. In order to address this risk, executives should prioritize risk management solutions that primarily focuses on data security.
- Assess the simplicity of everyday risk evaluation procedures for employees. The quality of a risk management solution is largely dependent on the quality of risk data that field workers provide on a daily basis. If the risk assessment forms that they submit are poorly designed, or if the mobile app that grants access to such surveys has a glitchy interface that provides a poor user experience, your risk data will be incomplete.
- Make sure the product can be integrated into everyday business operations. Some products just are relatively inflexible or allow for minimal scalability. In these cases, the size or structure of your company might impact your ability to leverage such tools. To avoid this tedious/complex issue, find out consult with other similarly sized companies to glean from their experiences.
- Check what legal acts and regulations you need to comply with. These days, most risk management software supports a number of regulatory acts, including the SOX, HIPAA, and GDPR. Choosing the right solution will make it much easier to comply with these regulations. Not to mention, you’ll avoid a ton of stress.
No two companies are wholly alike. Thus, you’ll need to adapt this checklist to your specific business needs. That notwithstanding, it’ll give you a good leg up.
Frequently Asked Questions (FAQ)
- How is enterprise risk management different from traditional risk management?
The main difference is that ERM, unlike traditional risk management approaches, identifies risks and makes predictions that guide decisions on the best corporate strategies. This means that ERM doesn’t only focus on the current situation. It further focuses on future outcomes, maximizing profits, and business sustainability.
- Does implementing enterprise risk management ensure business success?
Not necessarily. While ERM provides managers and IT teams with insight into risk-related issues and incidents, this does not automatically lead to better management decisions. Such limitations stem from human error – an ever-present risk – regardless of your risk management software, method, or strategies.
Moreover, the COSO framework states that companies should consider their risk management programs as mere insurance, without “religiously” relying on its predictions. The future is forever fraught with unpredictability, that no enterprise risk management program can fully tame.
- What is risk appetite?
According to ISO 31000, risk appetite is the amount of risk that a company is willing to embrace in order to achieve its strategic goals. Businesses regularly evaluate their risk appetite and use it as a deciding factor in whether or not to pursue certain business opportunities.
- Who is a risk owner?
A risk owner is an individual that occupies a senior management position. Therefore, he/she is accountable for all efforts and activities involved in preventing and mitigating particular risks. Therefore, risk owners are not only responsible for ensuring that stakeholders are adequately involved in the risk management processes, but also delegating tasks that help quell these risks.
As a result, risk owners regularly monitor any risks they’re assigned to, all the while engaging in ongoing communication with executives. This ensures that executives/stakeholders can make informed decisions when developing or adjusting corporate strategies.
- What is a heat map?
A heat map (or risk map) is a visualization tool that’s used to present risk assessment results in a clear, “at a glance” manner. Organizations place their critical risks on this chart, positioning them based on their potential impact and likelihood.
- What is residual risk?
Residual risk is the uncertainty that remains after the establishment of mitigation measures.
Conclusion
Today, enterprise risk management is a large field that spans both theoretical and practical knowledge. It is not only taught at the university level, but specialists in the field are also in high demand. In addition to ERM being a critical practice for the prosperity and longevity of businesses, ERM itself has become a booming industry. The field is inundated with visionaries who appreciate the inherent value, and thus opportunities, that come from partaking in this line of work.
Regardless of whether you’re within or outside of the financial, healthcare, or manufacturing sectors, risk management might still come across as obscure, unclearly formulated, and/or ineffective. But no business is impermeable to data security, reputational, or financial risk, especially internally. Not to mention, the worldwide transition towards digital business models and strategies, and an all-round heavy reliance on technology to streamline processes, demonstrates how ERM practices can yield substantial and tangible results – across all industries – when taken seriously.
If you’re wondering whether it’s time to implement ERM in your company, then contact us to find out how you can start reaping the benefits!



