Market Leader in Governance, Risk, and Compliance for JD Edwards EnterpriseOne
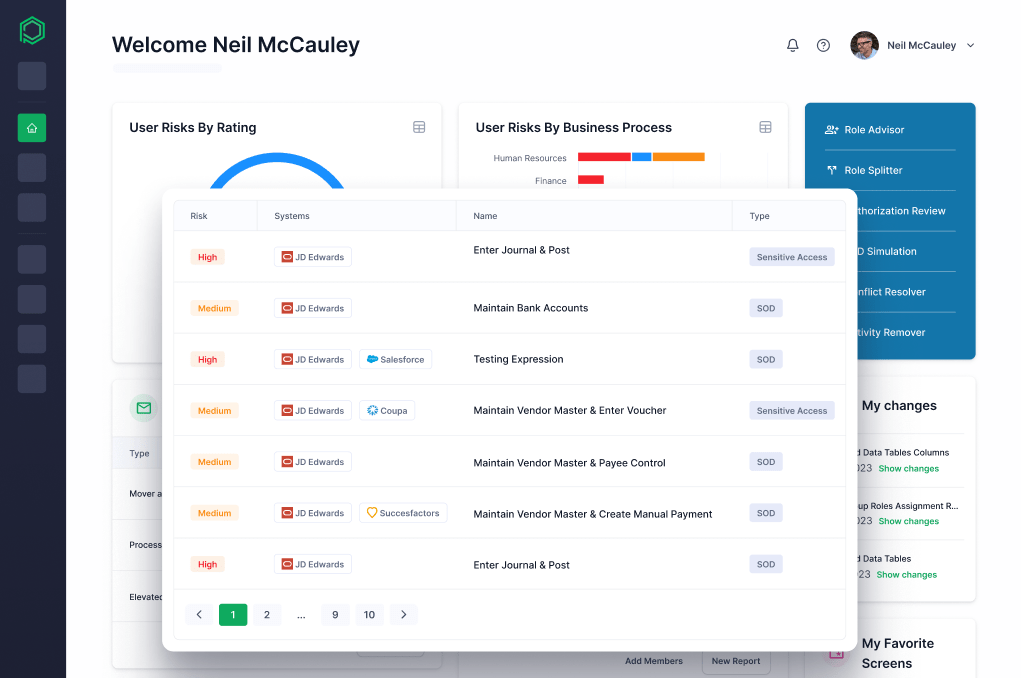

Pathlock automates your SoD and sensitive access risk analysis and reporting for your JD Edwards deployment. We provide pre-set, easily customizable rulesets, ensuring quick time-to-value for your organization and reducing risk and costs with an automated approach to risk analysis.
Pathlock’s automated approach to compliant provisioning allows you to create, maintain, and remove access for technical and business roles. It offers the most detailed provisioning capabilities, enabling you to better align access with business requirements, and all provisioned access is accompanied by audit-ready documentation.
Pathlock automates user access review so that organizations can accurately and quickly recertify access. Workflows eliminate spreadsheets, buried emails, and chasing down absent-minded reviewers.
Pathlock’s Role Management capability is a powerful, visual role builder which lets you assess the audit readiness and quality of existing roles while also allowing you to design new roles that are proven to be compliant with simulations and “what if” analysis.
Pathlock supports the largest catalog of business applications out of the box.

Learn why Pathlock is named an overall leader for product leadership, innovation, and market share.
Book a one-on-one demo with an JD Edwards audit expert consultant and learn how Pathlock can help you save as much as 80% on your audit costs.
