Technical SAP users with extensive authorizations like SAP_ALL pose a heightened security risk. Vulnerabilities can endanger interfaces and paralyze processes, so external auditors are intensifying their focus on authorization management. Let’s look at how we helped one of our customers – a company in the energy sector – who was facing the challenge of having to restrict the authorizations of its technical users (batch processing/RFC interfaces).
Insufficiently Protected SAP Users Pose a Hazard
Technical SAP users are often not adequately protected. To ensure the security of your SAP system, you should follow the need-to-know principle and only grant technical users the authorizations they need to do their jobs. This means carefully reviewing each user’s access privileges and removing unnecessary permissions. You should also be aware of dynamic application cases where the specific roles needed by users may change over time. By taking these steps, you can protect your SAP system from unauthorized access. Here is how we differentiate between the two scenarios:
1. Static Object Usage
In this case, you can determine future needs by analyzing past usage.
2. Dynamic Object Usage
When users with dynamic object usage are involved, it is unclear which additional permissions these users will receive in the future. In this case, it is possible to connect additional applications through the same interface to start a query of entirely new objects.
Two Simple Steps to the Solution
We first selected according to both scenarios.
Step 1: Select technical SAP users with static object usage.
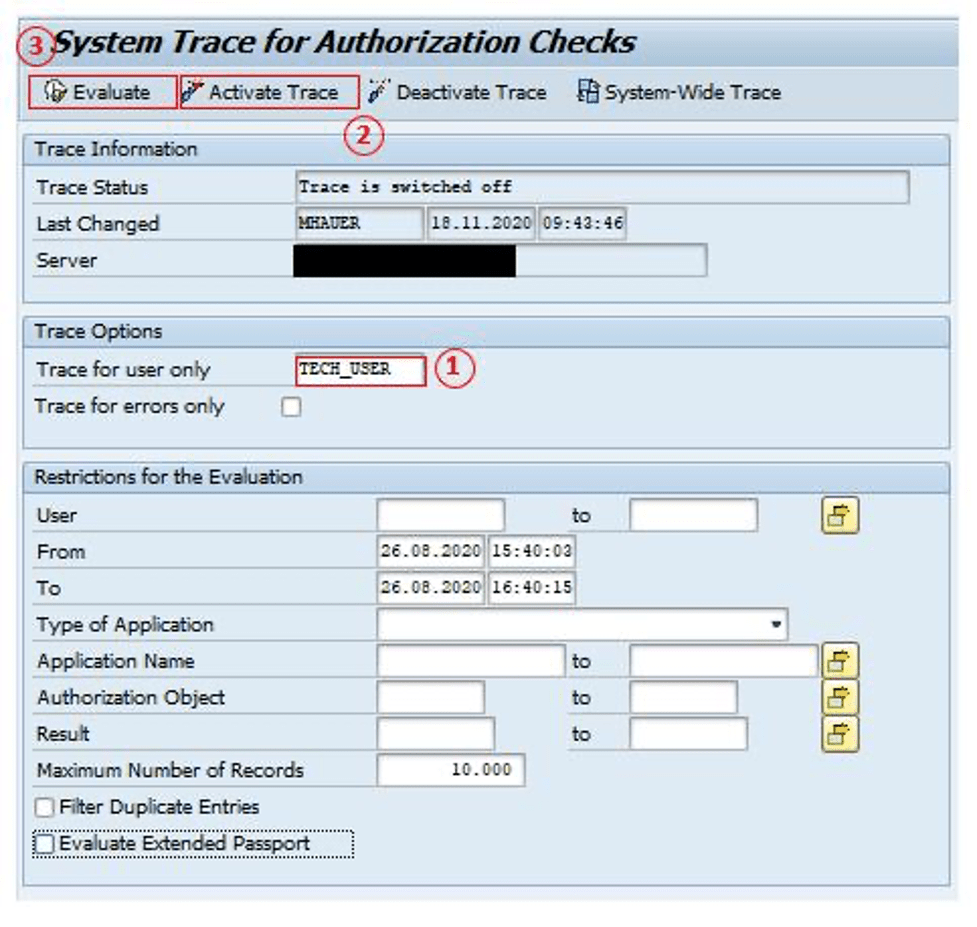
In the future, this user will carry out the same activities they previously performed. By analyzing the authorization trace data (transaction STAUTHTRACE, ST01), we could identify which authorization objects the user needs and remove those that aren’t needed from the single or composite role.
Excerpt from the transaction “STAUTHRACE – System Trace for Authorization Checks”:
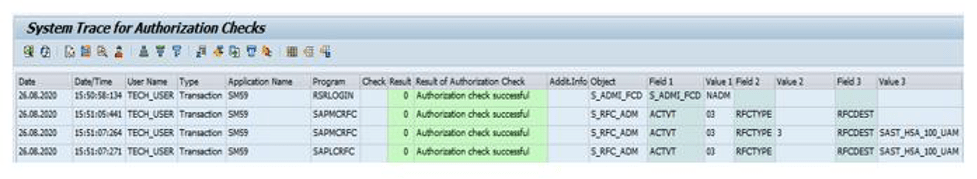
Excerpt from the log of recorded trace data, showing which objects the technical user used in the selected period:
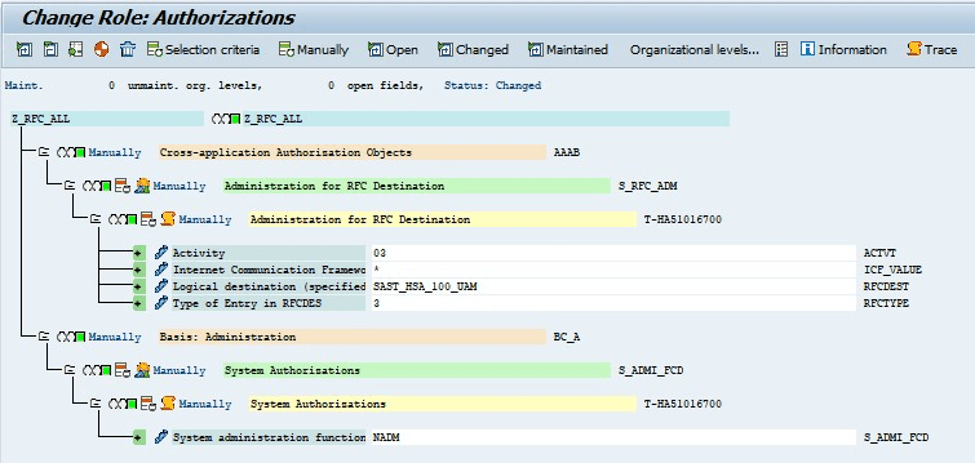
The next step involves enhancing the new role with only those RFC authorization objects and their values that are absolutely necessary instead of granting extensive authorizations or even full authorizations:
Our recommendation: Separate technical users should be created for each scenario (batch processing/RFC interfaces); collective users should be avoided because they have extensive authorizations that can also be misused.
Step 2: Restrict technical SAP users with dynamic object usage.
Particularly when business functions are used, SAP Basis authorization objects and transactions are assigned simply and directly.
If extensive authorizations are exploited, the following critical authorization objects can pose serious problems:
– S_TABU_DIS / S_TABU_NAM (access to tables)
– S_DATASET (access to files in directories on the application server)
– S_USER_GRP (maintenance of user master records)
– S_USER_AGR (maintenance of authorization roles)
– S_DEVELOP (ABAP development)
– S_RFC (remote function call)
– S_ADMI_FCD (system administration)
Our customer in the energy sector had specific targets to reduce risks by restricting certain objects in the production system. It was crucial that these objects were never given full authorization. To achieve this, every object had to be set as “Inactive” or “Display Restricted” in the production systems.
Creating a role based on the “SAP_ALL” profile:
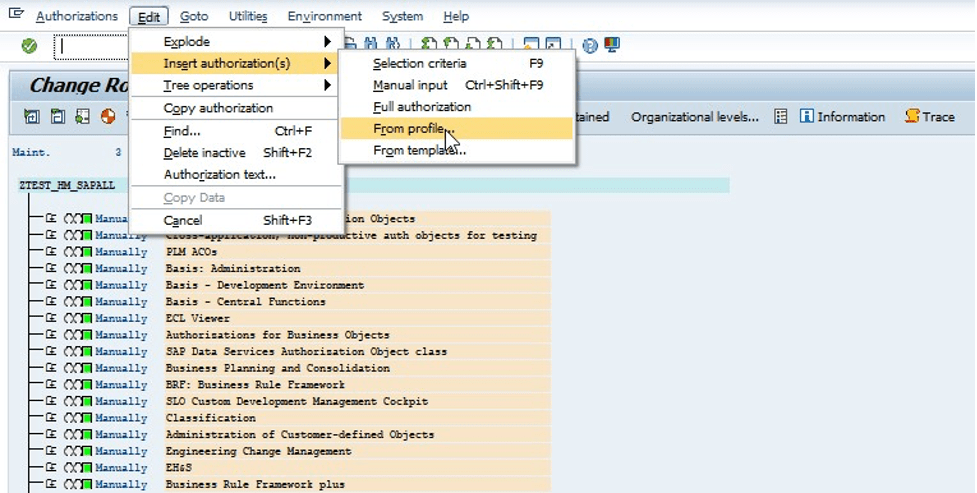
Restricting the affected objects by deactivating the authorization object S_DEVELOP:
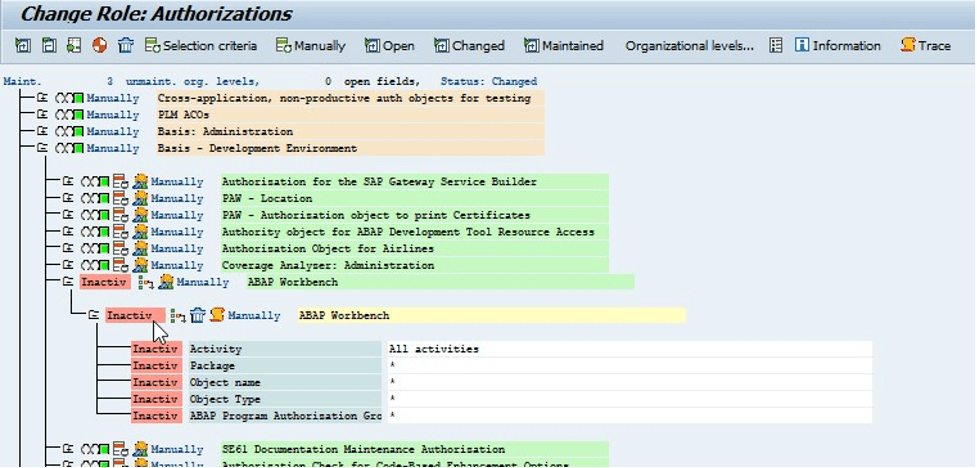
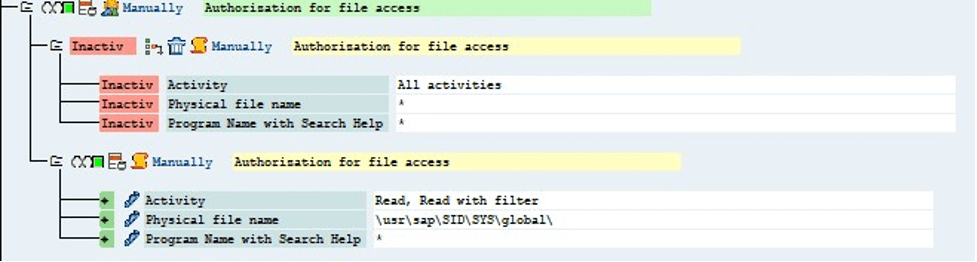
In transaction “PFCG – Role Maintenance,” the object “S_DATASET” allows deletion and modification of files in all directories – it was set to inactive as a result:
Pathlock Enables Mass Analyses and Role Assignment Virtually at the Touch of a Button
With this role authorizations best practices project, we supported our customers’ conversion of technical users in the hypercare phase. Any errors during batch processing or in the RFC interfaces were closely monitored in the initial days of the changeover and were corrected quickly using a smart fallback procedure.
Our customer from the energy sector utilized Pathlock in addition to the standard SAP solutions to ensure efficient execution. We simplified and automated the process significantly, from the initial analysis to going live. With Pathlock, we were able to analyze users on a large scale and create roles with the touch of a button without disrupting regular operations. This procedure resulted in significant time savings and significantly reduced risk through conflict-free authorization roles.
Are you interested in optimizing the role adjustment process for technical SAP users? We can help! Get in touch with us today.
Pathlock Solution Brief
S/4HANA Migration: Automated Role Re-design Solution Brief
Learn how Pathlock automates the role design and testing process, allowing security teams to complete the role re-design project significantly faster, saving both time and costs.



