This is the first article of a multi-part series featuring material weaknesses. Each piece will focus on one critical internal control weakness and provide solutions on how to resolve the weakness with granular security controls.
The purpose of an independent audit of a company’s financial reports, called a Financial Statement Audit, is to form an opinion by the independent auditor if the current and potential investors can rely upon the accuracy and completeness of the company’s financial statement. During this audit, the auditors will evaluate the design and operating effectiveness of the internal controls intended to manage the risks relevant to maintaining the accuracy and completeness of the financial reports. The auditor may identify deficiencies in the company’s internal control over financial reporting, which will be ranked from lowest to highest impact as Control Deficiency, Significant Deficiency, or Material Level Weakness.
What Is A Material Weakness?
According to the PCAOB, a material weakness is “a deficiency, or a combination of deficiencies, in internal control over financial reporting, such that there is a reasonable possibility that a material misstatement of the company’s annual or interim financial statements will not be prevented or detected on a timely basis.” Companies with material weaknesses are required to report them in their public SEC filings in the period in which they were identified. There are multiple types of internal control weaknesses that could lead to a material weakness.
Access Control Weakness
Segregation of duty (SoD) security violations are among the most common examples of an access control issue in ERP applications that lead to an auditor reporting a material-level control weakness. The principle of SoD is based on appropriately segregating critical duties to more than one person. For example, a single person should not have the ability to create and approve vendors, nor should that same person have the ability to create and approve payments. These four access rights could easily lead to fraudulent activity.
Resolving SoD Security Violations With Pathlock
The avoidance of SoD security violations within your ERP application starts with an effective user-provisioning process that enables organizations to proactively analyze the role assignments to verify that no SoD violation exists before authorizing the access assignment. Unfortunately, most organizations use manual user provision processes that are tedious and error-prone.
Pathlock automates your user-provisioning, de-provisioning, and access recertification process and enables real-time detection and prevention of SoD violations. Pathlock also continuously monitors user behavior and authorization usage. This allows organizations to de-provision unused authorizations and flag sudden deviations in user activity, thereby reducing the overall risk and enhancing threat detection.
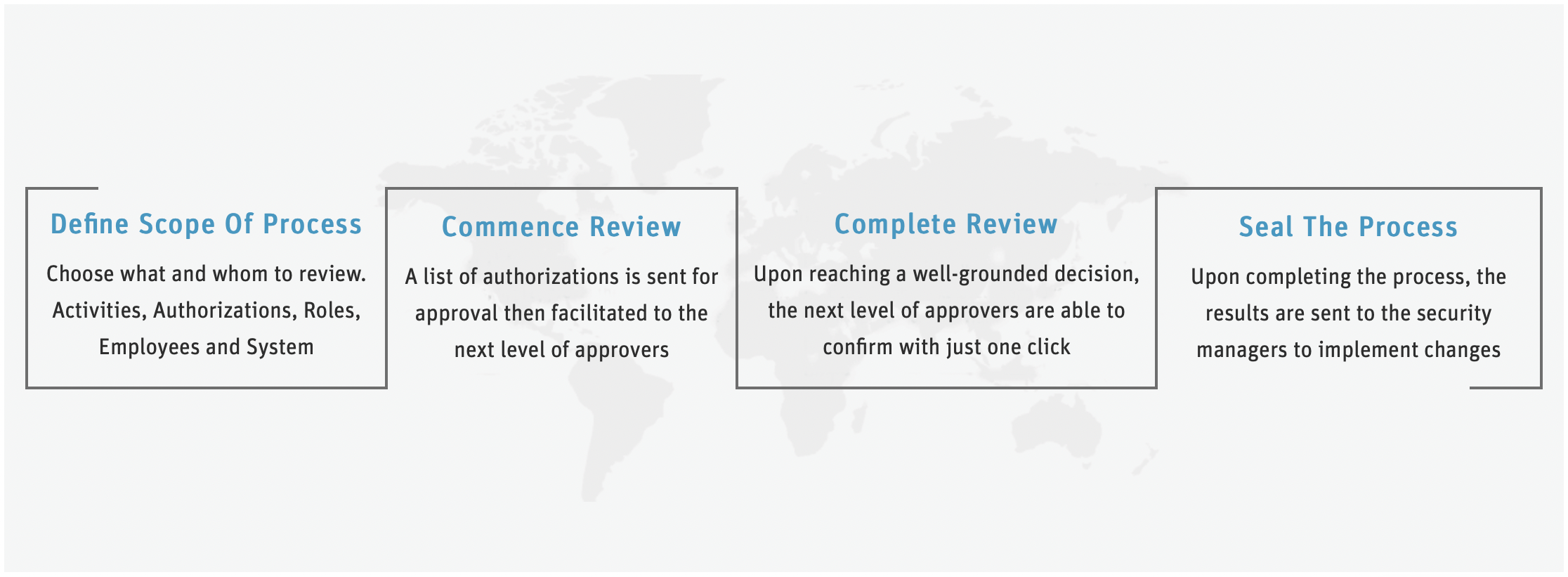
Some of the other leading practices offered by Pathlock to prevent SoD violations include:
Policy-Based Access Control
With policy-based access, organizations can go beyond roles to implement controls based on contextual attributes. A policy-based access control security model improves your policy enforcement capability at the SoD level.
Identity & Access Management (IAM)
Authorization, being an integral part of IAM, allows you to increase the effectiveness of your user-access management lifecycle process. By implementing dynamic MFA at the login, page, and data field level, you can ensure sensitive data and transaction changes are logged and protected.
Identity Governance & Administration (IGA)
With real-time user monitoring, you can remove unnecessary authorizations while gaining governance and oversight of all user access to increase your ability to detect and prevent SoD violations.
The Pathlock Platform gives you complete visibility and control of your ERP applications from the inside to resolve critical material control weaknesses. See the Pathlock Platform in action by scheduling a demo.


