What is Azure AD Connect?
Azure AD Connect allows you to connect on-premises identity infrastructure to Azure Active Directory (Azure AD). It lets you manage identities across a hybrid infrastructure consisting of public cloud and on-premises resources. Once your on-premises directories are integrated with Azure AD, you can leverage this service’s features to simplify identity management and provide on-premise users with easier access to cloud-based resources.
Azure AD Connect Features
Password Hash Synchronization
Password hash synchronization is a sign-in method that supports hybrid identity. Azure AD Connect synchronizes a hash of the user’s password from an on-premises Active Directory instance to a hash of the user’s password in a cloud-based Azure AD instance.
Azure AD Connect sync implements password hash synchronization as an extension of the directory synchronization feature. It allows on-premise users to sign in to Azure AD services like Microsoft 365 using the same password as they do for the on-premises Active Directory.
Password hash synchronization also enables leaked credential detection for hybrid accounts. Microsoft works with law enforcement agencies and dark web researchers to find publicly available username and password pairs. If credentials belonging to your users match credentials available on the dark web, the associated account is moved to high risk.
Pass-through Authentication
Pass-through authentication is another way to let users access both on-premises and cloud-based applications with the same password. Passwords are validated directly against your on-premises Active Directory.
Pass-through authentication is an alternative to password hash synchronization. The difference is that this option allows organizations to enforce their on-premises Active Directory security and password policies in the cloud.
Pass-through authentication can be combined with the seamless Single Sign-On (SSO) feature. These features combined allow users to access cloud applications from their corporate workstations, inside the corporate network, without typing in their password.
Federation Integration
A federation is a collection of domains with established trust for sharing access and resources. You can federate your on-premises environment with Azure AD for authentication and authorization. Using this sign-in method ensures all user authentication occurs on-premises and allows administrators to implement rigorous access control.
Synchronization
The Azure AD Connect synchronization component handles all operations related to synchronizing identity data between your on-premises environment and Azure AD.
This component creates users, groups, and other objects in Azure AD. It verifies that identity information for your on-premises users and groups matches the information in the cloud. This component also supports password hashes.
Azure AD Connect Health
Azure Active Directory Connect Health is used to monitor your on-premises identity infrastructure to ensure you maintain a reliable connection to Microsoft 365 and Microsoft Online Services. This feature provides monitoring capabilities for your key identity components and makes the key data points about these components easily accessible.
You can use this feature to view alerts, monitor performance, and analyze usage to keep track of the health of key identity components.
Pathlock & Microsoft Azure Active Directory Integration
Read how Pathlock’s integration with Microsoft Azure Active Directory provides enterprises with an identity governance solution SOX, SoD, & others.
Azure AD Connect Architecture
The following diagram shows the architecture of Azure AD Connect and how it integrates between Azure AD and an on-premise Active Directory forest (the largest unit of organization inside Active Directory, organizing multiple Active Directory trees).
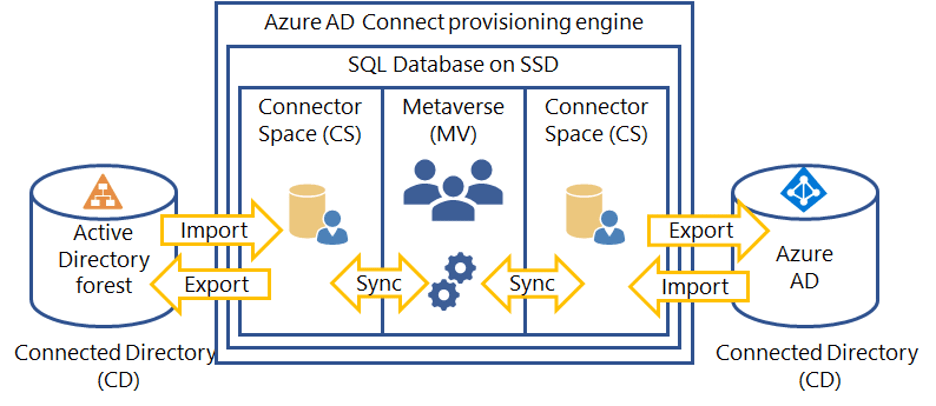
The provisioning engine connects to each Active Directory forest, and on the other end, to Azure AD. The process of reading information from each directory is called an import. An export creates updates in the provisioning engine. A sync operation evaluates rules on how objects flow through the provisioning engine.
Azure AD Connect uses the following staging areas, rules, and processes to enable synchronization from Active Directory to Azure AD:
- Connector Space (CS)—objects from each connection directory (CD), which are physical directories, are first prepared and then processed by the provisioning engine. Azure AD has its own CS, and each forest it connects to has its own CS.
- Metaverse (MV)—objects that require synchronization are created here according to synchronization rules. The object must exist in the MV before it is populated with other associated directories.
- Synchronization rules—determine which objects to create or connect to objects in the MV. Synchronization rules also determine which property values to copy or convert to and from the directory.
- Run profiles—copies object and property values according to the synchronization rules between the staging area and the associated directory.
Best Practices for Using Azure AD Connect
Here are a few best practices that can help you use Azure AD Connect more effectively.
- Protect the server like a domain controller—the server running Azure AD Connect should be treated just like a domain controller. Limit administrative rights and login permissions, and control physical access. An attack against Azure AD Connect is equivalent to an attack against the domain controller.
- Closely monitor who can use Azure AD Connect—by default, only those who install the sync engine, and admins of the local machine can access Azure AD Connect. You can add more users to the ADSyncAdmins group on the local server, but be very selective about who you allow to access it.
- Use Azure AD to manage Azure AD—create cloud-only administrators with predefined system roles such as Global Administrator and Application Administrator. The Global Administrator is a “super user” who can change any administrative setting in Azure AD, so Microsoft recommends granting this permission to up to 5 people in your organization. Use Azure AD advanced authentication features such as MFA.
- Carefully control which groups to sync to Azure AD—by default, Azure AD Connect synchronizes all groups to Azure AD, but it is a good idea to limit the groups you sync. Keep in mind that some groups are security groups (used to limit access), and some are distribution groups (used to easily contact a group of people). Identify which groups are not relevant to your cloud deployment and exclude them.
Related content: Read our guide to Azure AD Identity Protection (coming soon)
Azure AD Security with Pathlock
Pathlock is the leader in Access Governance for business-critical applications. Staying compliant with Sarbanes-Oxley is a critical business requirement, and Pathlock helps to automate the compliance process. As a MISA member, Pathlock can bring these capabilities to users of Azure Active Directory, with tight integration between the solutions.
Customers rely on Pathlock to streamline critical processes like fine-grained provisioning, separation of duties, and detailed user access reviews. With Pathlock’s out-of-the-box integration to Azure Active Directory, customers can enjoy the best of both worlds, including:
- Coverage for the leading business applications, with support for key applications like SAP, Oracle, Workday, Dynamics365, Salesforce, and more.
- Perform compliant provisioning at a transaction code or function level into both cloud and on-premise applications.
- Define Separation of Duties (SOD) rules, both within an application and across them, and enforce them to prevent access risks and stay compliant.
- Enrich User Access Reviews (UARs) with fine-grained entitlement details and usage about transactions performed with specific access combinations.
Interested to learn more about the winning combination of Pathlock and Azure Active Directory? Request a demo today to see the solution in action!



