When consumers decide to use a company’s product or service, they are consciously or subconsciously confirming their digital trust in that organization to keep their data private and secure. Data security and data privacy are terms that the cybersecurity and infosec industries are familiar with, but perhaps you might not have heard much about digital trust; yet.
Digital trust was a priority topic discussed at the ISACA Conference North America 2022, held in New Orleans this past May. In fact, ISACA is developing a certification course, a digital trust framework, and a variety of other resources. I’d like to take a closer look at this critical topic and share how Pathlock’s capabilities can help organizations achieve and maintain digital trust.
What Is Digital Trust?
ISACA defines digital trust as the confidence in the integrity of the relationships, interactions, and transactions among suppliers/providers and customers/consumers within an associated digital ecosystem.
Put another way, digital trust is the level of confidence or assurance a consumer has in the ability of an organization’s people, processes, and technology to maintain a secure digital experience for the services or products they provide. Achieving and maintaining digital trust encourages companies to focus on mitigating inherent risks that negatively affect consumers’ trust in the organization’s ability to maintain secure systems and data.
The Problem With Digital Trust: Customers Have Trouble Trusting Companies
The cost of non-compliance is high. That said, compliance is just your floor and not the ceiling. Evolving
As consumers continue to share more of their personal information online with various organizations, that data is increasingly more at risk of being exposed or stolen. And with every headline about a data breach or personal data being stolen, sold, or used unethically, trust erodes.
To build trust, companies must ensure that sufficient controls and leading practices are in place to protect consumer and customer information against threats such as data breaches, identity theft, and privacy violations. Organizations that can prove they are effectively maintaining the following capabilities over their critical business systems and data are much more successful in maintaining digital trust with consumers: Governance, Application Security, Data Security & Privacy, Risk Management, Vulnerability Management, Threat Management, Compliance Management, and Audit Readiness, as illustrated below.
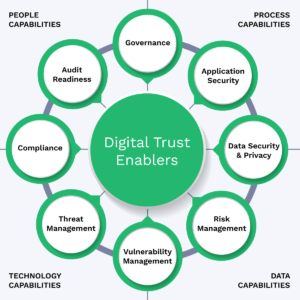
12 Leading Practices For Building & Maintaining Digital Trust
First, you need to realize that digital trust is a capability achieved and maintained by the four enablers – people, processes, technology, and data. Basically, people use processes enabled by technology to generate data utilized for decision-making and for the processing of business and consumer transactions. There are inherent risks, threats, and vulnerabilities associated with each of those four enablers that must be effectively managed to achieve/maintain the degree of confidence that encourages consumers to do business with the company.
Summarized below are 12 leading practices organizations can use to effectively manage the risks, threats, and vulnerabilities to achieve/maintain digital trust with their consumers. The first seven come from Gartner’s Continuous Adaptive Risk and Trust Assessment (CARTA) imperatives for safeguarding business systems, processes, and data.
Summary of Gartner’s Seven Security Imperatives.
1. Replace One-Time Security Gates with Context-Aware, Adaptive, and Programmable Security Platforms
Organizations need to move away from the initial one-time, yes/no risk-based decision at the main gate of their business systems (managed by a static role-based authentication and authorization process, also known as RBAC) to a continuous, real-time, adaptive risk and trust analysis of user anomalies with context-aware information across the platform.
The foundation of an adaptive security capability must be based on an adaptive security response, which cannot be achieved with the static RBAC security model. Context-aware security is the use of situational information, such as identity, geolocation, time of day, or type of endpoint device, found in the Attribute-Based Access Control (ABAC) security model. But you don’t need to get rid of your RBAC model in your current business systems. The ABAC model is a recent evolution of security intended to enhance your RBAC security model with capabilities not currently present.
2. Continuously Discover, Monitor, Assess, and Prioritize Risk — Proactively and Reactively
Risk events are fluid and require constant identification, analysis, prioritization, monitoring, and response after completing the initial login assessment. This should include a combination of proactive and reactive control capabilities. For example, suppose a user attempts to download a large amount of sensitive data. In that case, you need the ability to detect and prevent this action if it’s considered inappropriate. Again, ABAC can provide organizations with preventative, detective, and reactive controls when users attempt to log into the application, access business transactions, and access data.
3. Perform Risk and Trust Assessments Early in Digital Business Initiatives
This imperative focuses on performing your risk and trust assessments early in the process. Remember that the ABAC model is enabled through a continuous risk assessment process, as described in imperative #4, to enable detection and response to anomalies or threats. So, start early in the process, but enable a continuous risk and zero-trust assessment with ABAC.
4. Instrument Infrastructure for Comprehensive, Full Stack Risk Visibility, Including Sensitive Data Handling
This continuous risk assessment recommendation across the full tech stack and data handling enables adaptive security decisions. The imperative goes deeper into data handling to enable better data security and data privacy controls needed to safeguard assets.
5. Use Analytics, AI, Automation, and Orchestration to Speed the Time to Detect and Respond, and to Scale Limited Resources
This imperative promotes using artificial intelligence, machine learning, analytics, and automation to increase the efficiency and effectiveness of risk detection, analysis, and response capabilities.
6. Architect Security as an Integrated, Adaptive Programmable System, Not in Silos
This imperative warns organizations to not perform risk assessments in individual isolated silos. Instead, aggregate CRAs provide a more accurate view of the organizations’ risk exposure.
7. Put Continuous Data-Driven Risk Decision Making and Risk Ownership into Business Units and Product Owners
This imperative encourages better transparency and decision-making through better data-driven risk visibility to the business unit leaders for their own decision-making.
Additional leading practice to help you build and maintain Digital Trust.
8. Policy Enforcement
Establish effective Application Security, Governance, Risk, Compliance & Audit (SGRCA) policies to communicate Senior Management’s expectations for securing your critical business applications. The ABAC security model, often called the Policy-Based Access Control security model, can enable you to automate policy enforcement by configuring policy-based controls in your business systems that dynamically enforce policy requirements and detect and prevent risks and threats.
9. SGRCA Program Management
Leverage effective enabling technology to consolidate the management of your SGRCA programs across all business systems to realize greater operating effectiveness and cost savings.
10. Vulnerability Management
Arguably, one of the most effective ways to prevent threats from occurring is to perform a continuous vulnerability assessment that detects and remediates weaknesses in your business applications that could be exploited by threats.
11. Enable Zero-Trust
Zero trust – the principle of never trusting and always validating a user’s identity – can be enabled in many ways. One is through multi-factor authentication (MFA) when logging into a system, when attempting to access critical transactions, and when attempting to access critical data fields.
12. Enable Layered Security
Implementing layered security (also known as defense in depth) in overlapping layers of controls can typically provide the three control capabilities needed to secure assets: prevention, detection, and response. No individual security control is guaranteed to stop 100% of cyber threats. However, layered security provides mitigations against a wide variety of threats while incorporating redundancy in the form of compensating controls if one control should fail.
Achieving Digital Trust Across Your Business Applications With Pathlock
Pathlock’s automated PeopleSoft user provisioning solution lets you capture, assess, and respond to Data security, data privacy, and threat prevention are foundational to digital trust. If organizations cannot sufficiently protect that data, trust cannot be achieved/maintained. Pathlock offers you the ability to secure the leading business systems by implementing the 12 recommendations listed above, which help you build and maintain digital trust.
With Pathlock, you can:
- Configure policy-based access controls and enable automated policy enforcement
- Automate user access management processes (e.g., role design, provisioning, de-provisioning, access recertification, emergency access management, and privileged access management)
- Perform vulnerability assessment with over 4,000 pre-configured risk and threat scans to proactively avoid threats
- Conduct constant user behavior analysis to identify anomalies or threats
- Enable dynamic data security and privacy controls
- Enable data loss prevention
- Allow constant risk and control assessment and monitoring
Contact us today to see a demonstration of all our capabilities and learn how to secure all applications, transactions, and data with Pathlock.



