Business applications continue to be a top target for attack, with more organizations than ever reporting breaches that began within the confines of a business application. For example, did you know that the Colonial Pipeline ransomware attack ultimately brought down their billing system, which was what caused their days long outage?
Protecting the cyber landscape requires comprehensive security measures applied to every layer of communication stack for business applications, including the application layer. However, organizations still struggle to protect their critical data across their applications including SAP, Oracle, Workday, Salesforce, and NetSuite. Traditional security approaches which focus on hardening network and infrastructure are not sufficient to defend against the attack vectors involving misuse or abuse of authorized access in applications with sensitive data. Security teams have little or no insights into the risky user activities in applications, impacting the overall security posture. In many organizations, application layer visibility continues to be a blind spot in their cybersecurity programs.
The OSI Model
The application layer is the 7th and topmost of the layers in the Open Systems Interconnection (OSI) model. The OSI model, developed in 1984, provides a reference for layering the communications and information exchange to enable the interoperability of diverse communication systems with standard protocols. The model defines a hierarchical architecture that logically separates the standard functions of computer networking. In general, a given layer operates on the data and connectivity enabled by the layers below. The lower four layers are related to the hardware, network infrastructure and network level communications while the top three layers focus on the application functions, session establishment and data formatting for end-user interactions.
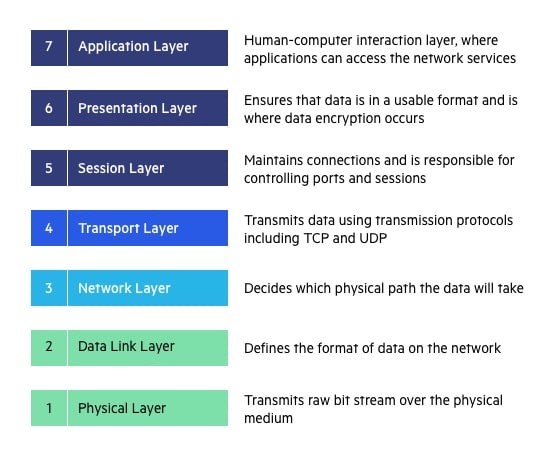
The seven layers of the OSI model are:
Layer 1: The Physical Layer addresses the physical characteristics of the physical media, such as the types of cables used to connect devices, data conversion functions and the electrical characteristics of the signals used to transmit data.
Layer 2: The Data Link Layer handles the packing and unpacking of data frames for transmission over a physical link between network entities and supports basic error detection to ensure that the data is received correctly. At the Data Link Layer, each network node is identified with the Media Access Control (MAC) address.
Layer 3: The Network Layer manages routing data packets through the network infrastructure. It operates at the level where network devices are recognized and managed with IP addresses, which are logical addresses mapped to the device MAC addresses.
Layer 4: The Transport Layer provides end-to-end communication control. This is where protocols like TCP and UDP operate to ensure that data packets are disassembled, moved through the network reliably and then reassembled into a data stream at the destination.
Layer 5: The Session Layer manages the application connection between two endpoints as well as authentication and authorization functions. This layer handles establishing, maintaining and terminating connections so the data can be exchanged for the application.
Layer 6: The Presentation Layer converts data sent through the network into information that can be used by the application layer. This layer addresses data formatting as well as data compression and encryption.
Layer 7: The Application Layer represents the layer that interacts with the user. This layer works with the application software to provide communications functions and the resources to support any data transfer for application services such as HTTP/HTTPS, FTP/SFTP. SMTP, DNS, etc. This is the layer where user access and perform business transactions in applications like SAP ECC, Oracle EBS, Salesforce. Ariba, Concur and NetSuite.
Securing the Layers from Top to Bottom
From the cybersecurity perspective, each layer in OSI model represents a different attack surface and requires different security measures to mitigate threats and vulnerabilities. By addressing security threats at every layer, organizations ensure data and application integrity, confidentiality and availability.
Security threats in layers 1 through 4 are typically addressed by IT and data center resources, either in-house or by hosting providers. As organizations move towards adopting SaaS solutions, much of the security at these layers is left to the 3rd party providers.
In the lower layers of the architecture, security threats include power outage, fire/water damage, physical access to hardware, MAC spoofing and man-in-the-middle attacks. Layers 3 and 4 are also vulnerable to TCP SYN flooding, sniffing, spoofing, routing disruption and unauthorized access. The effective protections to defend against attacks in Layers 1 to 4 include restricting physical access, hardening routers and switch configurations, updating firewall rules, blocking unused ports as well as disabling unused interfaces and network services. In addition, network traffic should be encrypted and monitoring solutions in place for intrusion detection and malware/virus scanning.
At layers 4 to 7, the threats take advantage of software vulnerabilities and gaps in securely storing and transmitting data. Attacks at these layers include SQL injections, cross-site scripting. phishing, backdoors and session hijacking. These layers are also exposed to zero-day attacks which rely on exploiting unknown vulnerabilities in network protocols/services and application software vulnerabilities. They are at risk for distributed denial of service (DDOS) attacks where multiple requests are sent to a targeted router or application in an attempt to overload it.
Preventing known attack vectors and restricting access to application services at the higher levels can partially be achieved with web application firewalls (WAFs) and secure web gateway services and cloud access security broker (CASB). However, they are incomplete, because they cannot monitor attacks which are being performed using legitimate credentials which may have been compromised by a phishing attack or are being used by a disgruntled employee.
Protecting from the Top: Securing the Application Layer
The application layer is the most accessible and the most exposed layer in the OSI model. It is the hardest to protect due the complexity of user interactions within the application which cannot be easily defined with intrusion detection signatures. Sensitive information like employee data, customer data, financial data, intellectual property no longer resides in file stores but is accessible via the application.
Critical business applications have become the largest concentration of sensitive data within an enterprise. Threat actors know the only way to access critical data is through the application itself. To gain application access, threat actors use increasingly sophisticated attack vectors involving phishing emails, account takeovers, credential stuffing, etc. Threat actors can then use authorized user accounts to execute critical transactions, download sensitive data or change system configurations, exposing the applications to the risk of data exfiltration, data tampering and disruption of business processes.
Driven by software as a service, remote work and digital transformation, the perimeter of the corporate network has all but disappeared and therefore solutions to secure the perimeter have become less effective in protecting data inside applications. Organizations need solutions to monitor application where critical data resides in order to detect unusual activities and precursor activities to data breaches and security incidents. Gaining insights in applications is challenging because each application is unique in its user interactions and transactions as well as its auditing and logging formats. Therefore, security operations teams must rely on applications experts to decipher and determine the critical activities and transactions. Security teams operating in silos cannot effectively perform alert triaging, security investigation and incident management for application security events.
Protecting Layer 7: Secure Applications with Pathlock
The most exposed layer needs the deepest visibility. Losing critical data in a breach is a major impact to the business so protecting critical business data means not only knowing where critical data resides, but also detecting and taking action when potential data loss is identified. With Pathlock, you can secure your application layer:
- Discover and classify data residing your application in order to determine the level of protection and visibility needed to secure the application.
- Extract real-time application user activity data to enhance SOC visibility beyond infrastructure and devices and provide in-depth application visibility.
- Transform and Normalize user activities, enabling unified monitoring of user behavior across diverse applications.
- Monitor applications for unusual transactions and data download as well as precursors security events such as privilege escalations and actions performed outside normal business hours.
- Automate responses to certain user activities including auto deprovisioning, enforcing MFA, and lock accounts to immediately mitigate risk of data leakage and security breaches.
Learn more about how Pathlock can help protect your application with deep visibility into user activities by requesting a demo.



