Go Beyond Traditional IGA
With the vast majority of breaches caused by human and access-related factors, effective IGA is essential. It strengthens security by ensuring the right users have the right access at the right time, while driving efficiency through automated provisioning and UARs that save time and reduce costs.
Pathlock Recognized as a Representative Vendor in Identity Governance and Administration
Modernize and Simplify IGA
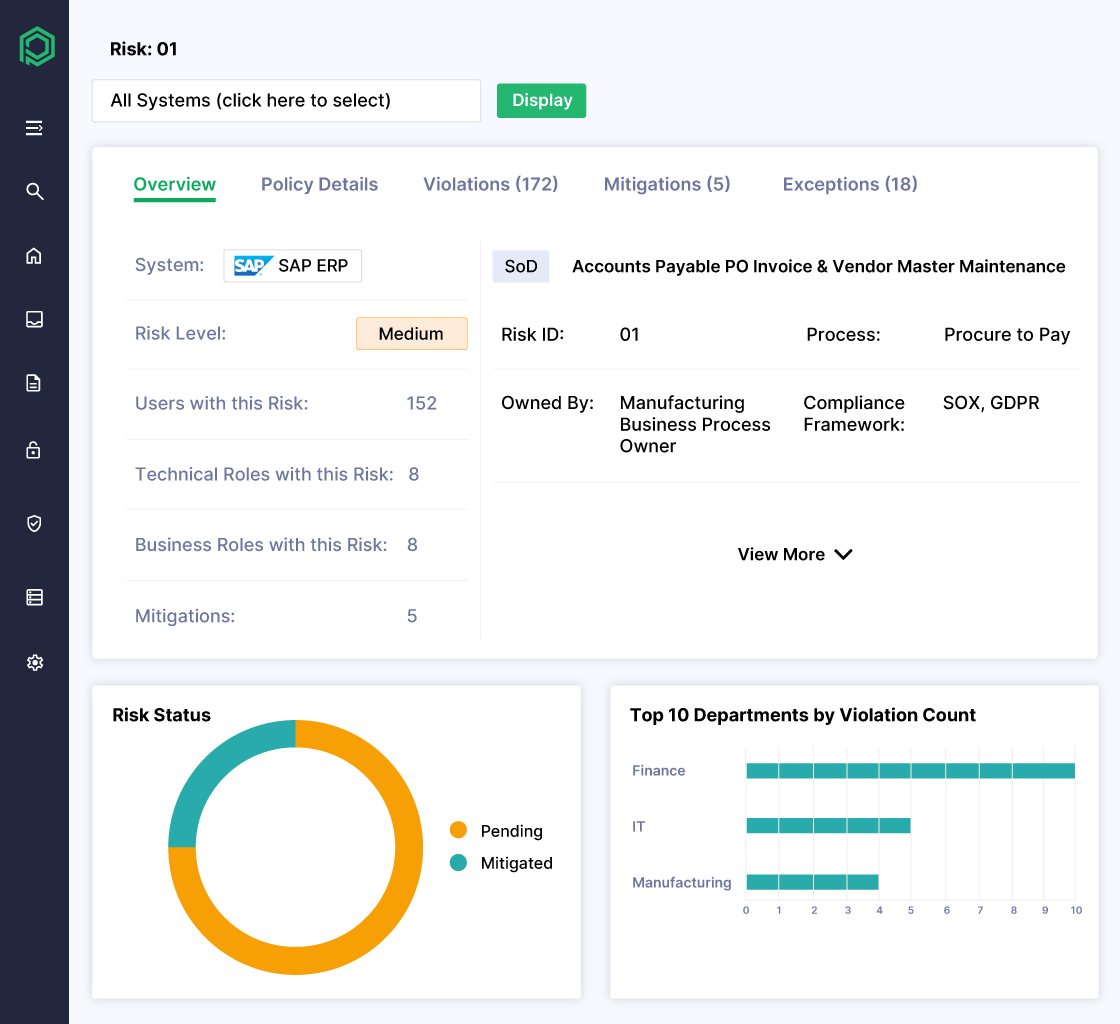
Uncover and Mitigate SoD and Sensitive Access Risks
- Get quick ROI by utilizing built-in risk rulesets
- Detect and remediate complex cross-application SoD conflicts
- Distinguish between theoretical and actual risks to prioritize remediation effectively
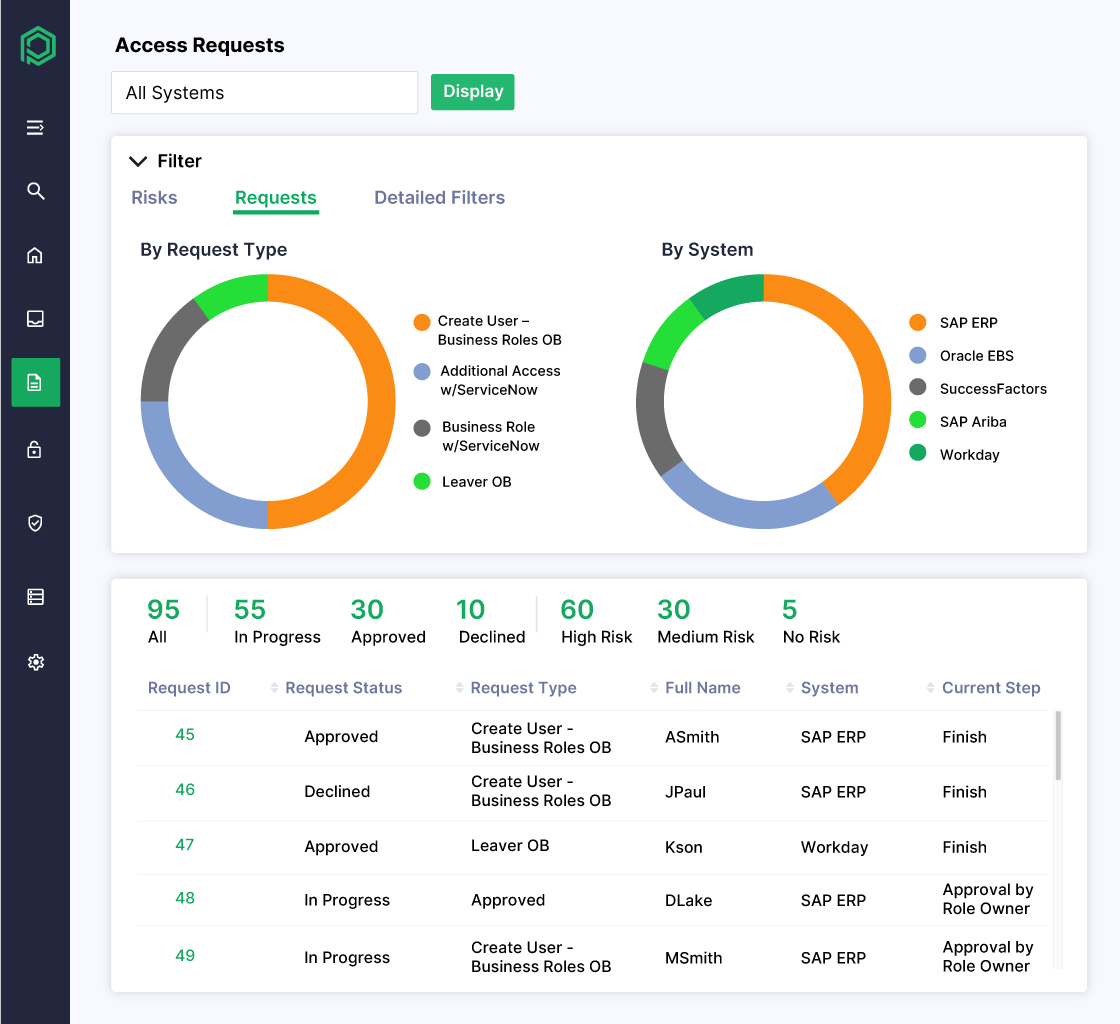
Streamline Compliant User Provisioning
- Provision access across ERP systems and enterprise apps like SAP, Oracle, Workday, and Salesforce
- Apply consistent rules and workflows across all user types—including employees, contractors, and third parties
- Simulate changes to determine if requested access introduces material risk
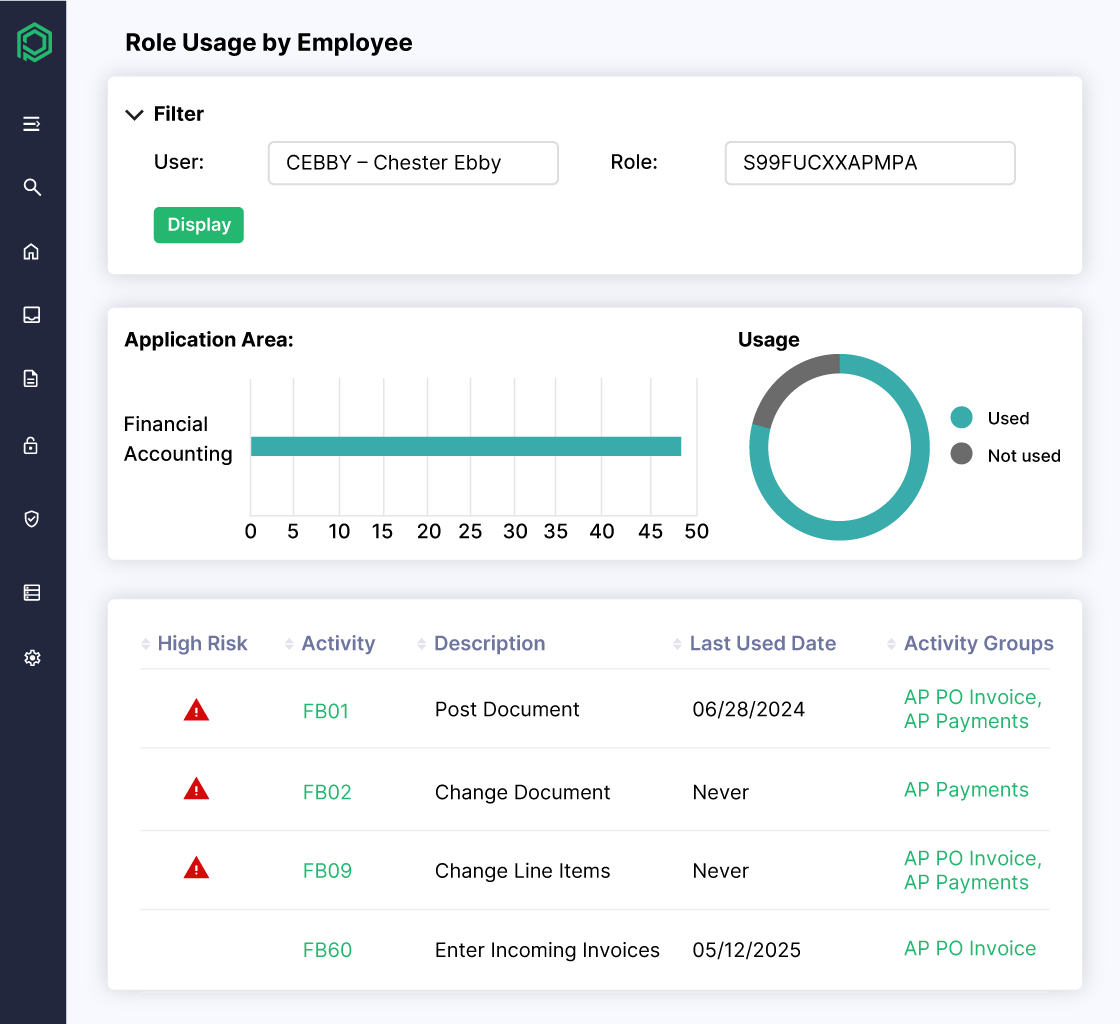
Automate Risk-Aware User Access Reviews
- Automate regular UAR campaigns and assign the right reviewers based on your specific requirements.
- Pinpoint users with unused access rights and eliminate excessive permissions
- Validate access to critical functions by aligning user behavior with policy
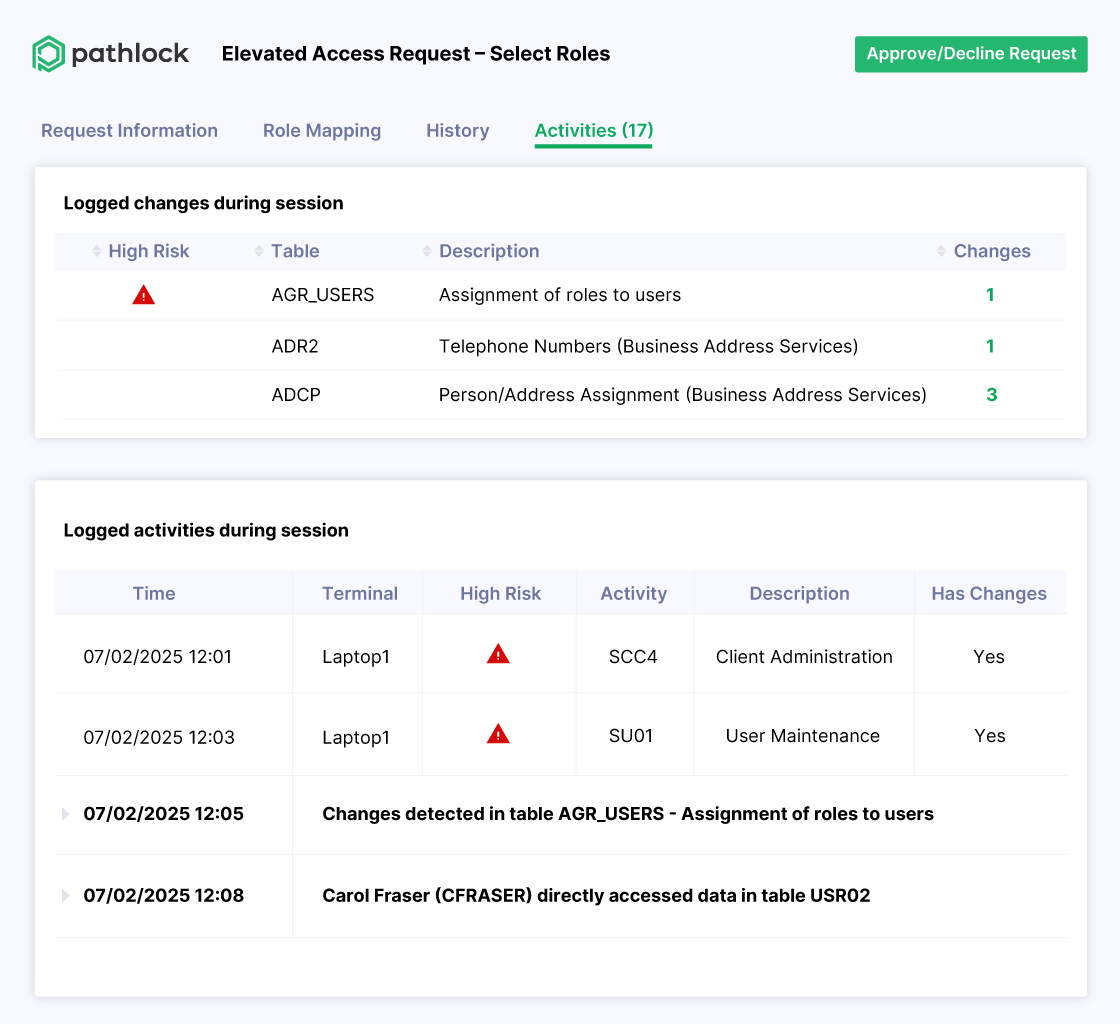
Automate Audit-Ready PAM for Business Applications
- Approve SAP Firefighter and privileged access requests from Oracle, Workday, and more—all within a single interface.
- Automatically revoke elevated privileges to prevent dormant permissions
- Track all elevated access activity and request history with unified reporting.
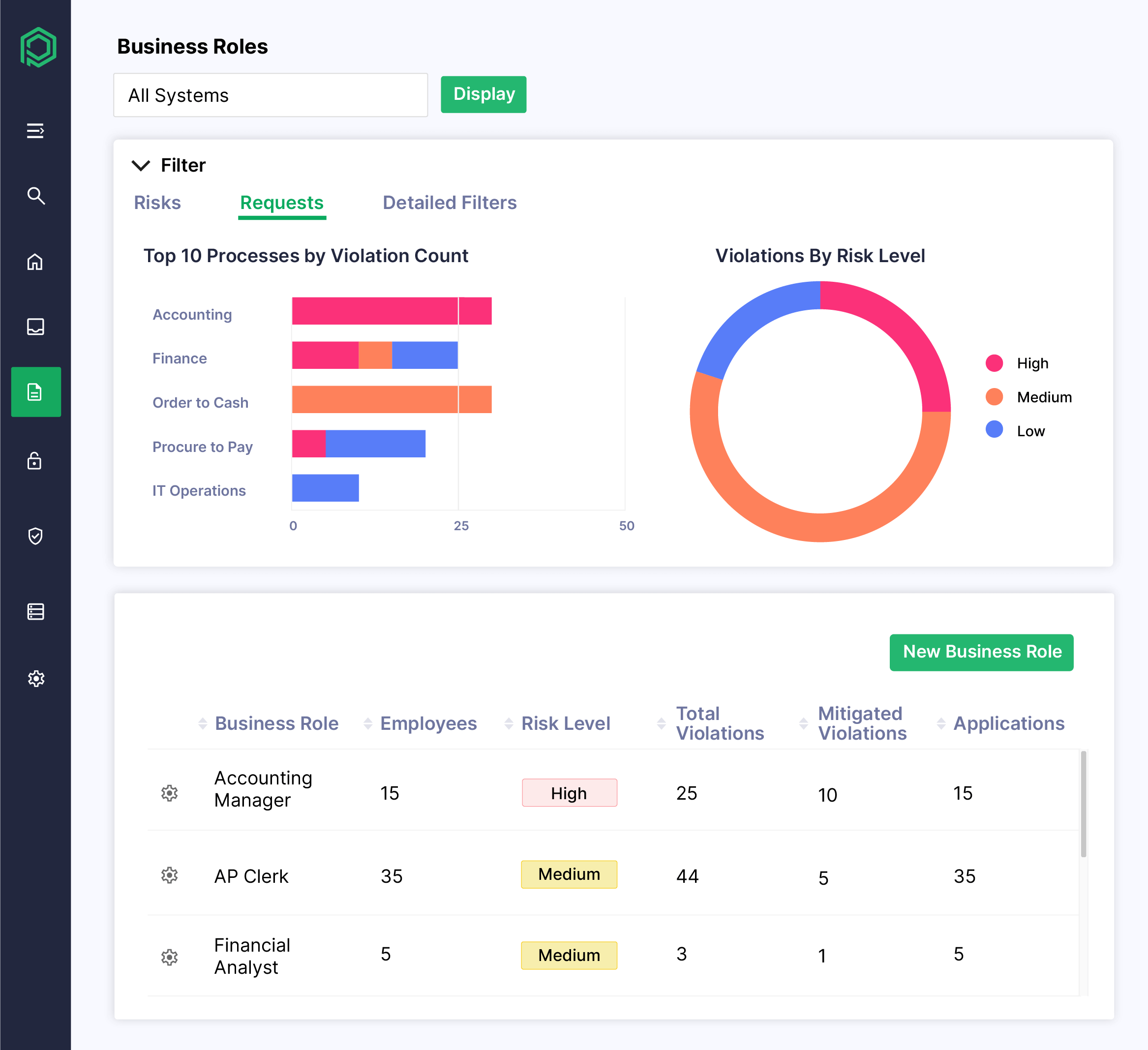
Reduce Risk and Role Management Complexity
- Run preemptive SoD and sensitive access checks during role creation
- Get guided suggestions for safer, more efficient role structures
- Track role assignments, usage trends, and change history
Fine-Grained IGA for More Then 100 ERPs and Business-Critical Apps
Don’t Take Our Word for It
“Pathlock gave us real-time visibility into access risk and automated our SoD analysis, eliminating guesswork and streamlining compliance.”

See Pathlock in Action

Analyze Access Risks and SoD Violations
Discover how Pathlock identifies real access risks across applications and helps you prioritize remediation with fine-grained SoD analysis.
Automate Compliant User Provisioning
See how Pathlock streamlines onboarding and access approvals with built-in policy checks, usage insights, and audit-ready workflows.
Accelerate Risk-Aware Access Certifications
Explore how Pathlock automates user access reviews, flags risky entitlements, and provides actionable data to enforce least privilege.
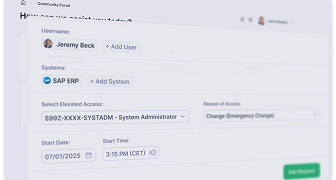
Control Privileged Access with Confidence
Learn how Pathlock manages time-bound elevated access, logs privileged activity, and prevents standing privileges across your systems.
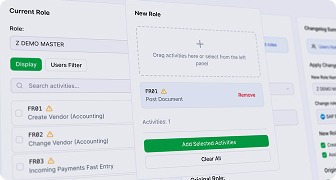
Proactively Manage Roles and Reduce Risk
Discover how Pathlock AI-powered role management tools help you simplify role design and reduce your organization’s risk exposure.