Click here to register for the July 27th live webinar Cyber Governance – Key Considerations for Navigating the New Normal to learn more.
What Is Cyber Threat Intelligence?
As the IT risk landscape continues to evolve and change at such as rapid pace, the ability to leverage threat intelligence big data in real-time provides organizations with a more proactive and preventative approach to security. The vast volumes and velocity of activity and transactional data that is being generated requires the ability to process it quickly and correlate across a variety of data in order to put the data in a context that is useful to the business in managing cyber-risks in a timely fashion. Critical capabilities include:
- Monitoring access activities within key business applications and across transactions for risk notifications and anomaly detection
- Identifying threat actors, their scenarios and behaviors
- Communicating with risk owners and key stakeholders to initiate workflows for remediation and mitigation of risk
With more data available for analysis, and better data context used in correlation rules analysis, we are now able to discover policy violations, inappropriate access or transactions and control failures that can lead to compliance issues and risks to business outcomes.
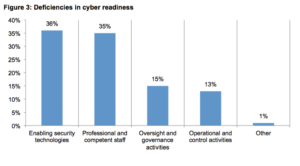
There has been much discussion with IT security practitioners about the need for advanced cyber threat intelligence. According to a SANS Institute survey, there is too much reliance on having SIEM platforms and manual techniques for analysis of the data. This approach has proved to be error prone and not able to put risks in a context that is meaningful to the business. As seen in recent Ponemon Institute research, the deficiency lies in the lack of enablement technologies that will provide this context.
Ponemon Research
Context-Aware Security
Context-aware security applies fine-grained, dynamic security policies based on a real-time analysis user activities supplemented with information about identity, role, events, conditions, location, behavior, application, device, data classification, time of day and more. These variable contextual factors are correlated to a baseline of normal or acceptable activity.
Security information and event management (SIEM) create logs of activity and events. Bu not all information sources are available to be monitored, and therefore, not all relevant information is collected and analyzed. Aggregating security data with other relevant process and/or transaction activity data increases the ability to correlate and detect user behaviors or events that will enable faster IT risk identification and prioritizes risks for remediation and mitigation.