If you do an internet search for the most common cause of data breaches, you’re going to get a variety of answers: ransomware, phishing attacks, stolen credentials, insider activity, etc. While these types of cyberattacks lead to data breaches, there is one simple truth ERP customers can never overlook: data breaches are caused by unauthorized access. Of course, not all unauthorized access is malicious. It can also be accidental due to poor access management (also called identity lifecycle management).
Clearly, the best practice is using the principle of least privilege to grant access to the applications, transactions, and data that a person needs to carry out their jobs. While data security and privacy are the primary elements of a successful access management process, the overall identity lifecycle management process should be automated, centralized, and provide IT teams and business units with audit-ready information. This information is critical for providing reasonable assurances that their SAP access management process is compliant and operating effectively.
Poor Access Management Exposes SAP Data To Risk
The process of SAP access management shouldn’t exist in a vacuum or a silo. Unfortunately, many organizations struggle with manual and decentralized identity lifecycle management. This leads to a variety of situations where unauthorized access leaves valuable ERP data exposed to risk:
- Unused new accounts with default passwords
- Employees collect new authorizations as they move around the business without removing unnecessary ones
- New employee authorizations causing SoD issues and sensitive access issues
- Employees leaving the company while their user IDs remain valid
- And many more
The identity lifecycle requires a process for controlling user access to critical information within an organization. The IT Infrastructure Library (ITIL) has a framework of best practices for access management: Requesting access, verification, providing rights, monitoring identity status, logging and tracking access, and removing or restricting access rights. But one department isn’t more responsible for the access management process than another, as outlined in this diagram:
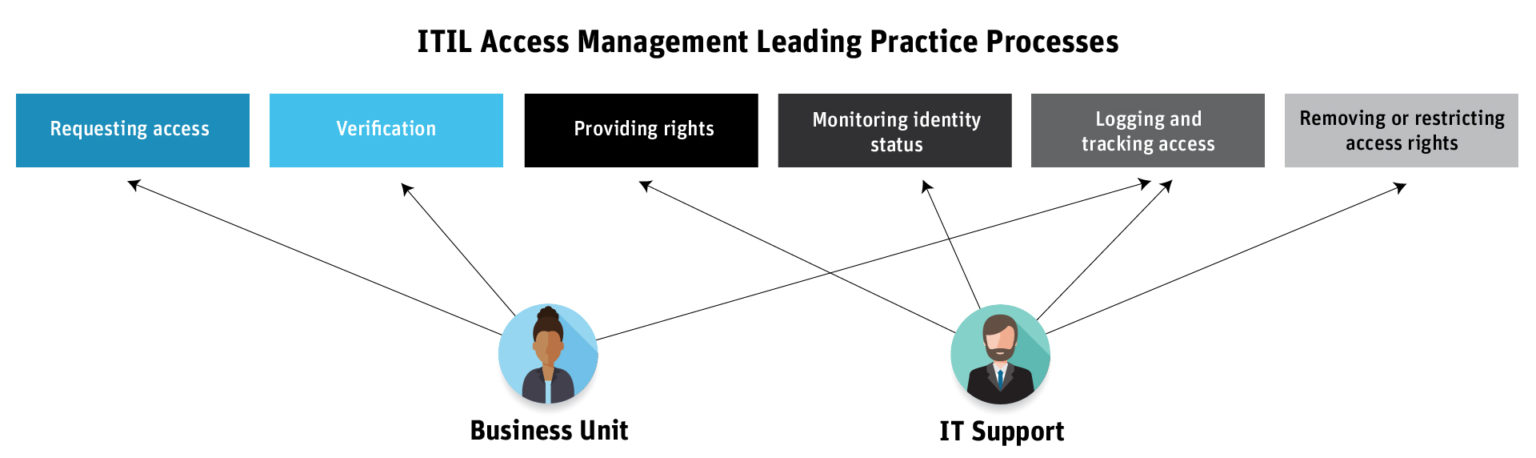
While business leaders are the first line of defense and are responsible for owning and managing their risks, those business unit leaders and the IT departments are responsible for assigning and monitoring user privileges in ERP systems. Unfortunately, existing access management processes are manual, siloed, and error-prone. For instance, HR might request access by emailing IT or using a self-service portal to create a request. IT might use a provisioning solution that’s included out-of-the-box with their ERP system. But this approach is still mostly manual and exists in siloes, requiring one unit to rely on each other for updates.
This less-than-optimal approach leaves organizations exposed to security and compliance issues. Increasingly, organizations are under regulatory pressure to prove they are protecting access to corporate resources. As a result, organizations can no longer rely on manual and error-prone processes to assign and track user privileges.
Audit-Ready Access Management
A poorly managed identity lifecycle process not only leads to security gaps but also visibility and compliance gaps.
As you can see from this illustration, all departments involved with access management will be audited to prove that their internal processes’ operating effectiveness sufficiently manages access risks, data security risks, and data privacy risks.
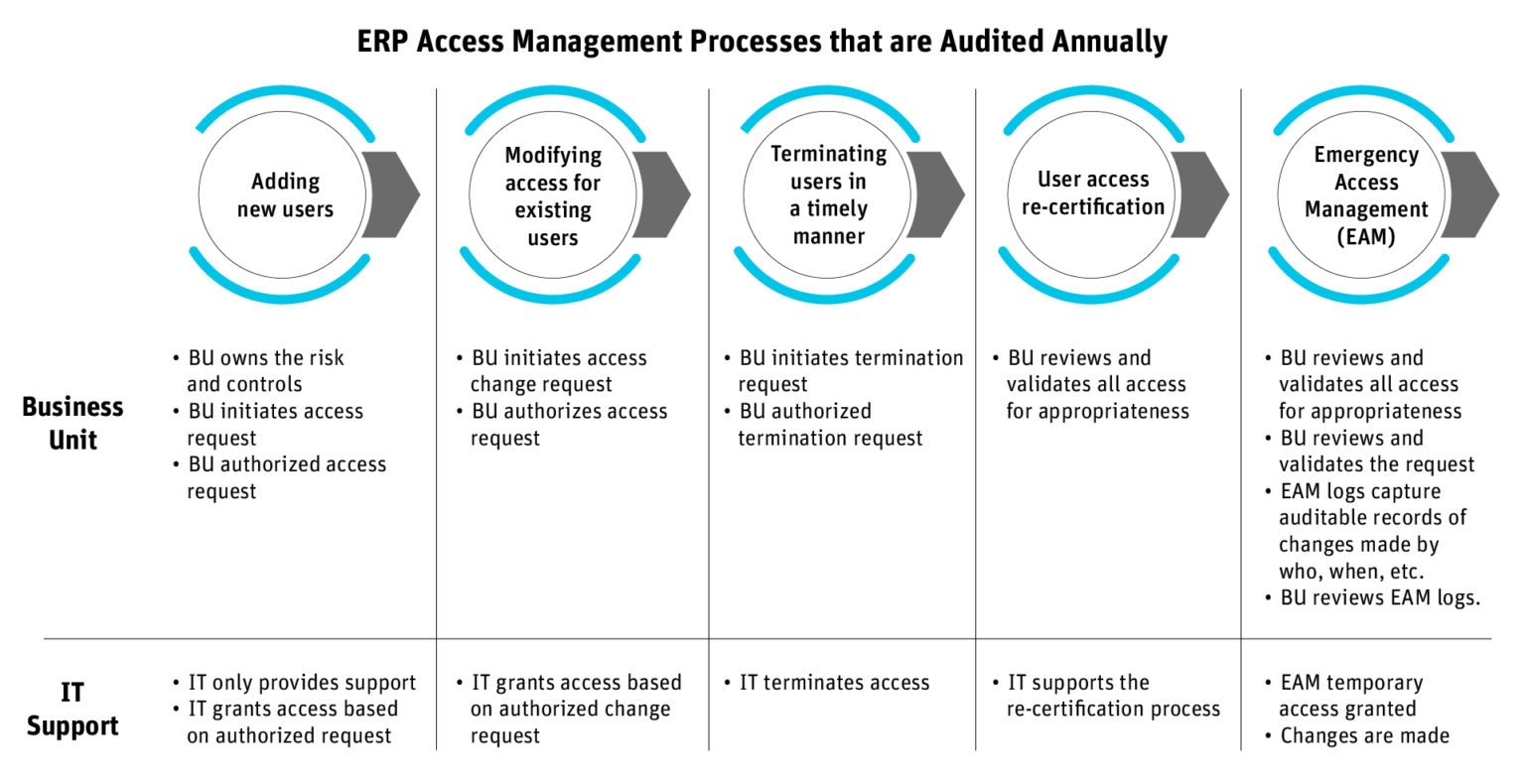
What’s missing for many organizations is an access management solution that centralizes and automates these tasks and enables granular access control and auditing of this process.
Automating And Centralizing Access Management With The Pathlock Platform
Taking control of SAP access management from the start is key to enforcing data security, maintaining internal and external compliance, and adhering to various regulations. With ProfileTailor GRC from Pathlock, you can easily organize, understand, and control the identity lifecycle process across your ERP landscape. Enabled by artificial intelligence, machine learning, and predictive analytics, it continuously identifies potential risks and provides optimized suggestions to streamline access management, including:
- Recommending the best alternatives when activities need to be removed from a user.
- Recommending the optimal segregation of roles to sub-roles according to business needs and actual usage. It automatically locks and removes the old authorization role from users who had it before the split.
- Solving SoD violations by replacing a user’s current roles without losing access to the activities actually needed.
- Choosing the optimal authorization role to grant users that enables them to perform additional activities without violating SoD policies.
Contact the SAP experts at Pathlock for a demonstration on how you can prevent unauthorized user access at the transaction and master data level.


