Governance, Risk, and Compliance (GRC) is an approach that organizations use to align their IT infrastructure and processes with broader business goals. It brings together governance, risk management, and compliance activities into a single, coordinated framework, encompassing the practical tools, policies, methodologies, and workflows that enable this unification to achieve business efficiency.
Organizations implement GRC frameworks to achieve three main objectives:
- Accomplish their business goals reliably.
- Address and minimize uncertainties in their operating environment to support confident decision-making.
- Meet industry standards and regulatory compliance.
By embracing a unified approach as an alternative to isolated, siloed practices, organizations can improve information sharing across business units, eliminate redundant work, and get real-time insights into operational efficiency, risk posture, and compliance levels.
It was in 2002 that the Open Compliance and Ethics Group (OCEG) first introduced the term ‘GRC’ in response to a new hype in regulatory and governance requirements. Then, in 2007, Scott Mitchell published scholarly research that framed GRC as “the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty, and act with integrity”, a concept known as Principled Performance. This influenced technology vendors to develop GRC software and consulting firms to assist organizations in implementing GRC practices. The development of open-source GRC standards allowed smaller firms to benefit from it.
Three Pillars of GRC

Before the GRC approach was unveiled, most businesses treated governance, risk, and compliance as separate functions. This often resulted in duplicated efforts, conflicting priorities, and gaps in oversight, which negatively impacted operational costs and GRC matrices. When different departments maintain separate risk registers and compliance trackers, it could result in inconsistent data and extra work to reconcile reports.
GRC brings these strands together into a single, coordinated framework that hinges on shared tools, reporting channels, and objectives. This enhances visibility, allowing leadership to see how a policy decision impacts risk levels and compliance obligations in real-time.
Let’s now look at the three pillars: G, R, and C.
Governance
Governance refers to the policies, guidelines, or framework that enable an organization to run its day-to-day business while supporting decision-making to achieve its business goals. It covers ethical standards, leadership structures, and responsibilities, setting the tone for accountability and transparency throughout the organization.
Core elements of good governance include:
- Clearly defined stakeholder responsibilities that outline the roles of the board, senior management, and other key parties.
- Commitment to corporate social responsibility to ensure that company policies reflect ethical practices.
- Completeness, reliability, and timely delivery of critical data required for decision-making.
- Transparent information sharing and open communication across hierarchical levels and departments.
- Robust internal controls and systems to maintain oversight, track performance, monitor the effectiveness of strategic plans, and ensure compliance with both internal policies and external regulations.
- Operational controls spanning physical and digital infrastructure, including data centers and critical applications.
- Strategic allocation and monitoring of financial, human, and technological resources.
- Alignment of job descriptions with lines of business (LOBs) and performance assessments.
- Fair distribution of responsibilities, rights, and rewards.
- Accountability for conduct and results, promoting ethical behavior and responsible corporate citizenship.
- Protection of the rights of management, employees, suppliers, and investors.
- Established conflict-resolution procedures.
Risk Management
Risk management involves identifying and assessing risks that can hinder your business objectives and implementing controls to prevent and mitigate their impact. It is both proactive, by identifying emerging threats, and reactive, by having contingency plans in place. Risk is best managed when people, processes, and technology work together to reduce the likelihood of occurrence and mitigate its impact.
Organizations have to manage many types of risks, including:
- Financial: market volatility, credit issues, cash-flow challenges
- Legal: lawsuits, regulatory penalties, or contractual disputes
- Strategic: poor business decisions or lack of adaptability to market changes
- Security: cyberattacks, data breaches, and other information-security threats
- Technological: system failures, outdated infrastructure
- Commercial: high customer concentration, pricing pressures
- Operational: supply chain disruptions, property damage, product or food safety issues, workplace health and safety (WHS) concerns, asset-maintenance failures
Effective risk management delivers substantial benefits and ensures long-term success. It protects an organization from uncertainty by identifying potential threats early and addressing them before they escalate. This translates into reduced costs, as fewer incidents mean fewer losses and fewer emergency responses.
Key activities include:
- Predicting potential problems and minimizing losses.
- Identifying and remediating risks before they escalate.
- Monitoring infrastructure risk, from facilities to digital networks.
- Spotting operational or technological failures that could disrupt service.
- Conducting targeted risk assessments, for example, to evaluate security loopholes or network weaknesses.
- Assessing system performance and effectiveness to verify that controls are working.
- Weighing stakeholder expectations for prioritizing risk.
- Providing reliable, timely risk-related information to executives, regulators, and other stakeholders.
- Meeting legal, contractual, internal, social, and ethical requirements to stay compliant.
Compliance
Compliance ensures that the organization adheres to external regulations and internal policies. This may involve complying with data-privacy laws, such as HIPAA, as well as environmental regulations and industry-specific standards, while also enforcing the company’s own rules, procedures, and code of conduct.
Key activities under compliance include:
- Identifying all applicable regulations.
- Evaluating the risks and costs of non-compliance compared to the cost of achieving compliance.
- Implementing procedures and controls to ensure that business processes comply with external regulations.
- Auditing the organization’s current level of compliance and any gaps.
- Keeping compliance documents up to date.
- Initiating corrective actions when issues arise.
- Producing clear, accurate compliance reports for stakeholders and regulators.
To undertake these activities, organizations must bear financial, strategic, and operational responsibilities. Yet they are worth the effort as compliance is critical to long-term success. Failure to comply can lead to poor performance, costly mistakes, penalties, and even lawsuits.
What is ITGRC?
IT governance, risk, and compliance (IT GRC) ensures that a company’s technological environment supports day-to-day operations and is adaptable to future business needs. It provides a framework for managing IT resources responsibly, adhering to all applicable regulations, standards, and internal policies.
IT GRC integrates with overall risk, governance, and compliance in the following ways:
- It aligns IT strategies with overall business goals. This means that IT decisions, such as selecting new software or expanding infrastructure, are guided by the company’s broader strategy and contribute to achieving business objectives.
- IT GRC identifies, assesses, and reduces risks like cyberattacks, system outages, and data breaches before they disrupt operations. In this way, it helps manage technology-related risks.
- It helps the organization meet IT-specific regulatory requirements, such as GDPR in Europe and HIPAA in the US, for healthcare data.
To keep technology risks under control and ensure compliance, IT GRC concentrates on several critical areas, such as:
- Prioritizing data security through encryption, secure backups, and access controls.
- Managing software vulnerabilities with regular patching and timely updates.
- Enforcing strong password policies and MFA to prevent unauthorized entry.
- Performing assessments to ensure that servers, networks, and applications remain efficient, reliable, and scalable.
- Keeping up with emerging laws and standards, such as evolving privacy rules or industry-specific cybersecurity frameworks, and adjusting policies as needed.
A GRC-based approach enhances information sharing across departments, reduces costs by preventing incidents, and lowers the risk of regulatory violations. Eventually, it fosters stakeholder trust and supports sustainable growth. Rather than being a burden, GRC strengthens day-to-day operations and makes organizations more resilient and adaptable.
Four Core Components of GRC
GRC emphasizes four key components: strategy, processes, technology, and people.
- Strategy sets the vision and risk priorities
- Processes turn that vision into policies and controls.
- Technology automates monitoring and reporting.
- People carry out the framework and uphold a culture of accountability.
In this context, GRC relies on collaboration among stakeholders, a structured framework, and an understanding of the organization’s GRC maturity level for optimal performance.
Stakeholders
GRC is not the job of a single department. It requires active engagement between teams. Internal audit, security specialists, department heads, the executive suite, and even the board all play a role.
- Senior executives weigh risks when making strategic decisions.
- Legal teams focus on reducing legal exposure and ensuring compliance with regulations.
- Finance managers support regulatory reporting and financial controls.
- Human Resources protects sensitive employee and recruitment data.
- IT teams safeguard systems against cyber threats.
This cross-functional collaboration ensures that risk management and compliance efforts are consistent and effective.
GRC Framework
GRC is a framework that provides a structured model for managing governance, risk, and compliance activities.
- It is about identifying and implementing policies that enable a company to achieve its goals and objectives.
- It also promotes an initiative-taking approach to identifying and mitigating risks.
- It helps decision-makers make well-informed choices and maintain business continuity.
- Stakeholders apply this framework to coordinate policies, workflows, and governance processes.
To support these efforts, companies usually deploy specialized software and monitoring tools that track progress and measure success.
GRC Maturity
GRC maturity reflects how well an organization intertwines governance, risk management, and compliance into everyday operations. A mature GRC program features strong coordination and efficient processes, resulting in cost efficiency, higher productivity, and effective risk mitigation. In contrast, a low-maturity environment features departments working in silos, resulting in duplicated efforts, poor productivity, and ineffective risk management. Understanding maturity levels enables organizations to plan improvements and prioritize resources effectively.
GRC Capability Model (OCEG Red Book)
The GRC Capability Model, also known as the OCEG Red Book, provides practical guidelines for implementing Governance, Risk, and Compliance to achieve business goals while addressing uncertainty and acting with integrity. It fosters a shared understanding of policies, communication, and training needs, while also providing GRC professionals with a roadmap to plan, assess, and enhance their GRC capabilities.
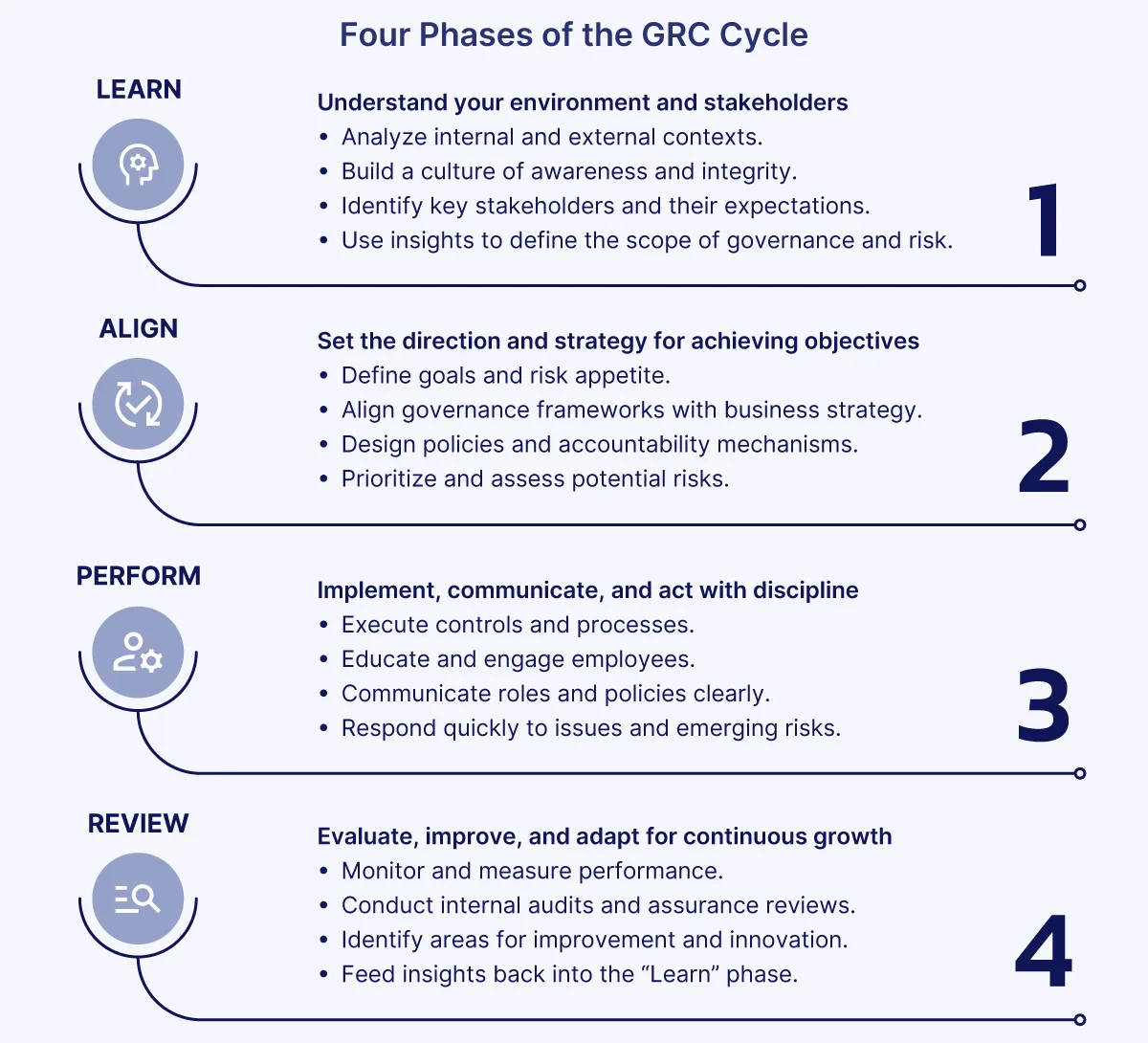
The GRC Capability Model has four components:
- Learn: Begin by understanding the organization’s context, values, culture, and key stakeholders. Use these insights to set clear objectives and devise strategies and actions to achieve them.
- Align: Make sure objectives, strategies, and day-to-day actions all point in the same direction. This unidirectional alignment is possible through effective decision-making that considers opportunities, threats, values, and requirements.
- Perform: Execute the strategies and actions that drive desired results while preventing or correcting unwanted outcomes. Ongoing monitoring helps detect changes and issues as early as possible.
- Review: Regularly review the objectives, strategies, and actions to affirm that they remain effective and appropriate to business goals. For example, a new regulation might require policy updates or a shift in approach to stay compliant.
GRC Implementation Challenges
Rolling out a GRC program requires getting people on board, communicating effectively, and having good data management practices.
Organizations often encounter the following hurdles:
Change Management
GRC reports provide timely insights to leadership, enabling informed decision-making in a fast-paced business environment. To put those insights into practice, organizations need a robust change management program that allows teams to adapt quickly.
Data Management
Many organizations still operate in silos, where each department generates and stores its own data. A successful GRC program relies on combining this information. This can lead to duplicate records and complex data-management challenges if there is no proper data integration strategy in place.
GRC Integration into Business Activities
An effective governance, risk, and compliance framework ties business activities directly to governance, risk, and compliance processes. Without seamless integration, implementation can become fragmented and may not deliver the intended benefits.
Integration with Legacy Systems
Many companies run on older applications and infrastructure. It can be technically challenging and time-consuming to integrate these legacy systems with modern GRC platforms.
Culture Propagation
Establishing a company-wide culture of ethical behavior requires considerable effort. Senior leadership must embody the desired standards and ensure that the message reaches every level of the organization.
Clarity in Communication
Successful GRC implementation depends on transparent, easy-flowing communication between compliance teams, stakeholders, and employees. This is essential to policy making, planning, and decision-making.
User Adoption and Training
Even the best GRC tools will fail if employees do not use them properly. User adoption depends on well-planned training, intuitive interfaces, and continuous support.
Resource and Budget Constraints
GRC initiatives can require significant investment in technology, training, and ongoing oversight. Limited budgets can delay projects or lead to inadequate solutions.
Evolving Regulatory Landscape
Regulations often vary by region and industry. Failing to keep policies, controls, and reporting aligned with these changes can strain resources and lead to compliance gaps.
How to Implement an Effective GRC Strategy
An effective GRC strategy begins by uniting business areas, such as operations, finance, IT, and legal, under a single cohesive framework. However, implementing this strategy is not a one-time effort. Risks, regulations, and industry standards are constantly evolving. Therefore, it is essential to evaluate and refine your GRC strategy regularly.
Here are some steps to guide your GRC implementation.
Define Clear Goals
The first step is to decide what goals you want to achieve with GRC. For example, do you want to reduce the risk of non-compliance with data privacy laws or strengthen cybersecurity?
Assess Existing Practices
Next, review your current governance, risk, and compliance processes as well as the tools being used to understand how well they meet your organization’s needs. During this assessment, look for areas of shortcoming, such as outdated technology, creating gaps in regulatory compliance, or weak third-party controls. Use what you have learned to select the most appropriate GRC frameworks and software.
Secure Executive Support
Senior executives play a central role in a successful GRC program. For them to champion this initiative, they must first understand and appreciate the benefits of a comprehensive GRC implementation. By setting clear GRC policies and promoting their use across the organization, top leaders lay the groundwork for success. This approach then cascades down to every level in the organization.
Define Roles and Responsibilities
GRC is a team effort. While executives set the policy, departments such as legal, finance, and IT are responsible for ensuring the program’s success. Each stakeholder must be assigned clear roles and responsibilities, so that everyone knows their tasks. This fosters a sense of ownership that encourages people to ensure everything is working well and raise any concerns promptly.
Test the GRC Framework
It is best to test the GRC framework within a single business unit or process to see if it addresses your issues and how well it meets your goals. Use the results to identify gaps or areas for improvement, then refine the framework before rolling it out across the entire organization.
Adopt GRC Technology
Relying solely on word processors and spreadsheets to manage a GRC program means endless manual tracking, which is prone to error and difficult to audit. It also makes it difficult to get real-time insight and generate quick reports. That’s where a dedicated GRC technology comes in. GRC software can manage and monitor an enterprise-wide GRC program, providing a complete view of processes, resources, and records. This makes it easier for organizations to track risks and ensure compliance with relevant regulations.
GRC Market Segmentation
A GRC program can target a single business area, such as IT or finance, or operate as a fully integrated function across the enterprise. The latter approach utilizes a standard library of controls that align with all key governance factors. This consolidation reduces the likelihood of repeated efforts, simplifies oversight, and ensures that every department operates under the same set of standards.
Now, let’s examine the most common individual GRC areas.
- Financial GRC encompasses the activities that ensure that financial processes run correctly and meet finance-related regulations.
- Operational GRC covers day-to-day business activities such as property and product safety, food safety, IT compliance, and asset maintenance. It has the following subsets:
- Workplace Health & Safety (WHS) GRC focuses on all activities related to workplace health and safety.
- IT GRC ensures that technology infrastructure supports current and future business needs while complying with cybersecurity and data-privacy mandates.
- Legal GRC coordinates all components of GRC through the legal department and the Chief Compliance Officer.
The boundaries between the various sub-segments of the GRC market are not clearly defined. For example, the Australian Institute of Company Directors (AICD) groups enterprise risks into three broad categories: financial risk, operational risk, and strategic risk.
Gartner, on the other hand, segments the GRC market into: finance and audit GRC, IT GRC management, and enterprise risk management. It further divides the IT GRC management market into these capabilities:
- Controls and policy library
- Policy distribution and response
- IT controls self-assessment and measurement
- IT asset repository
- Automated general computer control (GCC) collection
- Remediation and exception management
- Reporting
- Advanced IT risk evaluation and compliance dashboards
Market Segmentation for GRC Product Vendors
Given the unclear distinctions between the sub-segments of the GRC market and the lack of agreement among analysts on market segmentation, it can be challenging to determine the best software product for a given business. That said, the vendor market is diverse and sometimes overlapping, but it exists in three segments:
| GRC Vendor Market Segments | Description |
|---|---|
| Integrated GRC solutions | These provide enterprise-wide coverage, managing governance, risk, and compliance through a single library of controls. Governance, risk, and compliance are managed, monitored, and presented against every governance factor. |
| Domain-specific GRC solutions | These specialize in one governance area, such as finance. They connect governance, risk, and compliance within that area only. |
| Point solutions | They focus on addressing only one area within GRC, which can be either enterprise-wide governance, enterprise-wide risk, or enterprise-wide compliance, but not all of these in combination. |
GRC Data Warehousing and Business Intelligence
Integrated GRC solutions now also come with a custom-built GRC data warehouse and business intelligence capabilities. These features enable companies to aggregate and analyze data from other GRC applications, helping them identify risks earlier, improve controls, and compare high-value data across different systems. This approach enables organizations to retain their specialist applications while transitioning towards an integrated GRC strategy, beginning with unified reporting.
What are GRC Tools?
GRC tools are software applications that help organizations manage policies, assess and mitigate risk, control user access, and maintain regulatory compliance. These tools reduce costs and improve operational efficiency.
Modern GRC platforms offer the following functions and features:
- Content and document management to create, track, and store digitized policies and records.
- Risk data management and analytics that measure, quantify, and predict risk while guiding on how to manage it.
- Workflows to establish, execute, and monitor GRC processes.
- Policy and control management to create and distribute policies, map them to regulations, and assess how healthy controls are deployed and functioning.
- Audit management that organizes information and facilitates internal audits.
- Collaboration features enabling different business units to coordinate on a single platform.
- Regulatory updates to stay current with changing requirements.
- Pre-built templates for quick setup and easy customization.
- Real-time dashboards for monitoring key performance indicators (KPIs).
Deploying GCR software may not be a straightforward process, but the effort is worthwhile. Companies have reported improved decision-making, lower compliance costs, and quicker responses to risks and regulations.
Four Categories of GRC Tools
GRC tools fall into the following four categories:
| GRC Tool Categories | Description |
|---|---|
| GRC Software Platforms | These are all-in-one GRC software platforms that automate the GRC framework across the enterprise. They manage controls, align policies across departments, facilitate collaboration across business units, track risk, automate workflows, ensure compliance, simplify internal audits, generate real-time reports, and keep teams updated on regulatory changes. |
| User Management Systems | These tools enforce secure access to corporate resources by implementing fine-grained authorization policies, ensuring that users have access only to the data and applications necessary to perform their jobs. |
| Security Information and Event Management (SIEM) | SIEM tools detect potential cybersecurity threats by collecting and analyzing security event data. IT teams utilize them to close security gaps and comply with privacy regulations. |
| Auditing Tools | Auditing solutions enable organizations to evaluate the effectiveness of their GRC programs, conduct internal audits, and compare the results with their organizational goals. They help determine whether the GRC framework is performing as intended and where improvements are needed. |
How Pathlock Can Help in GRC Implementation?
Pathlock Cloud
The Pathlock Cloud platform is a suite of identity governance, access risk, and compliance solutions that help organizations automate controls, manage access, and monitor risks across business applications. Its GRC-oriented capabilities includes:
- Application Access Governance / Identity Governance: Pathlock Cloud provides fine-grained access control, role management, and automated provisioning/deprovisioning that aligns with compliance requirements.
- Continuous Controls Monitoring: It helps organizations test and enforce internal controls, thereby maintaining compliance with regulatory frameworks.
- Compliance Framework Support: It supports compliance with multiple regulations and frameworks, such as SOX, GDPR, and HIPAA, through out-of-the-box controls and rulesets.
- Enhancements to SAP GRC: Suppose you already have SAP GRC in place. In that case, Pathlock can extend or enhance it by adding attribute-based access control (ABAC), providing better real-time analytics, and integrating with non-SAP systems.
- Audit-Ready Reporting & Dashboards: The platform provides dashboards, customizable reports, and visualizations that offer valuable insights for GRC programs.
Conclusion
Here’s the reality: GRC is not going anywhere. As regulations become stricter and risks increase, GRC compliance will only become more complex and critical to business survival. Implementation is indeed challenging, and the market is fragmented.




