Oracle Access Management offers single sign-on (SSO) and multi-factor authentication (MFA) that integrate systems and identities across on-premises and cloud locations. You can deploy this solution as an on-premises image or in Oracle Cloud Infrastructure (OCI). The service enables access control for enterprise platforms, enforcing policies regardless of the user’s location and device.
Understanding Oracle Access Management Services
Oracle Access Management is a Java EE-based security application that offers web-perimeter security functions and SSO services, such as identity context, policy administration, authentication and authorization, testing, auditing, and logging.
It employs shared platform services, such as Identity Context, session management, risk analytics, and auditing. The image below illustrates how Oracle Access Management leverages Oracle Identity Management technologies:
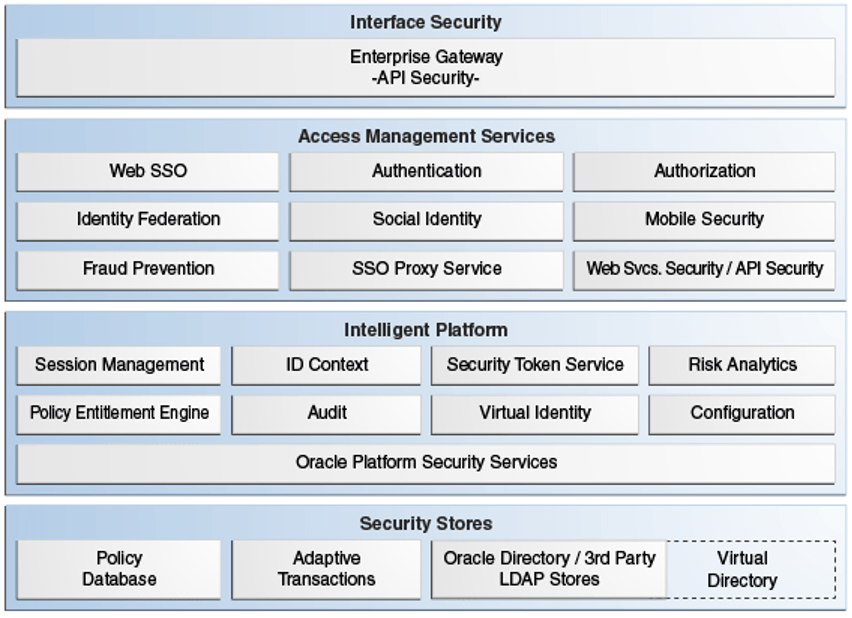
Here are key Oracle Access Management services:
Identity Federation
The Identity Federation service employs open federation protocol standards, like OpenID and SAML, to provide cross-domain SSO.
Security Token Service
This service facilitates access to services beyond organizational boundaries and across security domains through token validation and generation.
Management Mobile and Social
This service serves as an intermediary between a user attempting to access protected resources and any back-end identity and access management (IAM) service that protects these resources.
Oracle Access Portal
This SSO proxy service enables extranet and intranet applications to use Oracle’s form-fill SSO technology.
The Adaptive Authentication Service
This service provides a one-time password authenticator providing multi-factor authentication. It offers a framework for adding custom second-factor authentication that accepts PINs from users.
OAuth Services
This service lets you implement the OAuth 2.0 authorization protocol in Oracle Access Manager. It enables access to resources protected by Access Manager belonging to a different resource owner.
Identity Context
This service offers context-aware security policy management. It enables you to use Oracle Identity Management security frameworks to control the security level imposed in an application.
Oracle Access Management Access Manager
Oracle Access Manager is a key part of the Oracle Access Management platform, allowing you to leverage Oracle Fusion Middleware SSO capabilities. Access Manager SSO eliminates the need for users to sign in separately to each application, allowing them to authenticate once and access multiple applications.
You must use a web gate to protect your application server, web server, or third-party app before enabling SSO. The web gate must be registered with Access Manager. You can define the authentication and authorization policies to secure your resources, with the web gate serving as the agent that enforces these policies by filtering HTTP requests.
Web apps already using Oracle ADF Security or OPSS SSO can be easily integrated with Access Manager, which sits on an Oracle WebLogic Server instance. You might use multiple Access Manager deployments for your organization.
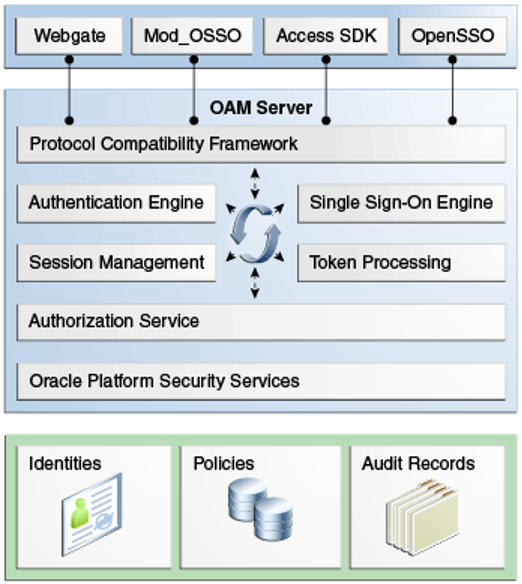
Oracle Access Management Authentication
Oracle Access Management offers an OAuth service that lets you implement the OAuth 2.0 authorization protocol in Access Manager environments. OAuth lets users access resources owned by another user and protected by Oracle Access Manager (OAM). It handles the authorization process.
OpenID Connect (OIDC) acts as an extension to OAuth, implementing the authentication process. It generates easily consumable ID tokens, which users can obtain via OAuth 2.0 flows.
OIDC adds an identity layer to the OAuth 2.0 protocol, allowing you to verify end-user identities and retrieve profile information. It uses the authentication carried out by the authorization server and supports interoperable, REST-like workflows.
Using Identity Context In Oracle Access Management
Identity Context provides context-aware authorization and policy management capabilities, allowing you to address the changing security threat landscape. These built-in Oracle Access Management capabilities let you secure access to resources using a combination of conventional access controls and dynamic data.
Identity Context retrieves data from the authentication and authorization processes, providing insights into authentication strength, device trust, and risk level. Access Manager incorporates Identity Context to enable context-based access management.
The following diagram outlines the Identity Context workflow, involving several application delivery components with dedicated security infrastructure:
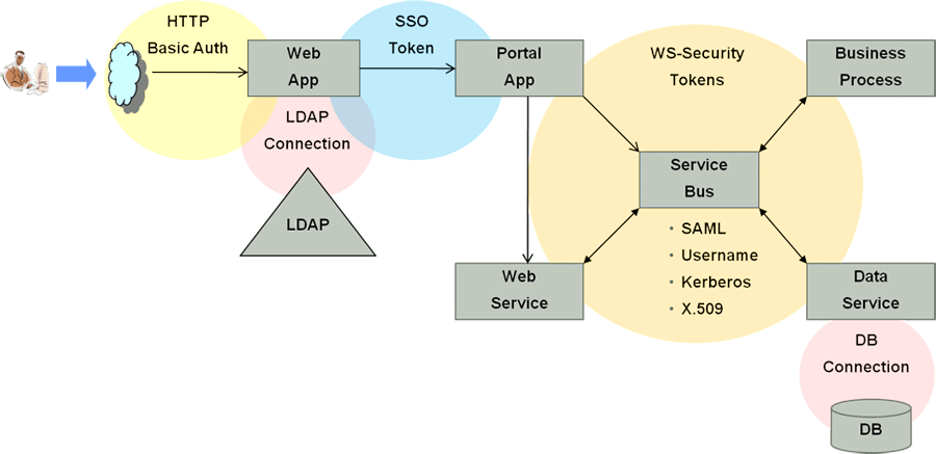
Each component has a security policy to protect its specific application part. Administrators define the authorization policies to govern access to protected resources, which Access Manager enforces during runtime. You can use an external authorization server like Oracle Entitlements to manage the policies of some or all these components—this applies to applications built using Oracle Platform Security Services.
The use case depicted here includes:
An end-user device—the origin of the access request.
A web server—runs static graphical user interface (GUI) pages.
An application server—runs the portal server to render dynamic content.
A service bus—exposes the web service endpoint.
A database server—contains transactional data.
A Lightweight Directory Access Protocol (LDAP) server—contains identity profile information.
The following diagram outlines Identity Context’s functional architecture, including its Oracle applications:
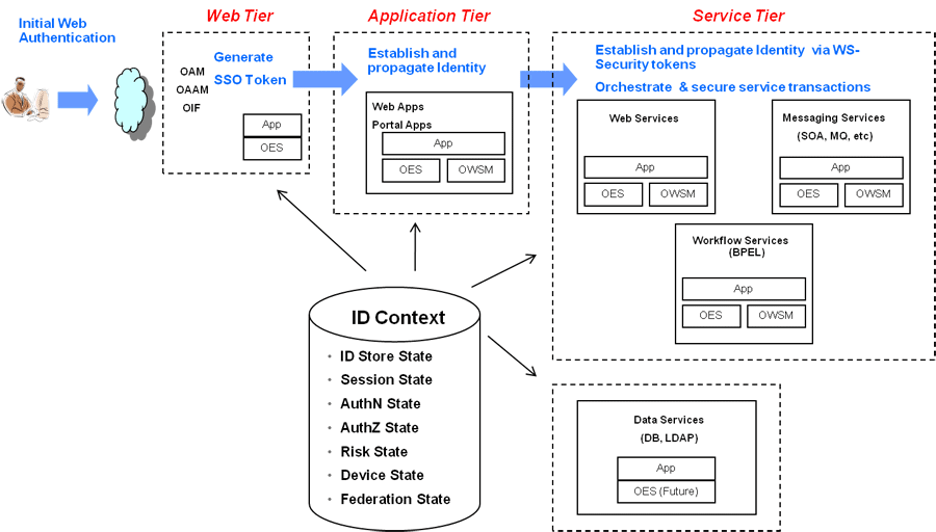
This architecture leverages the Oracle Access Management platform to manage security policies while maintaining context awareness. It provides native support for managing and enforcing attributes in Identity Context, such as authentication data, trusted device data, and risk score.
Identity Federation In Oracle Access Management
Federation involves merging several parties or groups. A federated environment establishes trust between multiple identities to enable safe access to protected resources. Identity federation helps protect resources against unauthorized access.
Oracle Identity Federation provides capabilities for creating federation and safely sharing services and data across security domains. The Identity Federation server is integrated with Oracle Access Manager to eliminate the need to install and maintain multiple servers.
Integrating the two services also simplifies the post-install configuration of federation features, allowing you to access federation features via the Oracle Access Management Console. It helps improve the scalability of the two services and enhances diagnostics and troubleshooting.
Oracle ERP Security With Pathlock
Pathlock’s suite of Oracle solutions is designed to protect your Oracle applications by automating user authentication (SAML SSO), safeguarding sensitive data, and identifying SoD violations with on-demand audits. Pathlock also provides granular insights to remediate threats and comply with SOX, CCPA, and GDPR.
Contact us to learn more about Pathlock’s Oracle-focused ERP solutions.


