Protect Your Critical Data from Insider and External Threats
Pathlock’s provides the industry’s most robust platform to enforce compliant policies for the handling of sensitive data like credit card numbers, personal information, health and employment data, and more.


Create Compliant Data Governance Policies Based on Real Security and Compliance Risk
Whether it’s locating and remediating sensitive data lost in the cloud, dynamically masking and anonymizing personal data at the column-level, or automating user deprovisioning for high-risk individuals, Pathlock has every capability you need to create and enforce enterprise-wide data governance policies that ensure compliance with privacy regulations.
Pathlock provides the industry’s most robust library of compliance controls for business-critical applications. This controls library is aligned with data security mandates and frameworks such as PCI, HIPAA, GDPR, CCPA, and more.
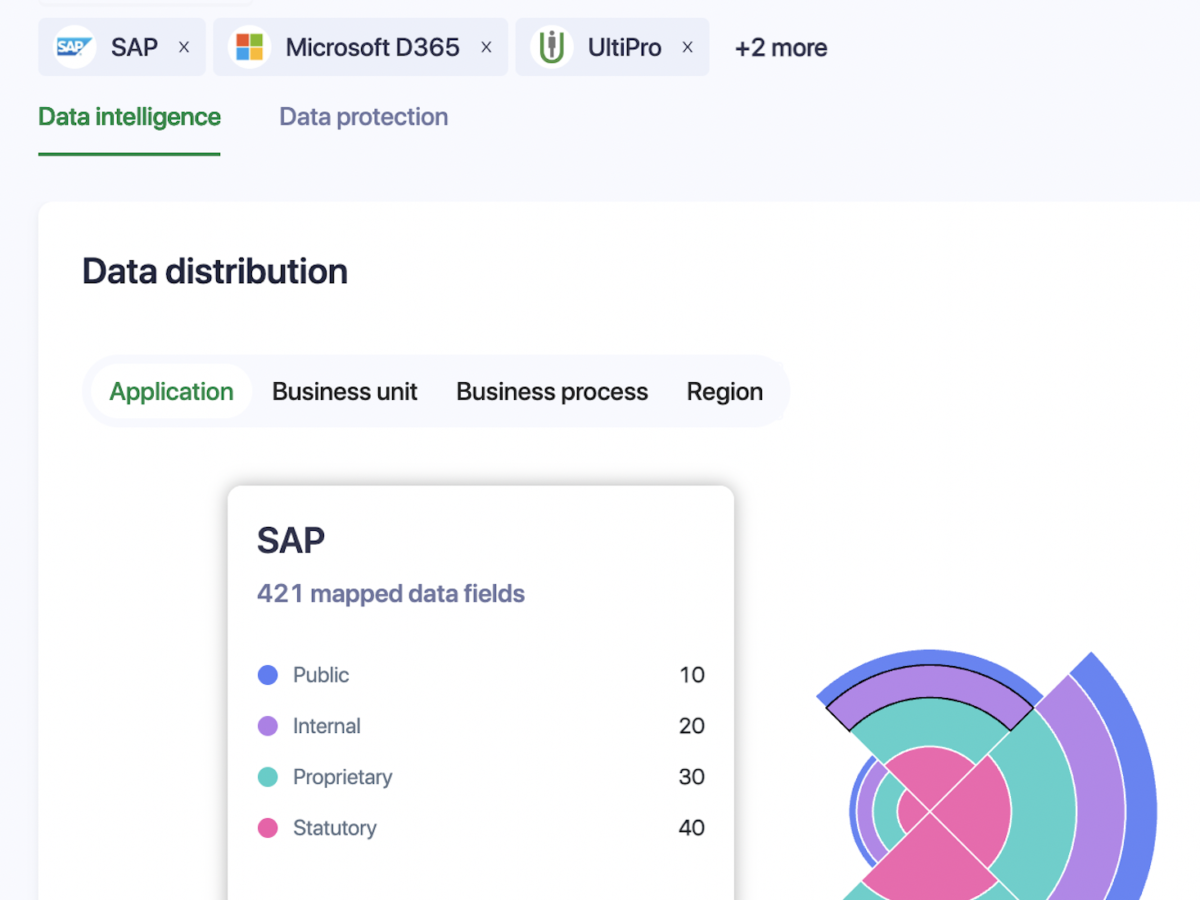
Automate Compliance for GDPR, PCI, HIPAA, CCPA, ISO 27001, and More

![[Webinar] Microsoft Entra ID Governance: How to Create Efficient and Secure Access Management Across Your Entire Business Landscape](https://pathlock.com/wp-content/uploads/2025/06/Screenshot-2025-06-18-at-3.24.10 PM-294x178.png)
![[Webinar] Fix Oracle Risk and Compliance Gaps Before They Cost You — With One Platform](https://pathlock.com/wp-content/uploads/2025/06/videocovermain-294x178.png)
![[Webinar] What a Former FBI Agent Wants Every Healthcare Security Team to Know](https://pathlock.com/wp-content/uploads/2025/06/fbi-294x178.png)
![[Webinar] Zero Trust for Export Controlled Information in SAP](https://pathlock.com/wp-content/uploads/2025/05/Screenshot-2025-05-23-at-11.53.14 AM-294x178.png)
![[Webinar] From ‘Oh No’ to Go-Live: De-Risk Your SAP Role Migration](https://pathlock.com/wp-content/uploads/2025/05/videocoverroledesign-294x178.png)


![[Webinar] Governance on Autopilot:Automate Compliance & Take Control of ERP Security](https://pathlock.com/wp-content/uploads/2025/04/heroimage1-294x178.png)