Internal controls are the policies, procedures, and systems that an organization establishes with the primary goal of ensuring the accuracy and reliability of its financial reporting. By-products of this control system include operational efficiency and protection of the organization’s assets. Controls are a way to keep a close check on a company’s day-to-day activities. This helps prevent mistakes, catch fraud, and keep everything running smoothly in line with internal policies and external regulations.
It is the responsibility of the top management to ensure that internal control systems are properly designed, implemented, and monitored across the organization. The first step is to encourage a culture that is built on accountability, ethical behavior, and transparency. It is this culture and commitment that shape how employees view compliance and risk.
Control Categories
Internal controls fall into three broad categories, based on how they are implemented.
- Administrative Controls: These are the rules, policies, and procedures that guide how people should behave to keep things secure.
Examples: Security policies, staff training, and background checks.
- Physical Controls: These are tangible measures that protect people, equipment, and facilities from harm or unauthorized access.
Examples: Locks, security guards, fences, CCTV cameras, access badges.
- Technical (Logical) Controls: These are usually software-based controls that use technology to secure systems and data.
Examples: Firewalls, encryption, antivirus, and authentication systems.
Control Types
Two types of internal controls are:
- Primary controls that directly address risks.
- Supplementary controls that support or strengthen the overall control environment.
Organizations must consider both these types of controls to design a balanced and practical internal control system.
Primary Control Types
These are the “frontline” controls that directly work to prevent or detect issues. They are integrated into an organization’s routine operations and are responsible for protecting assets, ensuring financial accuracy, and reducing risks.
Primary controls include:
| Types of primary controls | Description | Examples |
|---|---|---|
| Preventive Controls | These controls are designed to prevent problems, such as errors and fraud. | Requiring approvals before large payments. |
| Detective Controls | Also known as mitigating controls, these controls identify errors, irregularities, and other issues after they occur, so that they can be corrected. They identify risk areas that require new or stronger controls. | Monthly account reconciliations |
| Corrective Controls | These controls are implemented in response to errors or irregularities that occur. They address and fix problems to prevent them from resurfacing. | Restoring data from backups after a system failure. |
Supplementary Control Types
Supplementary controls are like the “support crew” behind the scenes. They do not directly act on risks but make the primary controls stronger and more reliable.
| Types of supplementary controls | Description | Example |
|---|---|---|
| Directive Controls | These controls give clear direction to people. They guide employees’ behavior on what to do and what not to do to prevent issues and undesired actions. | Management directives, company policies, standard operating procedures. |
| Deterrent Controls | They discourage undesirable actions or policy violations, usually by establishing consequences for violations. | Warning signs, penalties, and CCTV cameras installed in visible areas. |
| Compensating Controls | They act as a cover to provide an alternative when primary controls are absent, weak, or temporarily unavailable. They wouldn’t replace core controls, but can manage risk reasonably. | Using manual invoice verification when an automated payment approval system is temporarily down |
| Recovery Controls | These controls enable organizations to restore operations after a failure or incident. They are usually part of corrective measures or disaster recovery strategies. | Data backups, disaster recovery plan. |
Comparison of Key Controls
Not all controls work the same way. Some are there to stop problems before they happen, others are meant to warn or guide people, and some spot and fix issues after they happen.
Preventive vs. Deterrent Controls
Preventive controls block an inappropriate action by implementing physical and procedure-based checks. Consider the example of a locked door to the server room that prevents unauthorized entry.
Deterrent controls, on the other hand, do not physically stop the action but tend to influence behavior. For instance, a “No Entry” sign warns people, but they can choose to follow or ignore it.
In short:
- Preventive: The act is made impossible with no choice for the intruder. Violations can lead to serious consequences.
- Deterrent: The intruder is given a warning, but can choose to proceed or not.
How Detective and Corrective Controls Connect
Detective controls identify issues after they occur, such as security cameras capturing unauthorized access or a system flagging suspicious transactions. But catching the issue isn’t enough. Detective findings must lead to corrective actions. Without that link, the same issue could happen again. For example, if a review catches an accounting error, corrective steps can include fixing the faulty process or defining a new preventive check.
Control Strength Hierarchy
Controls vary in strength and ability to stop or reduce risks.
| Types of controls | Description | Example |
|---|---|---|
| Directive | The weakest in terms of stopping a threat, as they only set behavioral expectations. | Policies and training |
| Deterrent | More effective than directives, as they discourage undesired actions. | Warning signs and security cameras |
| Detective | They cannot prevent the act, but it is highly effective in exposing the act when it happens. | Alerts, logs, and audits |
| Preventive | The strongest, as they block unwanted actions from occurring at all. | Locked doors and system access controls |
Strong or weak, each control type serves a purpose. Implementing a combination of controls, where weaker ones complement stronger ones, is essential for a strong control environment.
Control Objectives and Measures
Controls are designed with specific goals or objectives that are tied to what the organization wants to achieve. Organizations also link certain measures with control objectives. These measures ensure that the controls are working as intended and yield the desired results.
Linking Controls to Business Objectives
Controls are not randomly implemented. Good controls directly support business objectives as they:
- Make business operations and processes more effective and efficient. For example, detective controls have the objective to detect errors or fraud, while corrective controls aim to fix problems once they are identified.
- Help companies comply with laws, regulations, and internal policies.
- Protect assets from loss, misuse, or damage.
- Make financial and operational reporting more reliable and accurate.
When control objectives align with the organization’s bigger goals, they become indispensable to business and its success.
Documentation of Objectives for Control Monitoring
A control remains relevant as long as it is monitored and reviewed. Start by writing down the objectives for each control, which should clearly state what that control stands to achieve. This makes it easier to test and evaluate the control later.
Organizations should follow these key practices:
- Keep the objectives for each control documented.
- Conduct regular reviews and testing to check if the control is working properly.
- Set up variance thresholds to flag when results do not match expectations.
- Define follow-up procedures to address any issues that are identified.
Consistent monitoring of controls is essential to validate results against objectives and ensure that controls remain relevant and effective over time.
Risk Treatment Process
Controls are intended to manage risk. Therefore, the risk treatment process is about assessing threats and vulnerabilities and then selecting the right internal control types based on findings. This involves:
- Selecting appropriate control types (preventive, detective, corrective, etc.) that address the specific risks.
- Implementing them in a way that supports the control objectives.
- Carrying out activities that prevent, reduce, or eliminate the chance of a threat occurring.
The risk treatment process has the power to turn control objectives into real-world protection that enables organizations to stay confident even in the face of uncertainty.
Types of Controls in Audit
In an audit context, controls are evaluated based on how they prevent, detect, and correct risks that may impact financial reporting and operations. The main types of controls in audit are:
- Preventive controls
- Detective controls
- Corrective controls
- Compensating controls
Auditors review these types of controls to assess whether the organization’s systems are reliable, capable of protecting assets, and comply with regulations.
Implementation Guidance for Control Types
It is critical to implement controls meaningfully across the organization in order to benefit from them truly. Strong leadership support is critical in this regard. If executives are serious about controls, employees will follow their footsteps.
The following measures can help make controls effective:
- Communication: Companies should take steps to communicate controls through different channels such as team meetings, emails, internal postings, and employee handbooks. This ensures that all employees understand expectations and responsibilities.
- Training: Employees should be trained in correctly applying controls, understanding the rules, and applying them in real situations.
- Compliance Checks: Management should regularly assess whether employees are following the controls and whether actions comply with policies and procedures. This can be achieved through tools like compliance checklists, inventory reviews, access control reviews, account reconciliations, and examination of audit trails.
- Addressing Gaps: Gaps should be addressed quickly. This involves implementing a new control, recommunicating expectations, or providing additional training to ensure everyone understands and complies.
Examples of Some Control Types
| Control Type | Examples |
|---|---|
| Directive Controls | Policies and Procedures Codes of conduct and ethics policies Standard operating procedures (SOPs) Acceptable use policies for IT and data Training and Awareness Employee onboarding programs Regular compliance and ethics training Cybersecurity awareness campaigns Communication and Guidance Employee handbooks Policy manuals and job aids Leadership messaging (“tone at the top”) Notice boards, signage, and reminders Governance and Oversight Board and committee charters Clear reporting lines and accountability structures Strategic planning directives |
| Preventive Controls | People and Responsibilities Segregation of duties Employing qualified personnel Use of standard operating procedures (SOPs) to prevent errors Approvals and Authorizations Proper approvals, authorization, and verification Transaction authorization procedures Access and Security Access controls (physical and logical) Access control procedures Multi-factor authentication Physical barriers Technology and System Safeguards System edit checks Firewalls and perimeter defenses Network and email security |
| Detective Controls | Reviews and Reconciliations Bank and account reconciliations Random or independent reviews of transactions After-the-fact approvals Exception report reviews Variance analysis Accountability and Documentation Audit trails, signatures, and record-keeping Logging Reporting Internal audits and other independent reviews System and Process Monitoring Log monitoring and behavior analytics Checkpoints in production jobs Echo controls telecommunications Error messages on incorrect or missing data (for example, tape labels) Quality and Risk Oversight Quality assurance checks Risk management processes Entity-level monitoring and analytics |
| Corrective & Recovery Controls | Planning and Preparedness Business continuity planning (BCP) Disaster recovery planning (DRP) Incident response planning Business continuity and disaster recovery plans (combined) Runbooks (step-by-step response guides) Recovery and Restoration Backup procedures (data and system recovery) Server and workstation hardening (to reduce vulnerabilities after an incident) Automated Corrective Actions: A credit card company blocks a card after detecting fraud Sprinkler system activation upon smoke/fire detection |
| Compensating Controls | Oversight and Review Regular log reviews (system, access, and transaction logs) Independent reviews of key transactions by management Periodic reconciliations performed by someone not directly involved in processing Documentation and Transparency Audit trails to track activities Supporting documentation for all transactions Formal signoffs by management when SoD is not followed System-Based Controls Automated alerts for unusual activity Exception reporting with follow-up review Independent Assurance Internal audit reviews focusing on high-risk areas Peer reviews or cross-checking in small teams |
Core Internal Control Activities
Internal controls are practical steps integrated into daily operations to protect resources, ensure financial reporting accuracy, and keep processes running smoothly.
Here are the core activities that create a strong control environment.
Proper Approvals, Authorization & Verification (Preventive)
Organizations rely on strong approvals and authorizations to catch errors, fraud, and misuse before they happen. The following elements create a strong approval ecosystem:
| Elements | Descriptions |
|---|---|
| Signatory Authority | Only individuals with designated authority should approve transactions. The approving authority should be a higher-level supervisor with enough knowledge to make an informed decision. These individuals should be independent of the person initiating the request. |
| Restrictions | No one should approve their payments or expenses.Approvals should carry a specific validity period. For example, if a purchase request is not processed within 6 months of approval, it should become invalid and require re-approval for processing. |
| Dual Authorization for High-Risk Transactions | Two authorized signatures should be required for large payments and access to sensitive data. |
| Complete Documentation | Approval should only be given when supporting documents are accurate and complete.Insufficient documentation should be checked and clarified before approval. |
| Access Control | Confidential information should only be accessible on a need-to-know basis. |
| System-Enforced Approval Workflow | Use ERP or financial systems for approval workflows. This also ensures that no checks or procedures are bypassed. |
| Termination/Transfer Procedures | Access and authority must be removed or adjusted immediately when someone changes roles or leaves the organization. Examples include returning company-issued mobile phones and laptops, removing personal biometric data from building access systems, updating signature authority, and disabling access to third-party vendor portals. |
Accountability and Audit Trail (Detective)
Accountability works best when there is a clear record showing who did what, when, and why.
| Elements | Description |
|---|---|
| Identification | Use signatures, initials, timestamps, and system login IDs to track actions. |
| Audit Trail | Every step in a process should be traceable to an individual. This makes it easier to pinpoint responsibility in case of error. |
| Audit of Approval Process | Approval logs should be audited to detect unusual patterns, such as one approver always signing off on certain vendors. |
| Record Retention | Keep supporting documents and system records according to the organization’s record retention policy so that they are available for review or investigation when required. |
Separation/Segregation of Duties – SoD (Preventive)
SoD is based on one basic principle:
- No single person should have complete control over a transaction from start to finish without review or oversight from at least one person.
- The person responsible for review should be different from any other person in the action chain.
This principle is the most effective way to reduce the risk of fraud or misappropriation. It not only applies to finance, but to non-financial areas too, such as employee performance reviews.
Here are some SoD examples.
| SoD Examples | Description |
|---|---|
| Revenue | Different individuals should handle distinct functions in the process, such as receiving cash, preparing deposits, and reconciling those deposits with the accounting records. |
| Expenditure | The people who process, approve, and reconcile payments should be different individuals. |
| Payroll | Separate the duties of entering employee data, approving hours worked, and managing the payroll budget. For example, the person adding a new employee to payroll should not also approve of their hours worked. |
| Independent Review | After transactions are complete, an independent party should review and reconcile records. This person may be responsible for the department or project budget. |
Reconciliations (Detective)
Reconciliations are a great way to verify that records match reality and that nothing suspicious has slipped through. This serves several purposes, such as detecting fraud, theft, inappropriate use of funds, or human error. The reconciliation process includes these elements:
| Examples | Descriptions |
|---|---|
| Monthly Reviews | The scope of these reviews should include all transactions posted to accounts. Compare account activity to supporting records to spot errors, theft, or misuse. Set thresholds that trigger a deeper review of discrepancies. |
| Variance Analysis | Compare actual financial activity to the budget or forecast and investigate differences beyond a certain threshold. |
| Documentation | Keep copies of all documents used in the reconciliation (such as bank statements, invoices, receipts) for follow-up or audit purposes. |
| Exception Tracking | Maintain a log of all discrepancies found, the resolution steps taken, and the date of closure. |
| Management Oversight | Senior personnel should: Review reconciliations to ensure they are consistent and reasonable.Check that reconciliations are timely and complete.Follow up on questionable items or issues identified. |
| Automation | Use reconciliation software to reduce manual errors and speed up the process. |
Security and Safeguarding of Assets (Preventive and Detective)
Protecting the organization’s assets from damage or loss calls for both detective and preventive measures. Assets can be physical and virtual, for example, cash, equipment, data, IT hardware and software, databases, sensitive documents, or property.
| Elements | Examples |
|---|---|
| Physical Security | Use locked storage, restricted areas, and security presence to prevent loss or damage. Use encryption to secure digital assets. Take regular backups and test the restore process. |
| Monitoring | Conduct periodic checks to ensure assets are where they should be and in good condition. Label physical assets with ID numbers or barcodes for ease in tracking. Use CCTV to detect suspicious activity in real time. |
| Incident Reporting Protocol | Define a process for reporting lost, stolen, or damaged assets. |
Accuracy of Data Entry (Preventive & Detective)
Accurate data entry is the foundation of reliable reporting and sound decision-making. It involves the following:
| Elements | Description |
|---|---|
| Training | Provide regular training to data entry personnel on system use, data standards, and techniques to avoid errors. Only trained, authorized individuals should be allowed to enter data. |
| Version Control | Use the latest, approved version of a document or dataset for data entry. |
| Verification | Compare output reports to the source documents to confirm accuracy. |
| System Edits | Enable built-in computer system edits or other automated checks (like reasonableness or logic tests) to catch errors during data entry. |
| Batch Totals | Compare original batch totals to processed reports to catch any discrepancies. |
| Continuous Review | Implement checks to ensure that mistakes are corrected early, before they cascade to other processes or reports. |
Fraud Risks and Red Flags
Fraud can take many forms, including theft, subtle misuse of resources, and misrepresentation of facts. While no control system can potentially eliminate it, it can drastically lower risk levels. Controls raise awareness about the common frauds and where to keep watch. This, coupled with management oversight, enables organizations to detect issues early and take corrective action.
Fraud Scenarios
Fraud often hides in everyday processes and will slip through in the absence of careful review. Some common examples include:
- Fictitious invoices, such as creating or approving payments for items that were never provided.
- Misuse of credit cards, as in using a company card for personal purchases.
- Payroll manipulation, for instance, by inflating hours worked, adding “ghost” employees, or changing pay rates without authority.
- Misappropriation of cash, such as skimming from cash receipts, under-reporting collections, or diverting deposits.
- Misuse of organizational resources, as in using facilities, equipment, or funds for non-business purposes.
Organizations should stay alert to these scenarios and train their staff to recognize them. Suspicious activity is likely to get noticed in a vigilant environment.
Management Oversight
To prevent fraud, the management should not just rely on controls but engage in the following:
- Conduct regular reviews of financial activity, reconciliations, and supporting documents.
- Facilitate thorough and timely reviews so that discrepancies are caught before they blow up.
- Investigate and resolve discrepancies instead of passing them off as errors or oversights.
- Document review activities with clear evidence (initials, dates, completion checklists, etc.).
With these practices, management sends a clear message that fraud is a serious matter and will be dealt with firmly.
Cybersecurity Control Perspectives
In terms of cybersecurity, organizations continue to rely on controls to keep their systems and data safe. Four control types, namely Preventive, Detective, Corrective, and Deterrent are most relevant to cybersecurity.
Four Cybersecurity Controls
The following controls work together to protect against threats and minimize risks.
- Preventive controls aim to stop attacks or unauthorized activity before it causes harm. Firewalls, access restrictions, and MFA are some examples of these controls.
- Detective controls are meant to catch issues that slip past preventive barriers. Tools like intrusion detection systems, log monitoring, and SIEM dashboards are examples of detective controls. These systems alert teams to unusual or potentially harmful activity.
- Corrective controls come into play after an incident occurs. Their goal is to limit damage and restore systems. Corrective control examples include activating disaster recovery plans, applying patches, and restoring data from backups.
- Deterrent controls are about making attackers think twice. They make them feel that the reward is not worth the risk of getting caught. Surveillance cameras and clear enforcement policies are some examples of these controls.
Technical (Logical) Controls
Technical controls are built directly into an organization’s IT systems and remain one of the strongest defenses against cybersecurity threats. Technical controls include:
- Firewalls and proxies for filtering traffic and block unauthorized access.
- Intrusion detection and prevention systems (IDS/IPS) to identify and stop suspicious activity.
- Operating system restrictions and login mechanisms to enforce user access rules.
- Antivirus and anti-malware tools to protect against malicious software.
- Security Information and Event Management (SIEM) systems to centralize monitoring, detect patterns, and alert teams to potential incidents.
Assessment, Optimization and Tool Support
To manage risk, organizations should begin by assessing their risk posture. They should look for answers to questions such as where they stand, what is already failing, what might fail soon, and where the gaps exist.
Controls are the building blocks of a risk management plan. They help teams identify weak spots, set priorities, and even anticipate issues in advance. But controls do not just work on their own. With regular risk assessments, organizations experience a subtle shift from a reactive to a proactive risk approach, where reacting to problems after they occur matures into preventing them in the first place.
Using Pathlock’s Continuous Controls Monitoring System
Manually monitoring controls and assessing risks is time-intensive and leaves you vulnerable. Pathlock’s Continuous Controls Monitoring (CCM) system is a great choice for automating control monitoring and compliance tasks. With continuous, real-time visibility, you are better positioned to quantify risk, prioritize responses, and automate remediation. The result is a more proactive and efficient approach to managing threats and meeting compliance requirements.
Pathlock’s Continuous Controls Monitoring (CCM) is designed to enhance the effectiveness, responsiveness, and measurability of internal controls:
- Automation of control monitoring: CCM continuously tracks business processes and financial controls, replacing manual checks and sample-based testing with always‑on, real‑time oversight.
- Risk quantification tied to transactions: Potential SoD violations are not just detected, they are assessed in financial terms, enabling compliance teams to prioritize remediation based on monetary impact.
- Configuration and master data change tracking: CCM provides detailed tracking of changes to system configurations and master data—capturing who made a change, when, and what the before/after values are.
- Centralized controls management: It consolidates control definitions across multiple frameworks into a unified platform, aligning governance with regulatory standards and reducing manual effort.
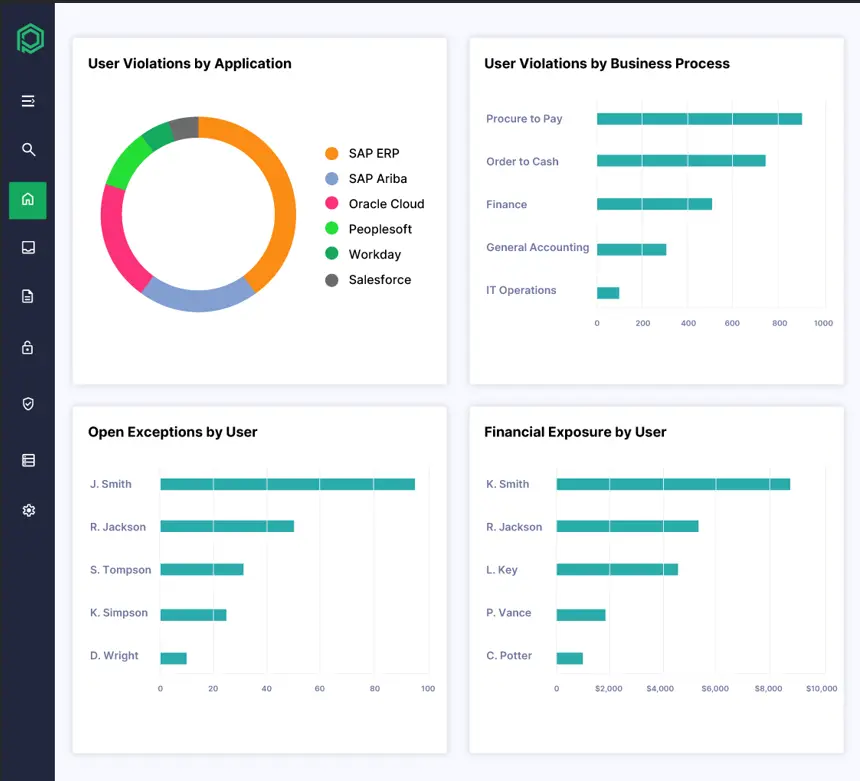
In this video, you will learn how Pathlock’s Continuous Controls Monitoring delivers real-time risk management by bridging the gap between traditional access governance and ongoing risk oversight. You’ll see how to investigate monitored rule exceptions, drill into transaction and user details, quantify financial risk exposure, and monitor high-risk events and suspicious activities — all through intuitive dashboards and automated workflows.
Beyond IGA: Real-Time Risk Management with Continuous Controls Monitoring from Pathlock
CISA Perspective: Certification and Self-Evaluation
Candidates preparing for the CISA (Certified Information Systems Auditor) certification will come across certain control concepts again and again. They should learn to define these controls with examples of their practical application.
Commonly tested areas include:
- Control types: Understanding the difference between preventive, detective, corrective, and compensating controls.
- Control objectives: Knowing why specific controls are put in place and what risks they are meant to address.
- Compensating controls: Being able to explain how these serve as substitutes when a standard control is missing or weak.
Sample Q&A Themes
CISA applicants should expect practical, scenario-based questions that test their understanding of control types and their application.
Common areas include:
- Control objectives: Being able to explain why organizations set specific objectives (for example, accuracy of financial reporting) and how auditors use them to design audit programs.
- Difference between control types: Being able to distinguish preventive, detective, corrective, and compensating controls. For instance, a firewall is preventive, an intrusion detection system is detective, restoring a backup is corrective, and extra oversight when segregation of duties is not possible is compensating.
- Segregation of duties classification: Knowing that this is a preventive control, designed to stop fraud or error before it happens by ensuring no single individual has complete control over a process.
- Controls minimizing impact: Understanding that controls do not eliminate risk but limit the damage if it happens. For example, regular data backups do not prevent a system crash, but they mitigate its impact by allowing recovery.
- Reasons for control objectives in audit programs: Knowing why auditors rely on control objectives as a guide. Control objectives clarify what the control is meant to achieve, such as asset protection or accurate reporting. With this in view, auditors can design effective tests and evaluate whether controls are effectively managing risks.
Summing Up
Organizations should implement a balanced strategy that combines technology with clear procedures and robust management oversight to create an effective risk management environment. While primary controls should take priority, they should be strengthened by supplementary controls to address risk from all angles. And this isn’t a “set it and forget it” system. Organizations should be committed to continuous improvement, using feedback from risk assessments and performance analysis to strengthen controls. Everyone in an organization should play their part.




