
Weakest Link in SOX Compliance
With 44% of audit and finance leaders citing IT access controls as their biggest challenge, relying on manual oversight is too risky. Even one gap can cascade into audit failures, restatements, and reputational damage. It doesn’t have to be this way.
Strengthen Your SOX IT General Controls
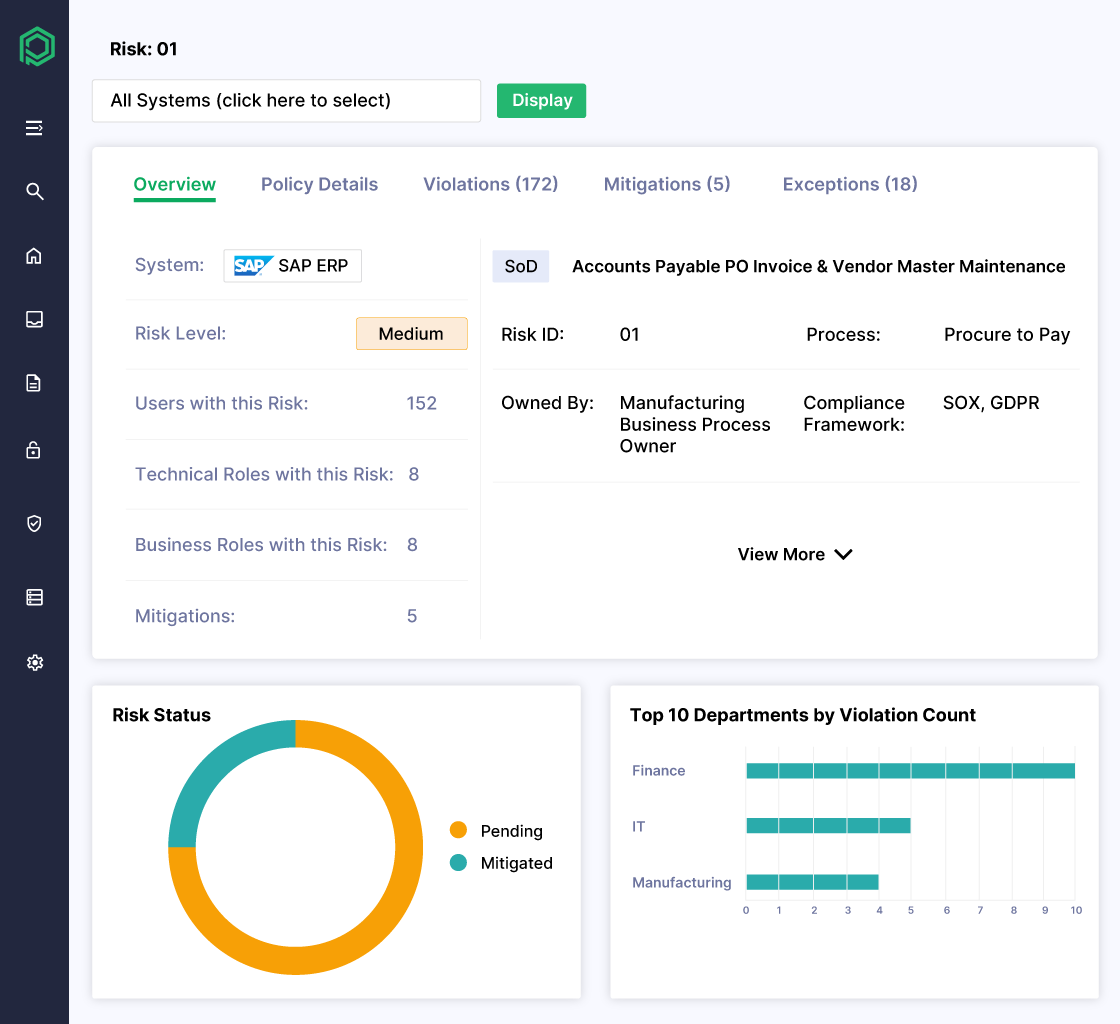
Control SoD and Sensitive Access Risks
- Continuously identify and remediate SoD conflicts across all applications
- Flag and monitor sensitive access to protect high-risk transactions and data
- Document ruleset changes and approvals to deliver complete SOX-ready evidence
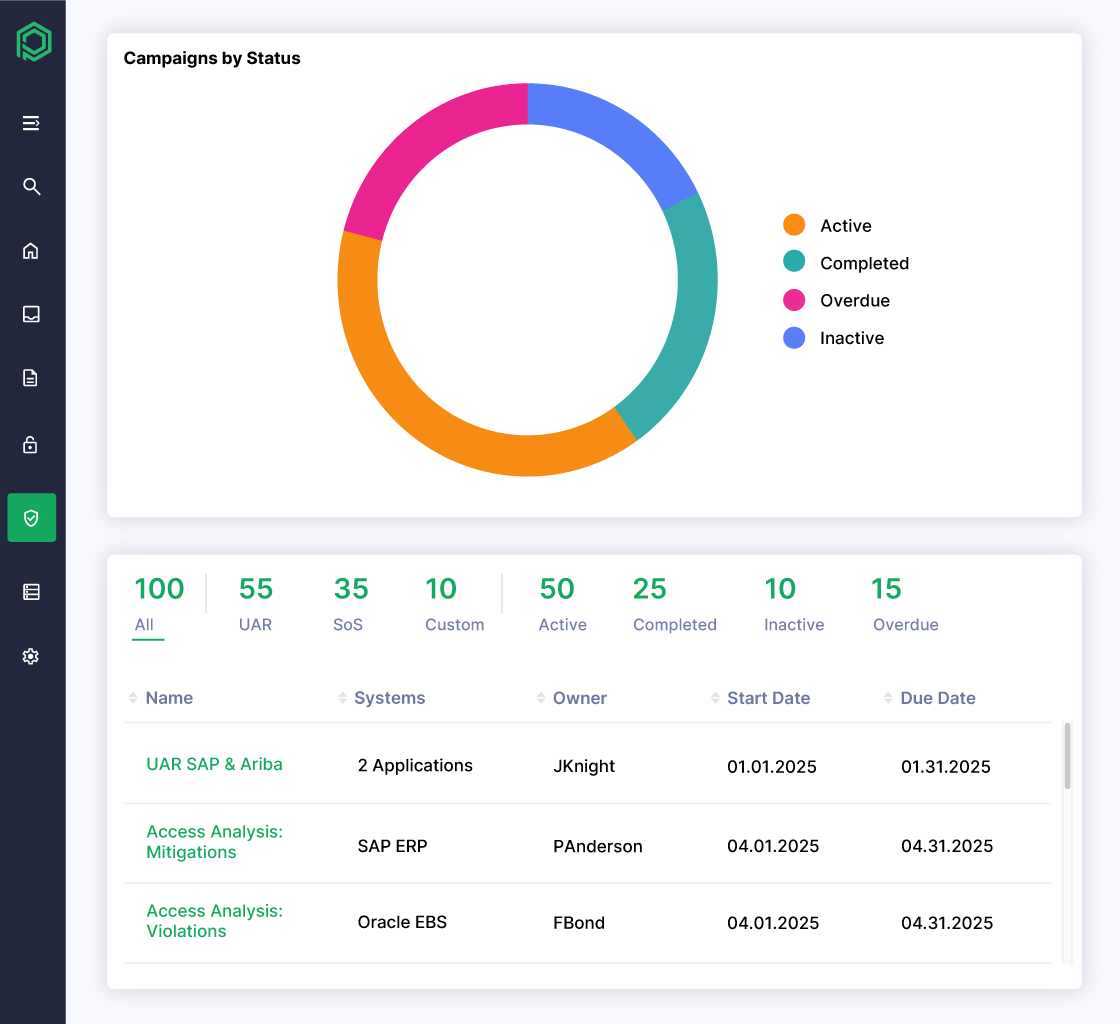
Streamline User Access Reviews and Certifications
- Automate periodic user access reviews across all applications
- Ensure timely revocation of unnecessary or high-risk access
- Provide auditors with complete evidence of approvals and removals
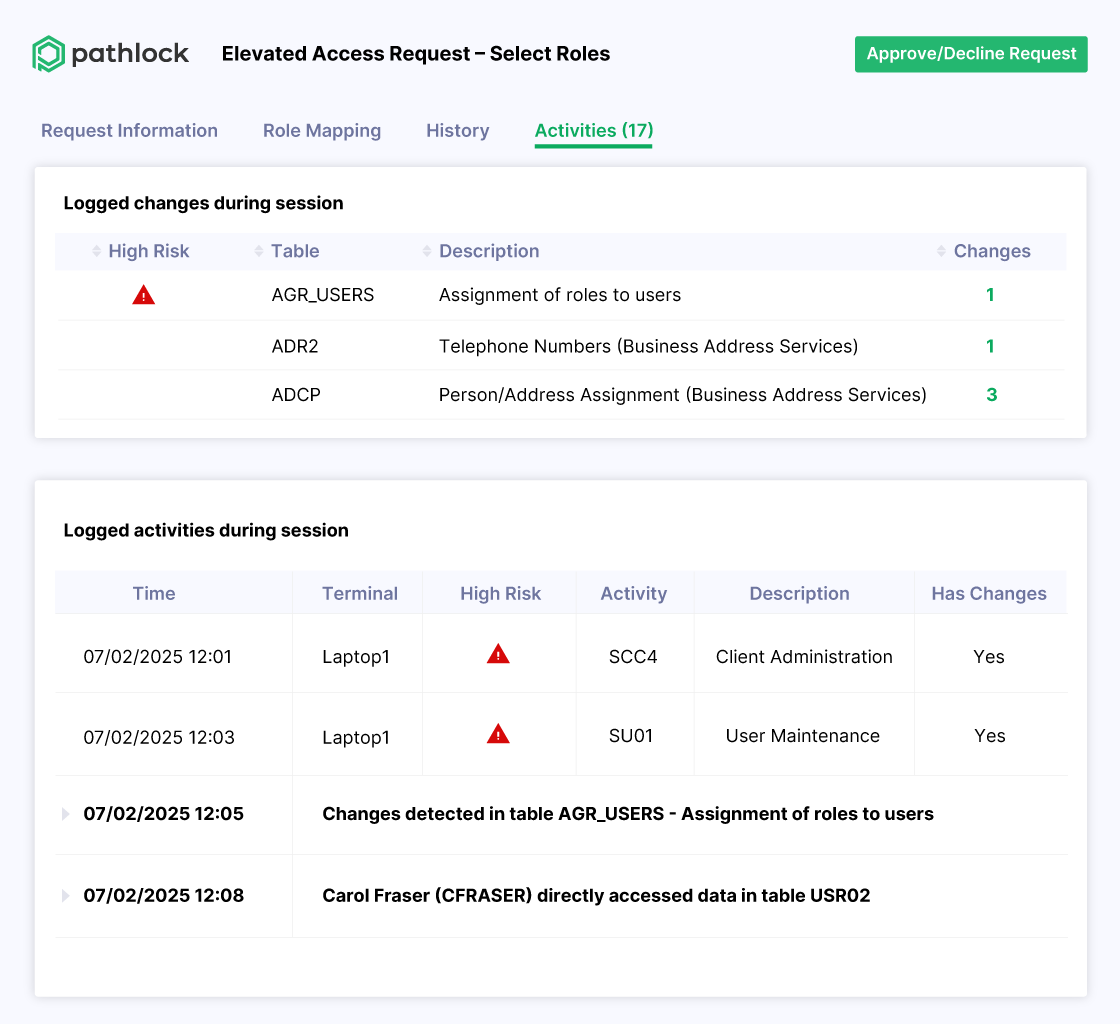
Control Elevated Access with Confidence
- Grant privileged or firefighter access only through approved workflows
- Monitor and log all elevated activity with complete audit trails
- Revoke temporary access automatically to reduce risk exposure

Get Expert Guidance on SOX Compliance
Don’t Take Our Word for It
“Pathlock streamlined our SOX audits by helping us identify true SoD violations, so we can focus on mitigating actual risks, not just potential ones.”

Streamline Audit Preparations
and Continuous Compliance
- Fine-grained SoD conflict detection and remediation across all in-scope applications
- Automated compliant provisioning and periodic user access certifications with full audit trails
- Centralized control over privileged and emergency access, with complete monitoring and logs
- Automated testing of controls with continuous monitoring of system access and financial transactions
- Real-time detection of violations, unauthorized changes, and policy breaches
- Compliance-ready reports that reduce manual documentation and speed up audits
- Ongoing monitoring of vulnerabilities and misconfigurations across SAP
- Automated detection of abnormal activity with rapid, risk-based response to prevent audit findings
- Centralized dashboards and audit-ready reporting
- Real-time data masking, export blocking, and scrambling to protect sensitive information
- Attribute-based rules that scale without adding role complexity or manual effort
- Centralized logs and dashboards that provide clear evidence for SOX compliance
See Pathlock in Action
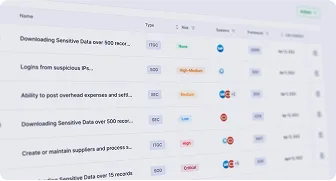
Analyze Access Risks and SoD Violations
Discover how Pathlock identifies real access risks across applications and helps you prioritize remediation with fine-grained SoD analysis.
Automate Compliant User Provisioning
See how Pathlock streamlines onboarding and access approvals with built-in policy checks, usage insights, and audit-ready workflows.

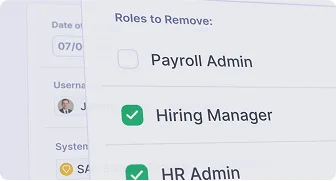
Accelerate Risk-Aware Access Certifications
Explore how Pathlock automates user access reviews, flags risky entitlements, and provides actionable data to enforce least privilege.
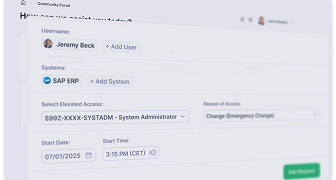
Control Privileged Access with Confidence
Learn how Pathlock manages time-bound elevated access, logs privileged activity, and prevents standing privileges across your systems.
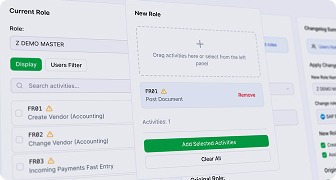
Proactively Manage Roles and Reduce Risk
Discover how Pathlock AI-powered role management tools help you simplify role design and reduce your organization’s risk exposure.
Identify and Resolve Control Exceptions
Discover how Pathlock centralizes business and manual process controls into one automated system to improve efficiency and risk visibility.

Dynamically Control and Secure Access to SAP Data
Mask, scramble, and prevent unauthorized access to data to minimize role explosion and reduce the risk of breaches across your SAP systems.