PATHLOCK DIFFERENCE
Automate
Simplify Provisioning, Strengthen Compliance
Manual processes slow down onboarding, introduce errors, and leave compliance teams chasing paper trails. With the right solution, organizations can deliver timely access without sacrificing control. Pathlock brings speed and accuracy to provisioning decisions.
Automate
Audit Preparation
Document and store provisioning activity in a centralized location
Trusted by 1,300+ Customers
Don’t Take Our Word for It
Discover how organizations worldwide use Pathlock to automate compliant provisioning, maintain regulatory compliance, and achieve more.
“Pathlock ensured secure and compliant provisioning and identity lifecycle management for students and staff.”

— Charles Lukes
PeopleSoft Security Admin, Lee County School District
How It Works
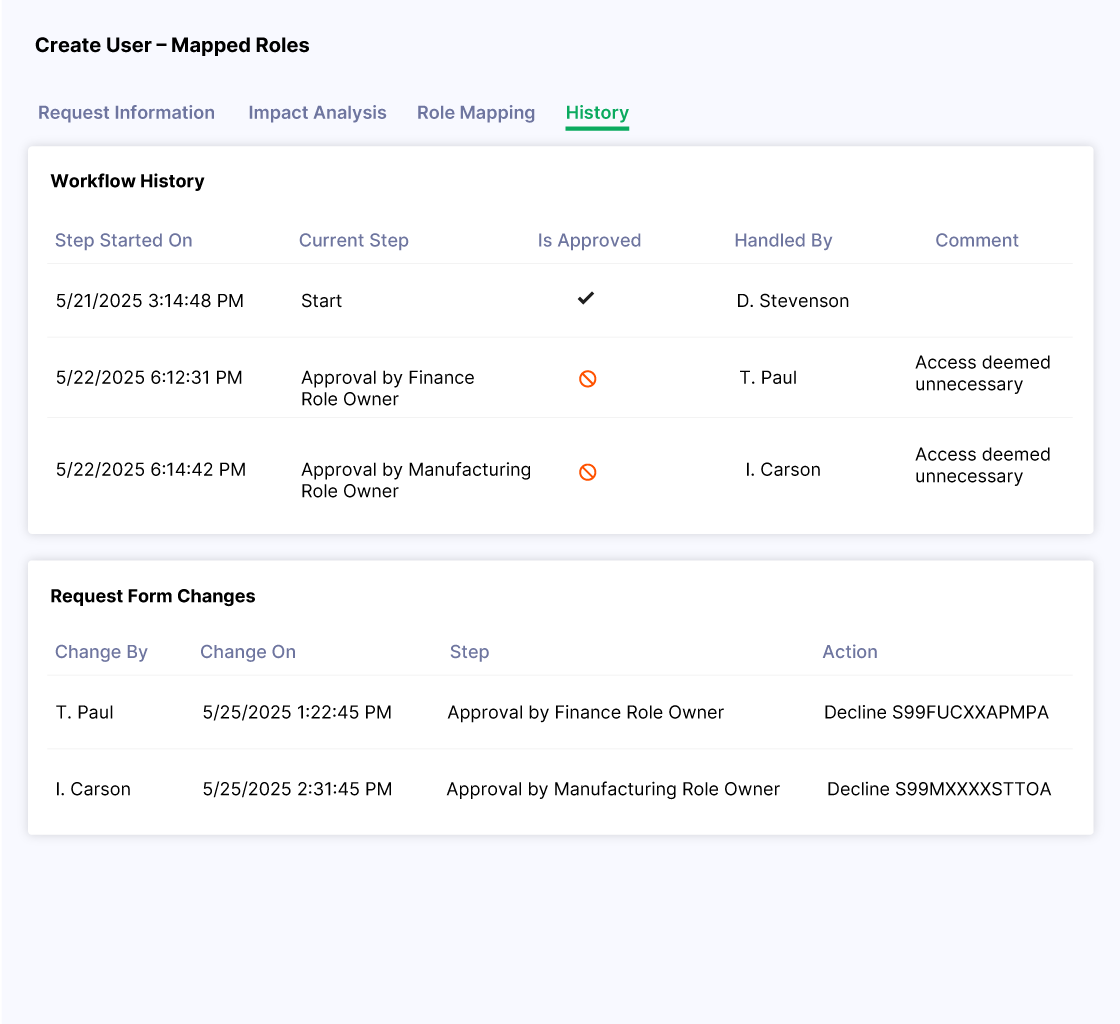
See Risk-Aware and Compliant User Provisioning In Action
Pathlock automates compliant provisioning to ensure users receive the right access at the right time—without compromising compliance. By combining intelligent automation with risk-aware decisioning, Pathlock accelerates onboarding, reduces errors, and maintains a complete audit trail.

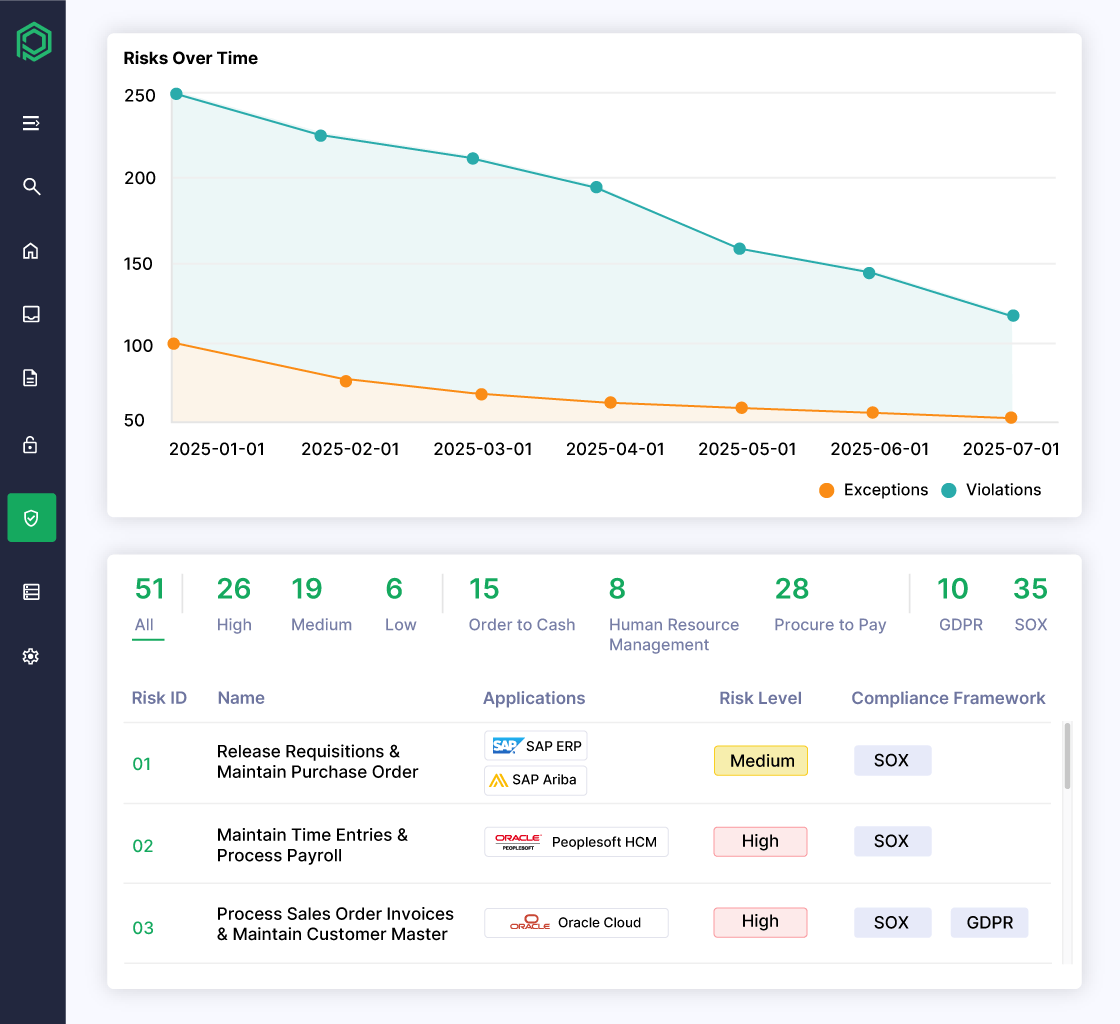
Fine-Grained SoD and Sensitive Access Insights
Provisioning isn’t just about granting access—it’s about granting the right access. Pathlock embeds real-time SoD and sensitive access checks directly into the provisioning workflow, helping approvers identify risks before access is assigned.
- Identify risks at the point of request using out-of-the-box controls
- Detect segregation of duties conflicts across multiple applications
- Simulate changes to determine if requested access introduces material risk

Compliant Provisioning Across All Business Applications
Simplify and standardize how access is granted across your organization. Pathlock centralizes provisioning for all business-critical applications, so you can enforce policies consistently and reduce manual effort.
- Provision access across ERP systems and enterprise apps like SAP, Oracle, Workday, and Salesforce
- Apply consistent rules and workflows across all user types—including employees, contractors, and third parties
- Maintain a complete audit trail for every provisioning action to support regulatory compliance

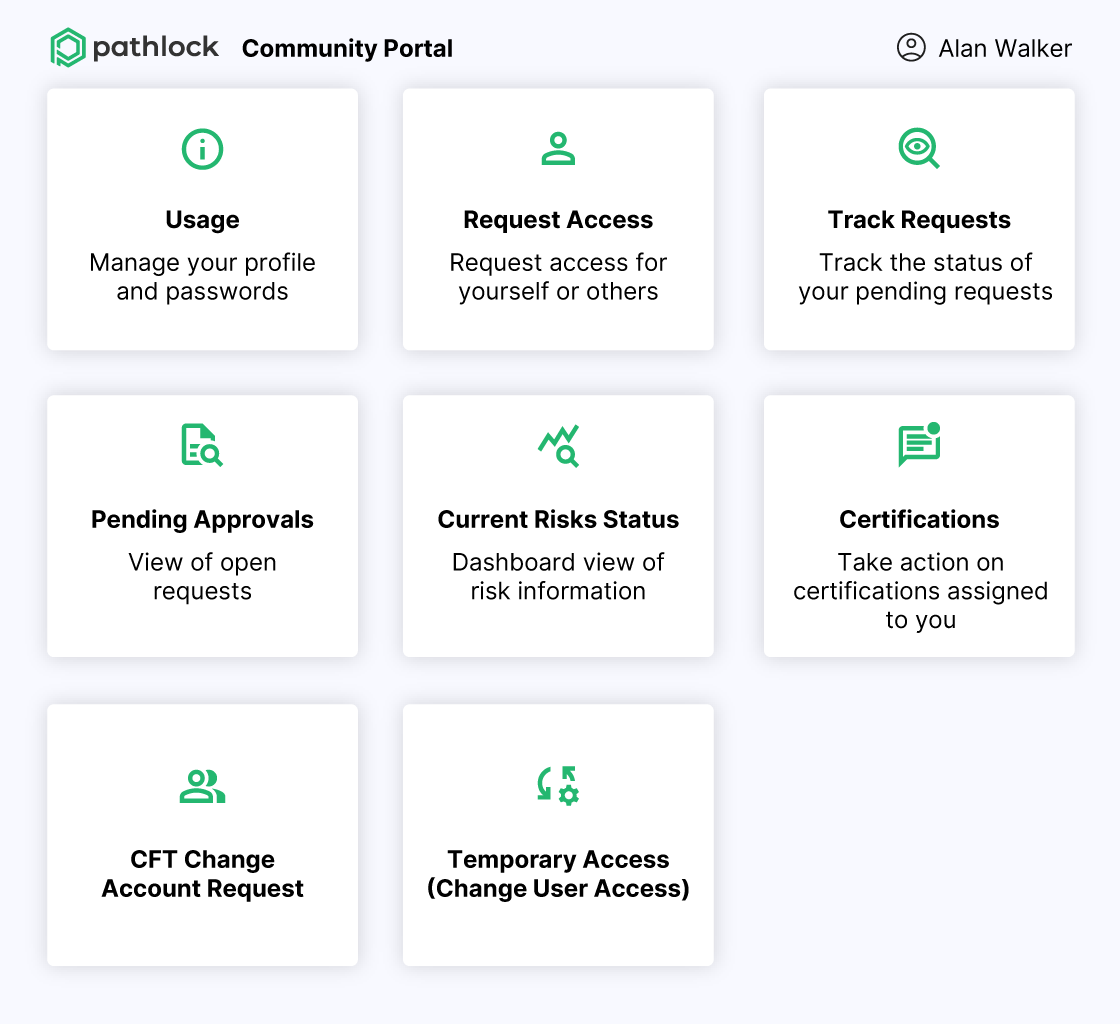
Intuitive, Modern User Interface
Pathlock’s intuitive interface isn’t just sleek—it’s purpose-built to simplify provisioning for every stakeholder, from requesters to reviewers. The result: faster, more accurate access decisions without the back-and-forth.
- Guide requesters through a streamlined experience to select roles and justify access
- Empower approvers with clear risk context, policy checks, and one-click decision-making
- Give compliance teams full visibility into provisioning workflows with centralized audit trails

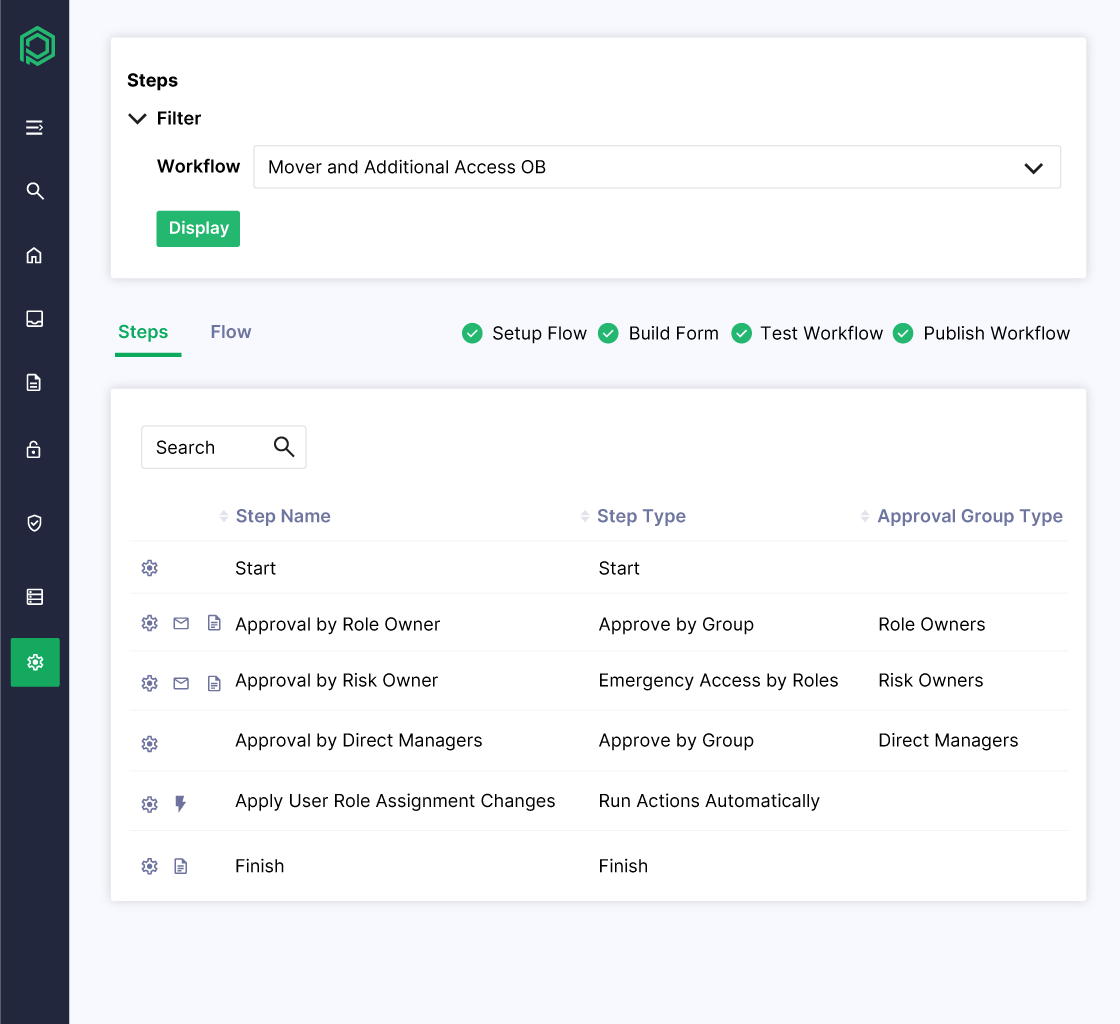
Configurable Workflows Built for Your Business
Pathlock’s provisioning workflows are fully configurable to fit your unique processes, policies, and organizational structure. Whether you’re managing employees, contractors, or third parties, Pathlock always adapts to your needs.
- Design custom approval paths based on user type, application, or risk level
- Automate escalations, reassignments, and notifications to keep requests moving
- Standardize policy enforcement while maintaining flexibility for business-specific requirements

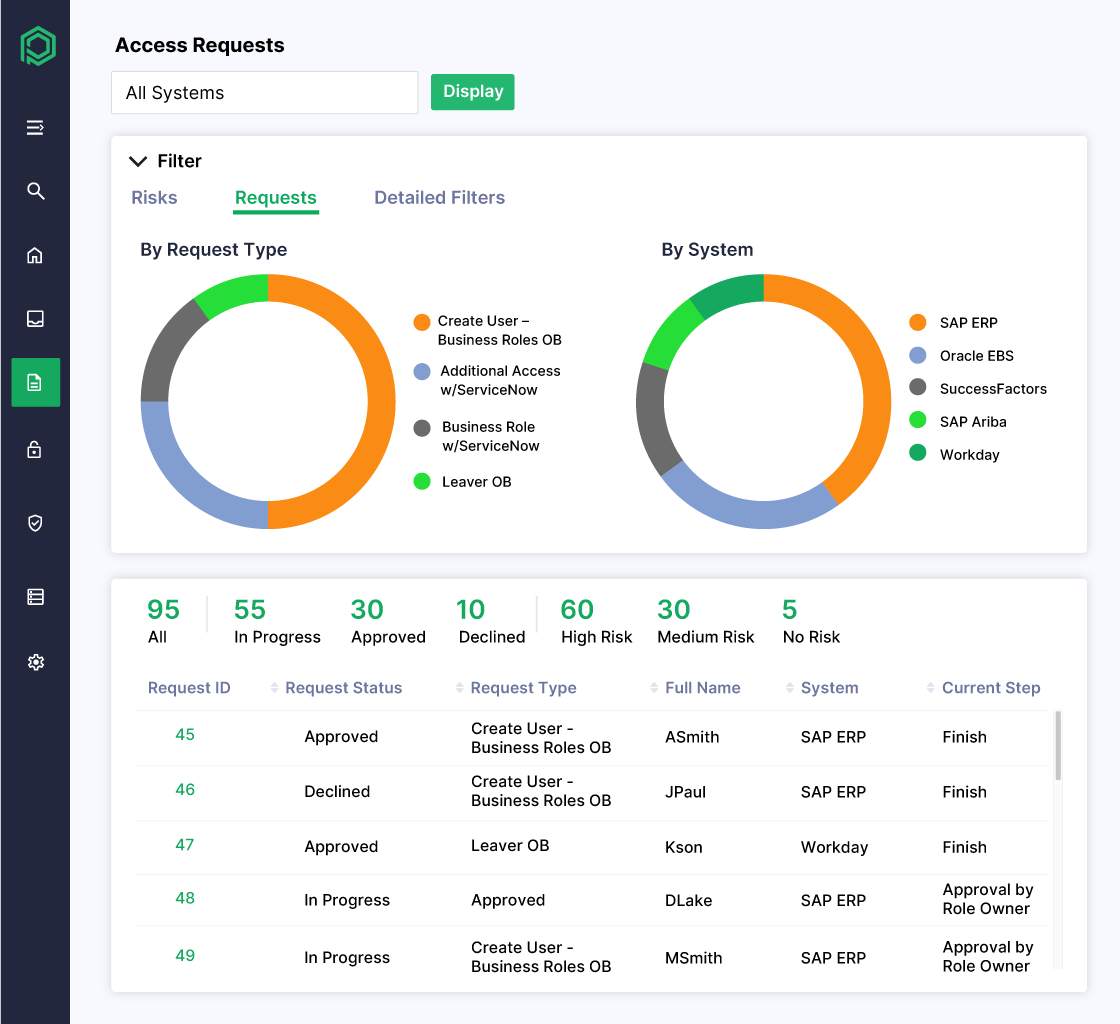
Audit-Ready Reports and Dashboards
With Pathlock, every provisioning action is tracked, timestamped, and reportable—so you’re always prepared for audits. Dashboards and reports give stakeholders the insights they need to monitor access, enforce policies, and demonstrate compliance.
- View end-to-end provisioning activity across systems with centralized, real-time dashboards
- Export detailed audit logs and reports to satisfy internal reviews and regulatory requirements
- Empower compliance teams with visibility into approvals, exceptions, and policy enforcement
Solution Overview
Learn how organizations use Pathlock to efficiently create, manage, and remove access across business applications.
Ready to Get Started?
Pathlock helps enterprises streamline and secure user provisioning with policy-driven automation. Grant, modify, and revoke access confidently—while maintaining compliance, audit readiness, and complete visibility across every step of the user lifecycle.
