Following up on last year’s Executive Order to help improve the nation’s cybersecurity posture, the White House released a 30-page zero-trust strategy document outlining several measures federal agencies must enact to secure systems and limit the risk of security incidents.
The White House noted that the growing threat of sophisticated cyberattacks (for example, SolarWinds, ransomware, and Log4j vulnerability) underscores that the Federal Government “can no longer depend on conventional perimeter-based defenses to protect critical systems and data.”
And neither should you.
Instead, the Federal Government will focus on multifactor authentication as a critical part of its security baseline. In fact, strong authentication, as provided by a strong and dynamic MFA, is a necessary component of any zero-trust strategy.
What’s Good For The Feds Is Good For The States
If you’re a state or local government, I recommend that you review the White House’s zero trust strategy document. You won’t be bound by their mandated timelines, but the document is full of best practices and sound advice. Briefly, the security goals are based on the maturity model developed by the Cybersecurity and Infrastructure Security Agency. CISA’s zero trust model describes five complementary areas of effort (Image Source: White House):
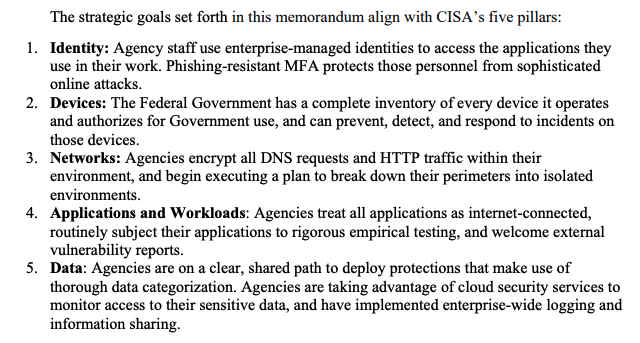
Again, all good advice. I want to point out two key actions mandated by CISA related to multifactor authentication:
- Federal Agencies “must employ centralized identity management systems for agency users that can be integrated into applications and common platforms.”
- MFA must be enforced at the application layer instead of the network layer.
Unfortunately, the majority of our clients in the government sector use ERP applications like PeopleSoft, SAP ECC, and Oracle EBS, whose native architecture does not allow for the seamless integration of MFA solutions that can be A) integrated at the field/transaction levels of workflows or B) deployed dynamically with each unique context of access.
These traditional ERP applications use static security controls to govern access. These controls fail to provide protection beyond the traditional perimeter-based security because they do not leverage contextual attributes. Put another way, these ERP systems do not allow seamless integration of MFA solutions and make it challenging to achieve strong authentication for zero trust.
Centrally Managed MFA To Enable Zero Trust Security With Pathlock
Fortunately, requiring dynamic MFA that is integrated inside ERP applications is one of the most common use cases our Pathlock Platform solves.
The platform can enforce zero trust security policies that can dynamically secure data and regulate access based on contextual attributes (e.g., IP address, time of day, location, user security clearance, data classification, device used, max dollar amounts, etc.). Additionally, Pathlock can help bring your zero-trust strategy to life with:
- Context-Aware Access Controls (with ABAC) – Fine-grained controls help you set dynamic access permissions for users down to the transaction and field level
- Step-Up Authentication – Integrate enterprise MFA at the field level for re-authentication when a user requests access to sensitive data
- Transaction Monitoring & Control – Monitor high-risk transactions and automatically remove privileged access rights to stop potentially high-risk user activity
- Data Masking – Enforce full, partial, or click-to-view data masking to obscure sensitive data and protect against unnecessary data exposure
- Logging & Analytics – Capture detailed logs to get real-time visibility and insights into user access, IP address of frequent transactions, asset inventory, and other vital data.
Contact Pathlock today for a demo to learn how we develop native integrations between Oracle and SAP ERP applications and some of the top MFA providers in the market.


