What is Azure Active Directory?
Azure Active Directory (Azure AD) is a cloud-based identity and access management (IAM) solution. It provides directory services for on-premises applications, just like the traditional Microsoft Active Directory. In addition, it lets you manage external applications, such as software as a service (SaaS) or resources in the Azure cloud.
If your organization uses Microsoft Online services such as Microsoft 365, you may not realize you are already using Azure AD to enable employees to sign into the applications. Microsoft provides the free version of Azure AD together with any Microsoft Online subscription. However, you can upgrade to a paid license to gain access to additional features such as self-service identity management, monitoring, security reporting, and secure mobile access.
Many organizations use Azure AD as their primary identity management solution, irrespective of their use of Microsoft Online services. Azure AD provides security features that are uniquely suited to the zero trust security paradigm.
Azure Active Directory Features and Services
Azure Active Directory Single Sign-On
Single sign-on (SSO) is an authentication method that lets users sign in once and get access to several software systems. It enables users to use one set of credentials to log in to multiple applications. SSO can significantly improve user experience. Azure AD enables you to enable SSO for various applications.
Here are notable benefits of Azure AD SSO:
- Improve productivity – SSO eliminates the need to memorize several sets of credentials for different applications. It enables users to easily access all their applications using SSO from any device and location.
- Accelerate user provisioning – Azure AD lets you set up automatic user provisioning and de-provisioning processes. You can use this capability to provision just-in-time access to new resources for new employees and role changes. It also helps keep all identities up to date.
- Enhance application security – SSO minimizes the risk of reusing weak and default passwords. It lets you use Azure AD Conditional Access to create risk-based security policies for individual applications. You can also measure risks associated with users, locations, and devices before allowing, verifying, limiting, or blocking access.
Azure Active Directory Security and Governance
Azure AD helps secure remote access to your organization’s systems. It provides strong authentication governed by granular access policies. It also continuously monitors threats and performs ongoing risk assessments of user connections based on machine learning and heuristics. If a connection is suspicious or unusual, Azure AD will not grant access, providing strong protection against compromised identities.
Azure AD security capabilities include:
- Verification of user identity using SSO and multi-factor authentication.
- Ability to deny access by default in line with a zero trust approach.
- Conditional access policies based on multiple criteria, including device, location, time of day, application, and individual users or user groups.
Azure Active Directory External Identities
Azure AD provides a secure and convenient way for external users like partners or customers to access your organization’s systems, with powerful options for customizing and controlling their access. It also allows the management of multiple user directories, spanning one or more organizations, in one user interface.
Azure AD’s external identity capabilities include:
- Unifying and centrally managing disparate identity systems using a cloud-based platform.
- Highly scalable system that can support any number of users from a large number of organizations.
- Uniform identity experience for any user on any device – customers and partners can use existing credentials or social media accounts to sign into your organization’s systems.
Azure Active Directory Domain Services
Azure Active Directory Domain Services (Azure AD DS) is a managed solution for directory domains that lets you run legacy applications in the Azure cloud. If your organization has older applications that don’t support modern authentication, and you don’t want to rely on legacy on-premises active directory services, you can use Azure AD DS.
Azure AD DS capabilities include:
- Directory domain operations, including domain join and group policy.
- Support for legacy protocols like Kerberos/NTLM and LDAP without having to deploy any domain controllers.
- Integration with an existing Azure AD deployment, which means users of legacy applications can use existing credentials to access both legacy and new cloud applications.
- Ability to use existing user accounts and groups to control access to cloud resources.
Azure Active Directory Reports and Monitoring
Azure AD provides on-demand reports that let you:
- See how applications and services are accessed by users
- Detect health issues in the environment (for example, high latency or failed sessions)
- Troubleshoot issues hurting user productivity
Azure AD also provides monitoring functionality that lets you:
- Integrate with security information and event management (SIEM) tools.
- Route logs to an Azure storage account and retains them for long-term use.
- Route logs to an Azure event hub and integrates the events with Splunk and Sumo Logic.
- Route logs to an Azure Log Analytics workspace, where you can analyze and alert on the data.
Azure AD Privileged Identity Management
Azure Privileged Identity Management (PIM) is a feature of Azure AD. It lets you manage and tightly control privileged access to various sensitive resources. It enables time-based activation of roles to allow individuals only the minimal access they need to your critical systems. This prevents excessive or unnecessary privileges and supports a zero trust strategy.
Related content: Read our guide to Azure AD PIM (coming soon)
Azure AD Application Proxy
Application Proxy is a feature within Azure AD that enables remote access to web applications running in an on-premise data center. Here are core capabilities of Azure AD Application Proxy:
- An Application Proxy service running in the cloud.
- An Application Proxy connector running on the on-premises server
- Azure AD.
All three of these components communicate to enable users to securely pass their sign-on tokens from Azure AD to on-premise web applications.
Related content: Read our guide to Azure AD Application Proxy (coming soon)
Azure AD Premium Licenses
Azure AD is offered free of charge with Microsoft SaaS products like Office 365. However, the free version provides only basic features. If you need additional features such as identity management, multi-factor authentication, and privileged access management (PAM), you can opt for a Premium license.
There are two Azure AD Premium licenses:
- Azure AD Premium P1 costs $6 / user / month and offers additional features such as hybrid identity management, self-service group management, and Microsoft Identity Manager.
- Azure AD Premium P2 costs $9 / user / month and offers the Premium P1 features, and in addition, Azure AD Identity Protection, PAM, advanced monitoring, entitlement management, and more.
Related content: Read our guide to Azure AD Premium (coming soon)
Azure AD Architecture
Azure AD employs a geographically-distributed architecture that offers extensive monitoring, automatic redirection, and failover and recovery capabilities.
Service Architecture Design
Azure AD’s data tier includes various front-end services that provide read/write capabilities. Within the tier, partitions form the units of scale. The following diagram shows how the architecture ensures consistency in a geographically distributed data center. It does so by ensuring all writes to a user directory go to a primary partition, which is replicated to the others.
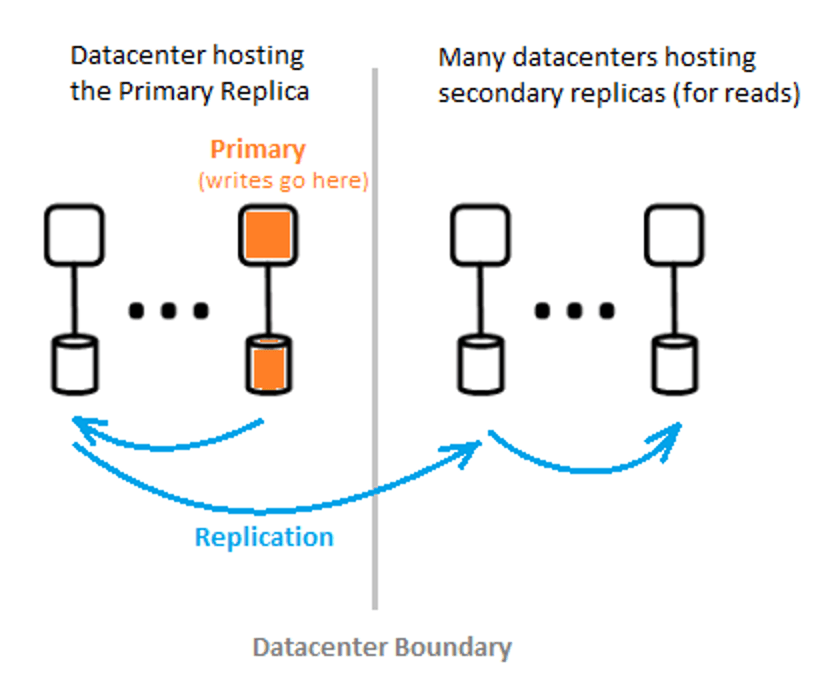
Scalability
In Azure AD, read scalability is achieved by copying data from one partition to multiple globally distributed secondary copies.
Requests made by applications to the user directory are routed to the physically nearest data center to improve performance and allow for horizontal scaling. Writes are transparently redirected to the master copy, ensuring read and write consistency.
The primary mechanism for scalability is secondary, read-only copies. Read scalability is very significant because the vast majority of requests to user directories are read requests.
Continuous Availability
Availability, or uptime, determines your system’s ability to operate without interruption. Azure AD achieves high availability by quickly transferring traffic between multiple data centers that are geographically distributed.
Each data center is independent, meaning that if any data center experiences failure, traffic can be transparently routed to another data center. This type of design enables Azure AD to maintain continuous availability during maintenance activities, eliminating downtime completely.
The Azure AD partition design uses a single master with a simplified, carefully coordinated master replica failover process. If the node running the master partition fails, Azure AD performs seamless failover to a replica on another node.
Data Centers
Azure AD stores replicas of user directories in Azure data centers around the world. The distribution of user requests among data centers works as follows:
- The Authentication service, Graph service, and other AD services operate behind a gateway service. The gateway manages load balancing for these services. It uses health probes to determine if a service is down and failover automatically, dynamically routing traffic to a healthy data center.
- For read requests, the directory employs secondary copies configured in an active-active state and running in several data centers. If an entire data center fails, traffic is automatically routed to another data center.
Differences Between Windows AD and Azure AD
Azure AD and Windows AD are both IAM systems developed by Microsoft, but they are fundamentally different. Let’s review a few of the key differences.
| Azure Active Directory | Windows Active Directory |
| Integrates with other cloud services via REST APIs | Passes data between clients and servers using the LDAP protocol |
| Uses modern authentication protocols like OAuth 2.0 and SAML | Uses Kerberos and NT LAN Manager (NTML) to validate credentials |
| Organized using tenants, each tenant includes multiple users and groups | User directory is structured according to Organizational Units, Domains, Forests |
| Access to cloud applications and resources is managed by user groups | Access to network resources is managed by user groups |
| Supports mobile device management (MDM) via Microsoft Intune | Does not support mobile devices |
| Supports Windows desktop machines via Microsoft Intune | Governs desktops using Group Policies (GPOs) |
| Can manage Azure VMs using Azure AD Domain Services | Manages on-premise servers using GPOs or server management software |
Most organizations use both Azure AD and Windows AD, the former to manage cloud access and the latter to manage access to on-premise systems. In many cases, as organizations migrate to the cloud, they add Azure AD to their existing Windows AD implementation.
To see Azure AD compared to another popular solution, read our guide to Azure AD vs Okta (coming soon)
Azure Active Directory Best Practices
Here are a few best practices you can use to make more effective use of Azure AD.
Implement Azure AD Privileged Identity Management
Here are the core features of Azure AD Privileged Identity Management (PIM):
- Identify and manage users assigned to admin roles.
- Identify unneeded or over-privileged roles that should be deleted.
- Set up rules to protect privileged roles with multi-factor authentication, and ensure privileged roles are granted for exactly enough time to perform privileged tasks.
After enabling Azure AD PIM, check the users assigned to the admin role and delete any accounts that are not required for these roles. For the remaining privileged users, transition them from permanent users to eligible users. Finally, set the appropriate policies to ensure each user gains access to privileged roles only when needed, with appropriate change management.
Best Practices for User Accounts
In an organization with thousands of user accounts, a user directory can be difficult to manage. You can take the following steps to ensure that the directory is healthy, which means it will be easier to manage and reduce the chance of a security breach:
- Periodically remove unwanted user accounts from the domain administrators group. Members of this group are granted access to many devices and servers, making them a prime target for attackers. So it is important to keep this group to an absolute minimum.
- When an employee leaves the company, the user account must be revoked. Unused accounts give former employees unauthorized access to corporate information. It can also be an easy target for hackers to break into a domain using inactive accounts. Perform due diligence and clean up abandoned accounts on a regular basis.
- Perform ongoing monitoring to identify issues like service outages and account lockouts. Spikes in login attempts should raise a red flag and usually indicate an attacker is attempting to compromise accounts.
Active Directory Security Groups
Carefully define your security groups using these principles:
Least privilege
Identify which employees should access which resources and whether they should be authorized on a regular basis. Follow the principle of least privilege, recognizing that most employees do not need full domain access. Grant each user account the minimum privileges required to complete their assigned tasks. This can significantly reduce security risks—whether a user’s device is infected by malware or their credentials are compromised, attackers can do much less damage with limited privileges.
Do not use defaults
Azure AD assigns default privileges via built-in security groups, like Account Operators. It’s important not to use these defaults out of the box—identify if they match the roles and responsibilities in your organization and if not, customize them. Changing the defaults also helps with obfuscation because attackers are familiar with default settings.
Azure Active Directory with Pathlock
Pathlock is the leader in Access Governance for business-critical applications. Staying compliant with Sarbanes-Oxley is a critical business requirement, and Pathlock helps to automate the compliance process. As a MISA member, Pathlock can bring these capabilities to users of Azure Active Directory, with tight integration between the solutions.
Customers rely on Pathlock to streamline critical processes like fine-grained provisioning, separation of duties, and detailed user access reviews. With Pathlock’s out-of-the-box integration to Azure Active Directory, customers can enjoy the best of both worlds, including:
- Coverage for the leading business applications, with support for key applications like SAP, Oracle, Workday, Dynamics365, Salesforce, and more.
- Perform compliant provisioning at a transaction code or function level into both cloud and on-premise applications.
- Define Separation of Duties (SOD) rules, both within an application and across them, and enforce them to prevent access risks and stay compliant.
- Enrich User Access Reviews (UARs) with fine-grained entitlement details and usage about transactions performed with specific access combinations.
Interested to learn more about the winning combination of Pathlock and Azure Active Directory? Request a demo today to see the solution in action!


